Contents:
A Trojan is a type of malware that acts according to the Greek legend, as it camouflages itself as a legitimate file or program to trick unsuspecting users into installing it on their PCs.
This is how unsuspecting users will give unauthorized remote access to cyber attackers. The threat actors will now be able to spy on a user’s activity (web browsing, computer activity, etc.), in order to collect and harvest sensitive data, delete files, or download more malware onto the PC, and more.
The threat actors are becoming more innovative as they started to use YouTube videos as a way to distribute malware through embedded links in video descriptions.
Security researcher Frost from Cluster25 disclosed for BleepingComputer that he noticed a significant rise in malware campaigns on YouTube pushing various password-stealing Trojans.
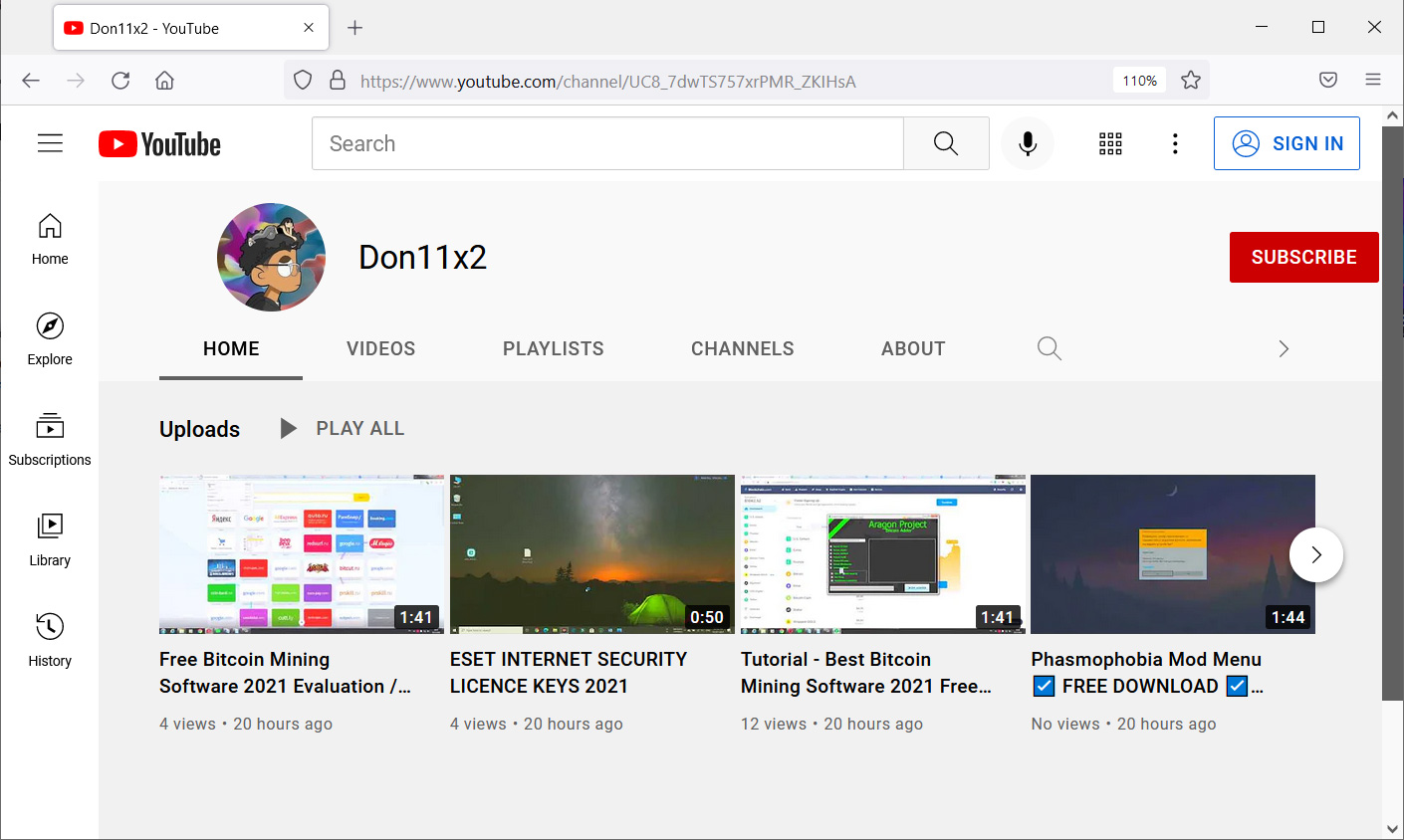
It seems that at this time we’re dealing with two clusters of malicious activity both conducted simultaneously – one pushing the RedLine malware and the other pushing Racoon Stealer.
Thousands of videos and channels were generated as part of the huge virus effort, according to the researcher, with 100 new videos and 81 channels formed in just twenty minutes.
Frost stated that the threat actors utilize the stolen Google accounts to establish new YouTube channels to disseminate malware, creating an endless and ever-growing loop.
The threat actors have thousands of new channels available because they infect new clients every day. As part of these attacks, they steal victim’s Google credentials, which are then used to create new YouTube Videos to distribute the malware.
What Is the Attack M.O.?
The assaults begin with malicious actors launching dozens of new YouTube channels dedicated to software cracks, licenses, how-to instructions, bitcoin, mining, game hacks, VPN software, and just about every other popular topic.
These videos provide instructions on how to do a job using specific software or tool. In addition, the YouTube video’s description claims to provide a link to the related program that was used to spread the virus.
A bit.ly link in a movie will take you to another file-sharing site where the RedLine password-stealing malware infection is hosted. If it contains an unshortened domain, however, it will redirect to a page on the taplink[.]cc domain, as seen below, to push Racoon Stealer.
Once a user has been infected, the malware will search all installed browsers as well as the machine for cryptocurrency wallets, credit cards, passwords, and other sensitive information before sending it back to the attacker.
Google said that they know about the malicious campaign and are taking action to disrupt the activity.
We are aware of this campaign and are currently taking action to block activity by this threat actor and flagging all links to Safe Browsing. As always, we are continuously improving our detection methods and investing in new tools and features that automatically identify and stop threats like this one. It is also important that users remain aware of these types of threats and take appropriate action to further protect themselves.
This is not the only situation that puts YouTube users in danger.
As my colleague Antonia explained, security experts from Google’s Threat Analysis Group (TAG) noticed the fact that YouTube creators have been targeted with “highly customized” phishing emails and cookie-stealing malware.
In order to infect YouTubes with information-stealing malware, the attackers used social engineering tactics (through bogus software landing pages and social media pages) and phishing emails.
How to Stay Safe?
These efforts demonstrate the need not to download programs from the Internet at random, as video producers cannot check every link posted to sites like YouTube.
As a result, before downloading and installing anything from a website, you should investigate it to see whether it has a solid reputation and can be trusted. Even so, it’s always a good idea to submit the application to a site like VirusTotal first to make sure it’s safe to execute.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








