Contents:
As modern threats surpass traditional security measures, XDR software steps in as a revolutionary solution. A software that empowers CISOs to proactively navigate the evolving threat landscape.
Understanding the Challenge
CISOs face a daunting task. The traditional siloed approach to security—where various tools are used to monitor specific areas—falls short in the face of coordinated and multifaceted attacks. The lack of holistic visibility, coupled with alert fatigue, significantly hinders incident response capabilities.
Enter XDR: A Game-Changing Solution
XDR offers a holistic and integrated approach to cybersecurity. By collecting and correlating data from multiple sources, XDR provides comprehensive visibility into the entire attack surface. This empowers CISOs with actionable insights and enables them to detect, investigate, and respond to threats in real time.
Key Benefits of XDR for CISOs
- Centralized Visibility: XDR aggregates data from various sources into a centralized platform, eliminating blind spots and providing a unified view of the entire IT environment.
- Advanced Threat Detection: By employing AI and machine learning algorithms, XDR can detect anomalies and suspicious activities across the organization, even those that may go unnoticed by traditional security tools.
- Real-time Response: XDR enables rapid incident response by automating the analysis of threats and suggesting appropriate mitigation actions. This reduces the mean time to detect and respond to incidents.
- Reduced Alert Fatigue: XDR’s advanced analytics and correlation capabilities mean that CISOs are presented with fewer alerts. This makes life easier for your IT managers and your teams.
- Proactive Threat Hunting: XDR empowers CISOs to adopt a proactive stance by hunting for potential threats before they escalate into full-blown attacks. This approach helps your security teams stay ahead of threat actors.
- Cloud Security: As organizations embrace cloud services, securing cloud environments becomes paramount. XDR extends its coverage to cloud platforms, ensuring consistent security across all fronts.
Read our article on How to Choose the Best XDR Solution for Your Organization for a comprehensive view on choosing the right solution for your company.
Making the Shift: Implementing XDR
Transitioning to XDR requires careful planning and execution.
Here’s a step-by-step guide to help CISOs make the most of this transformative technology:
- Assessment: Evaluate your organization’s current security posture and identify gaps that XDR could address. Understand your specific security needs and priorities.
- Vendor Evaluation: Research and choose an XDR solution that aligns with your organization’s requirements. Look for features such as ease of deployment, scalability, and integration capabilities.
- Integration: Ensure a smooth integration of XDR with your existing security infrastructure. Collaborate with your IT team to set up data feeds and configure the system according to your needs.
- Training: Provide training to your security team to maximize the benefits of XDR. Familiarize them with the platform’s features, dashboards, and reporting capabilities.
- Testing: Conduct thorough testing to validate the effectiveness of the XDR solution in your environment. Fine-tune configurations based on initial results.
- Deployment: Deploy the XDR solution across your organization’s IT landscape. Monitor its performance closely during the initial stages.
- Continuous Improvement: Regularly review and update your XDR strategy to adapt to evolving threats and organizational changes. Leverage feedback from your security team to optimize the system’s performance.
Heimdal®’s XDR
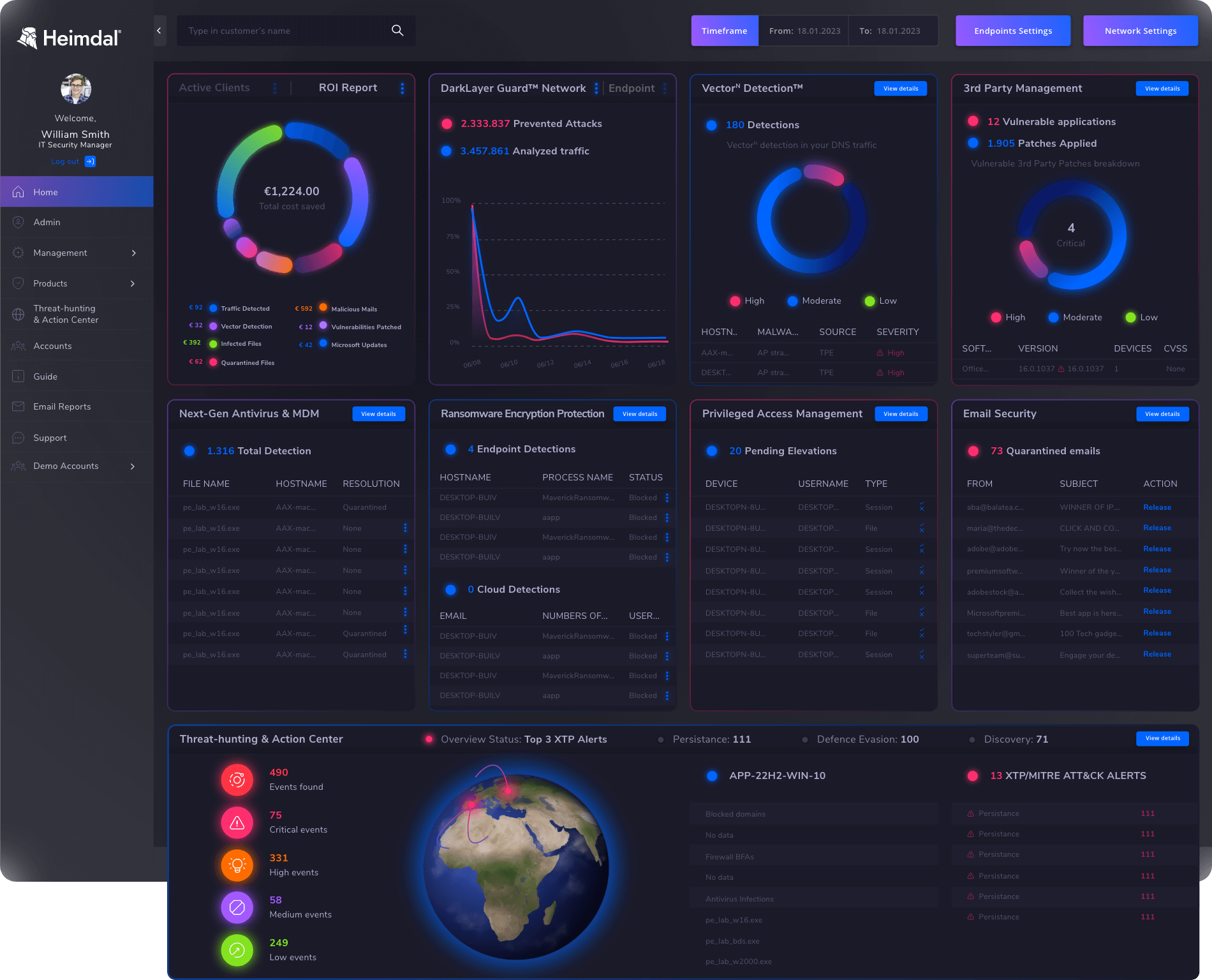
With Extended Detection and Response. XDR Solution by Heimdal, it’s not just about software – it’s about embracing a comprehensive partnership that prioritizes your security needs.
Our XDR solution empowers you with unparalleled threat detection, automated responses, and a unified security platform, all designed to simplify your security operations. Step into a new era of cybersecurity with Heimdal and experience security that transcends the ordinary.
