Contents:
More than 50,000 Android devices have been infected with a new banking trojan called Xenomorph, which was spread via Google Play Store in order to steal financial information.
Users of dozens of banks in Spain, Portugal, Italy, and Belgium are being targeted by the new malware, which is still in the early stages of development.
More on the Xenomorph Malware
Researchers at ThreatFabric, an organization that provides banks with the expertise and tools to detect known and unknown threats to reduce fraud and deflect risk, analyzed the Xenomorph malware and discovered code that is similar to Alien banking trojan.
This indicates that the two viruses are linked in some way: either Xenomorph is Alien’s successor, or both have been developed by the same person.
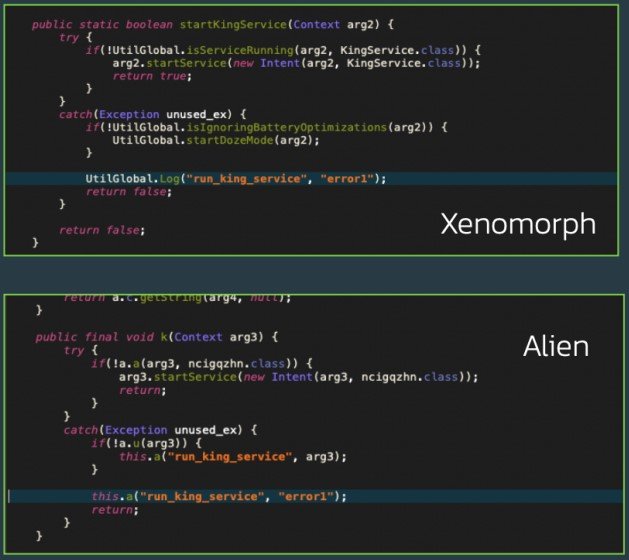
Banking trojans like Xenomorph are designed to steal sensitive banking details, take control of accounts, and initiate unauthorized transactions, with the stolen data being sold to prospective buyers.
How Did It Happen?
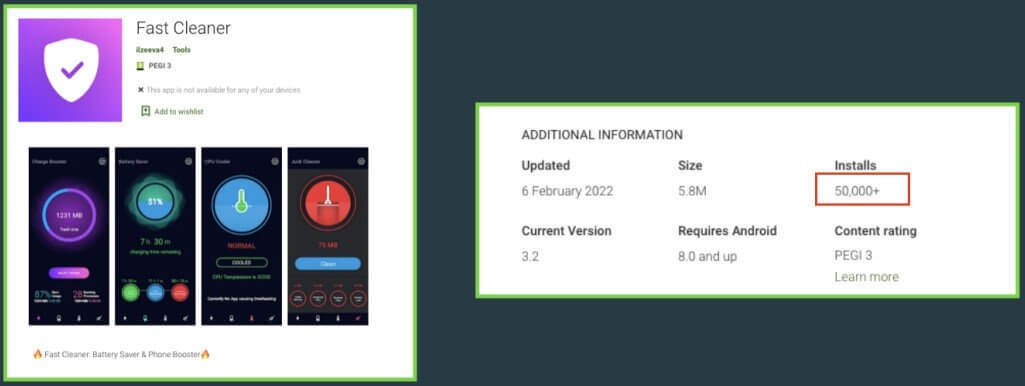
The Xenomorph trojan got into the Google Play Store through generic performance-boosting apps like “Fast Cleaner,” which has 50,000 installations.
Banking trojans, including Alien, use such utilities, which are classic enticement as users are always interested in tools that promise to boost the performance of their Android smartphones.
To avoid rejection during the Play Store application review, Fast Cleaner fetches the payload following the installation, ensuring that the app is clean at the time of submission.
What Can Xenomorph Malware Do?
Xenomorph’s functionality isn’t complete yet because the trojan is still under development. Nevertheless, it remains a significant threat because it is capable of stealing private information and targets no less than 56 different financial institutions from Europe.
As explained by BleepingComputer, the banking trojan can intercept notifications, log text messages, and use injections to conduct overlay attacks, so it can already steal logins and one-time passwords used to protect banking accounts.
The app’s first move following the installation is to send back a list of the installed packages on the compromised device so that the suitable overlays can be loaded.
To accomplish this, the malware asks for Accessibility Service permissions on installation and then uses those privileges to grant itself further permissions as needed.
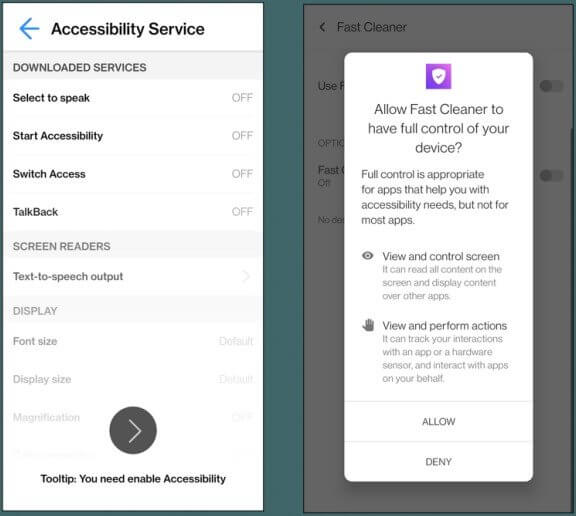
Keylogging functions and behavioral data collection are two examples of commands that are existent in the code but have not yet been implemented.
Its Accessibility Engine is very detailed, and is designed with a modular approach in mind. It contains modules for each specific action required by the bot, and can be easily extended to support more functionalities. It would be unsurprising to see this bot sport semi-ATS capabilities in the very near future.
Due to its “under development” status, ThreatFabric believes Xenomorph is not a significant threat at this time. However, it has the potential to become “comparable to other modern Android Banking trojans” over time.
In order to avoid falling victims to Android malware skulking in the Play Store, users are recommended to stay away from applications that seem too good to be true. Sometimes, checking the reviews of other people can help avoid malicious apps.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








