Contents:
The encryption mechanism of the Zeppelin ransomware was analyzed by security researchers and, as they found vulnerabilities in it, they began to secretly exploit the flaws in order to create a working decryptor which they then used to help companies affected by ransomware to recover files without having to pay the attackers.
The developer of the decryption tool is the New Jersey based cybersecurity consulting company, Unit221b, who had a technical report ready ever since February 2020 but chose to delay its publishing, to keep the threat actor in the dark about the vulnerabilities in their file-encrypting malware.
Zeppelin Crackdown
Unit221b, in their report, claim the decision to crack Zeppelin was motivated by the fact that the ransomware operators hit charity organizations, nonprofits, and even homeless shelters.
The potentially exploitable flaws in Zeppelin were first noticed after reading an analysis of the malware from Blackberry Cylance in December 2019. Zeppelin used an ephemeral RSA-512 key to encrypt the AES key that locked access to encrypted data. The AES key was stored in the footer of each encrypted file, so if the RSA-512 key was cracked, it meant that the files could be decrypted without paying the attacker.
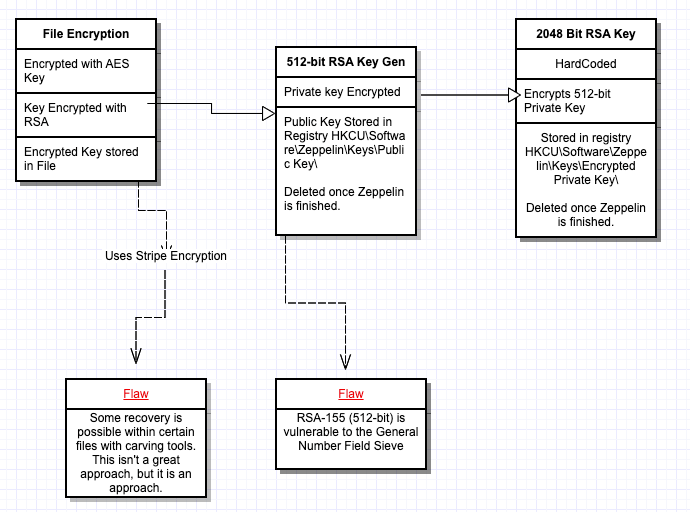
Further, Unit221b realized that this public key remained in the registry of the infected system for five minutes after the data encryption was complete.
Retrieving the key was possible by doing registry carving on the raw file system, the registry.exe memory dumps, and directly on the NTUSER.Dat in the “/User/[user_account]/” directory.
The resulting data is obfuscated with RC4, and once that layer was lifted, the researchers were left with one layer of RSA-2048 encryption. To overcome this as well, Unit221b used a total of 800 central processing units (CPUs) in 20 servers, each with 40 CPUs, that factored smaller parts of the key.
It took six hours for the key to be cracked, at which point the analysts could work their way back to retrieve the AES key from the file footer.
Decryptor Made Available
In a statement for BleepingComputer, Unit221b’s founder Lance James claims they decided to make all details public due to the Zeppelin ransomware victim influx dropping significantly in the recent months. The decryption tool is now available upon request, and it should work on recent Zeppelin versions as well.
In addition, threat analyst Brett Callow from Emsisoft also confirmed the drop in Zeppelin attacks and noted that data recovery experts have been exploiting Zeppelin’s encryption vulnerability since mid-2020.
Further Context on Zeppelin
Zeppelin, aka Buran, is a Delphi-based ransomware strain of Russian origin, first spotted in November 2019 as a semi-private project operating in small-circle partnerships. The ransomware project extorted victims for an average of $50,000 and featured a robust AES-256-CBC encryption.
Operators behind the Zeppelin Ransomware-as-a-Service (RaaS) sell their new version on clandestine forums, allowing customers to choose how they want to employ the virus. Unlike other RaaS campaigns the developers seek affiliates to attack a network, steal data and install the file-encrypting virus. The operators and their partners then split the ransom payment.
More recently, in August 2022, the FBI posted an alert about Zeppelin ransomware, warning that its operators were now following the tactic of performing multiple encryptions on the breached systems.
This tactic created multiple victim IDs and files with multiple encryption layers, requiring several decryption keys and a lot of trial and error to restore the data even after the ransom has been paid.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