With a lineup of over 10 fully integrated security solutions, our approach spans your entire IT estate, enabling proactive and compliant measures whether your operations are remote or on-site.
Top-notch Features of Heimdal®’s XDR
- Unified Security Platform: Consolidate all your security tools into a single, easy-to-navigate interface, providing you with a clear and holistic perspective of your security landscape.
- Smart Threat Detection: Powered by advanced AI and ML technologies, our XDR software excels at detecting threats with remarkable speed and intelligence, ensuring you stay ahead of potential risks.
- Automated Response: Heimdal XDR doesn’t just identify threats; it acts upon them automatically, swiftly neutralizing dangers before they escalate.
- Cost-Effective Solution: By integrating a diverse range of security technologies, Heimdal’s XDR offers an efficient way to save costs while fortifying your defenses.
- Simplified Management: Bid farewell to the complexities of managing multiple security solutions. With Heimdal’s XDR, all your security needs are seamlessly handled within one unified platform.
- Expert Support: Our dedicated team of experts stands ready to support you, offering insights and assistance whenever you need it.
- User-Friendly: Engineered with ease of use in mind, Heimdal’s XDR is designed to be intuitive, even for those who aren’t tech experts.

- End-to-end consolidated cybersecurity;
- Complete visibility across your entire IT infrastructure;
- Faster and more accurate threat detection and response;
- Efficient one-click automated and assisted actioning
Equip your organization with the cutting-edge protection it deserves. Embrace our XDR software today and stay one step ahead of cyber threats. Get in touch with our experts to learn how XDR can transform your security posture. Safeguard your digital future—act now!
In Conclusion – Embrace the Future of Cybersecurity
In an era where cyber threats continue to evolve, CISOs need advanced tools that can keep pace with the changing landscape. XDR offers a comprehensive and proactive approach to cybersecurity, enabling CISOs to protect their organizations from a wide range of threats. By harnessing the power of integrated data, advanced analytics, and real-time response capabilities, CISOs can confidently navigate the complexities of modern cybersecurity challenges.
XDR FAQs
1. What exactly is XDR?
XDR stands for Extended Detection and Response. It’s a cybersecurity solution that offers a comprehensive and integrated approach to threat detection, investigation, and response. Unlike traditional security tools that focus on specific areas, XDR correlates data from various sources to provide a unified view of the organization’s attack surface.
2. How does XDR enhance threat detection?
XDR employs advanced analytics and machine learning algorithms to identify anomalies and suspicious activities across the IT environment. By analyzing data from endpoints, networks, cloud services, and more, XDR can detect even the most sophisticated threats that might evade conventional security measures.
3. Can XDR help reduce alert fatigue?
Absolutely. XDR’s correlation capabilities and AI-driven analytics result in fewer, high-fidelity alerts. This significantly reduces alert fatigue by presenting CISOs with actionable insights. As a result, they are able to focus on critical threats instead of sifting through numerous false positives.
4. Is XDR only for on-premises environments?
No, XDR’s reach extends beyond on-premises environments. It covers endpoints, networks, and cloud services, ensuring consistent security across all fronts. This is particularly beneficial as organizations increasingly embrace cloud technologies.
5. How does XDR enable proactive threat hunting?
XDR empowers CISOs to take a proactive stance by enabling threat hunting. With access to comprehensive and correlated data, security teams can identify potential threats before they escalate into significant security incidents. This approach helps organizations stay ahead of threat actors and minimize potential damage.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security