Contents:
According to Google, YouTube influencers have been targeted with password-stealing malware in a phishing campaign allegedly conducted by Russian-speaking cybercriminals.
Security experts with Google’s Threat Analysis Group (TAG), who first noticed the operation in late 2019, say that the company had disrupted phishing campaigns ever since. According to them, the YouTube creators have been targeted with “highly customized” phishing emails and cookie-stealing malware.
In order to infect YouTubes with information-stealing malware, the attackers used social engineering tactics (through bogus software landing pages and social media pages) and phishing emails.
As mentioned by BleepingComputer, the hackers use a variety of infections, with many of them publicly available on Github. Some of them included RedLine, Vidar, Predator The Thief, Nexus Stealer, Azorult, Raccoon, Grand Stealer, Vikro Stealer, Masad, and Kantal, as well as open-source malware like AdamantiumThief and Sorano.
Once installed on the victim’s network, the malware was employed to steal their login info and browser cookies, enabling the hackers to hijack their accounts through pass-the-cookie techniques.
Ashley Shen, a TAG Security Engineer, declared:
While the technique has been around for decades, its resurgence as a top security risk could be due to a wider adoption of multi-factor authentication (MFA) making it difficult to conduct abuse, and shifting attacker focus to social engineering tactics.
Most of the observed malware was capable of stealing both user passwords and cookies. Some of the samples employed several anti-sandboxing techniques including enlarged files, encrypted archive and download IP cloaking.
Session Hijacking Explained
As explained in this article, session hijacking stands for a cyberattack where a malicious hacker places himself in between your computer and the website’s server while you are engaged in an active computer session in order to steal it.
The hacker actively monitors everything that happens on your account, and can even kick you out and take control of it. It is often called cookie hijacking or cookie side-jacking because the hacker gains knowledge of your session cookie giving him access to the session ID that lets him impersonate the user and perform actions on his behalf: transferring your money to his account for instance.
At least 1,011 domains have been tied to these attacks, with about 15,000 accounts opened especially for this operation. These accounts were used to send phishing emails (that included links redirecting to pages containing malware) to business emails belonging to YouTube influencers.
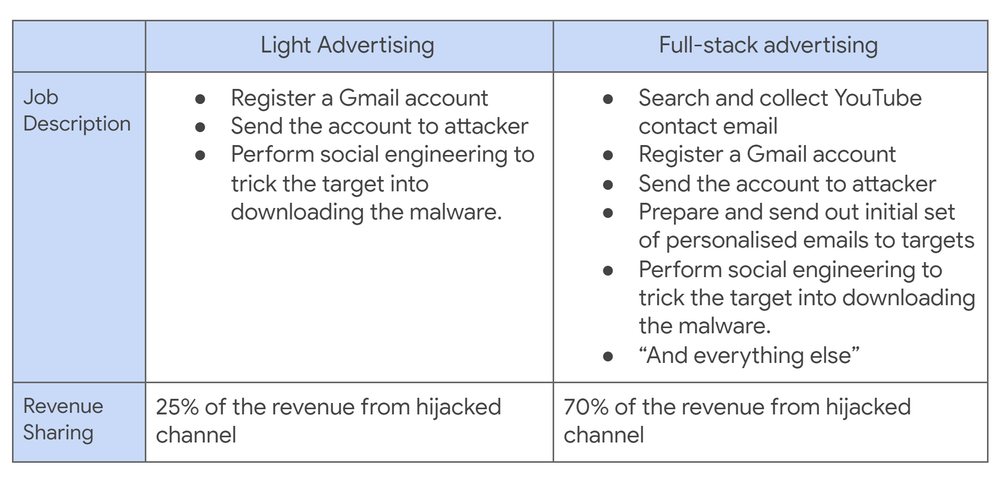
According to BleepingComputer, many of the YouTube channels that were hijacked in these attacks were sold on underground markets.
Ashley Shen stated that since May 2021, Google’s Threat Analysis Group reduced phishing emails associated with these attacks on Gmail by 99.6 %.
We blocked 1.6M messages to targets, displayed ~62K Safe Browsing phishing page warnings, blocked 2.4K files, and successfully restored ~4K accounts.
With increased detection efforts, we’ve observed attackers shifting away from Gmail to other email providers (mostly email.cz, seznam.cz, post.cz and aol.com).
Google also notified the FBI about the operation in order to protect the YouTube creators who were affected by this attack.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










