Contents:
Threat actors are distributing instructions and exploits for the Windows MSHTML zero-day (CVE-2021-40444) vulnerability on hacking forums, allowing other hackers to use the new vulnerability in their own assaults.
Microsoft reported a new zero-day vulnerability in Windows MSHTML that allows attackers to produce malicious documents, such as Office and RTF documents that may be used to remotely execute commands on a victim’s machine.
Despite the fact that there are no security patches available yet for the CVE-2021-40444 vulnerability, Microsoft chose to expose it and give mitigations to assist prevent its exploitation when EXPMON and Mandiant determined it was being exploited in active attacks.
ActiveX components and Word/RTF document previews in Windows Explorer are blocked by these mitigations. Researchers were able to alter the exploit so that it no longer uses ActiveX, therefore bypassing Microsoft’s mitigations.
Guides Shared on Hacking Forums
When Microsoft disclosed the Windows MSHTML zero-day, also known as CVE-2021-40444, security researchers quickly found the malicious documents used in attacks.
As the researchers reproduced the exploits, they modified them for further capabilities, and discovered a new document preview vector, but did not disclose details fearing the fact that other threat actors would abuse the vulnerability.
Inspired by @buffaloverflow, I tested out the RTF attack vector. And it works quite nicely.
WHERE IS YOUR PROTECTED MODE NOW? pic.twitter.com/qf021VYO2R— Will Dormann (@wdormann) September 9, 2021
Not sure if Microsoft fixed this (my VM is unpatched). But it works in explorer preview mode via RTF: https://t.co/GI9xr71JKt pic.twitter.com/H5cdmL8tpX
— Rich Warren (@buffaloverflow) September 8, 2021
Unfortunately, the malicious actors managed to reproduce the exploit on their own by using just the information and malicious document samples posted online.
According to BleepingComputer, the threat actors started to share public information about the HTML component of the exploit as well as instructions related to the way in which the malicious document can be created.
The information shared online is quite simple to follow, therefore allowing anyone to create a working version of the CVE-2021-40444 exploit.
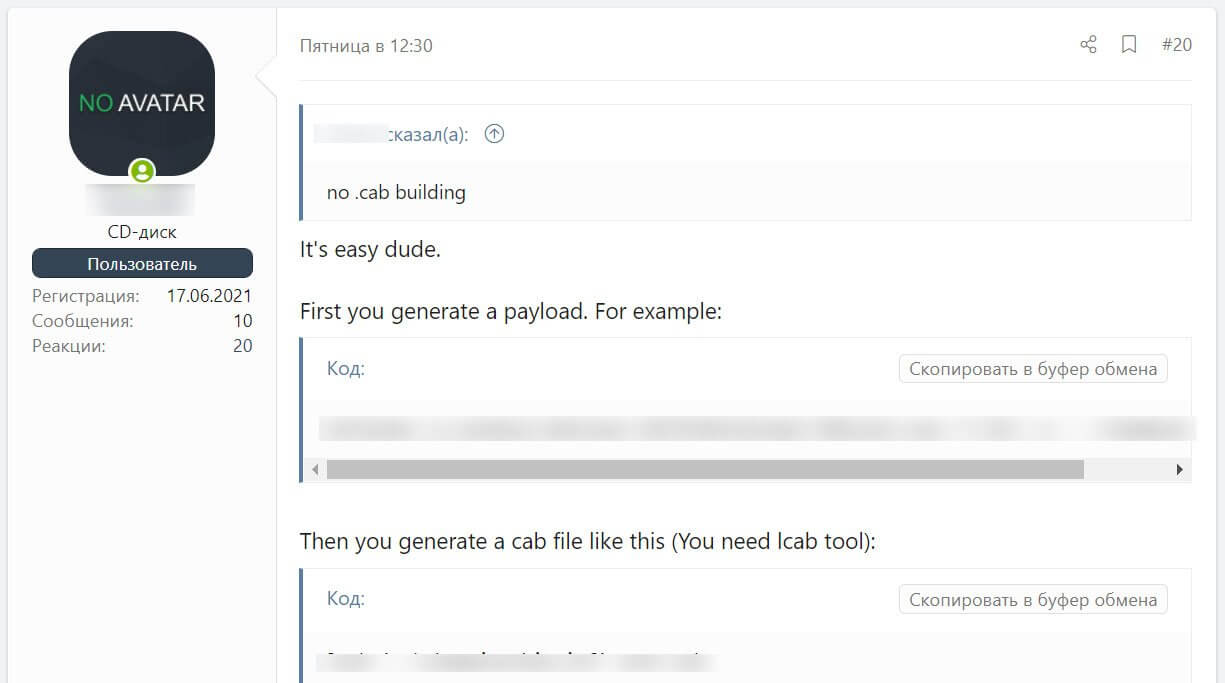
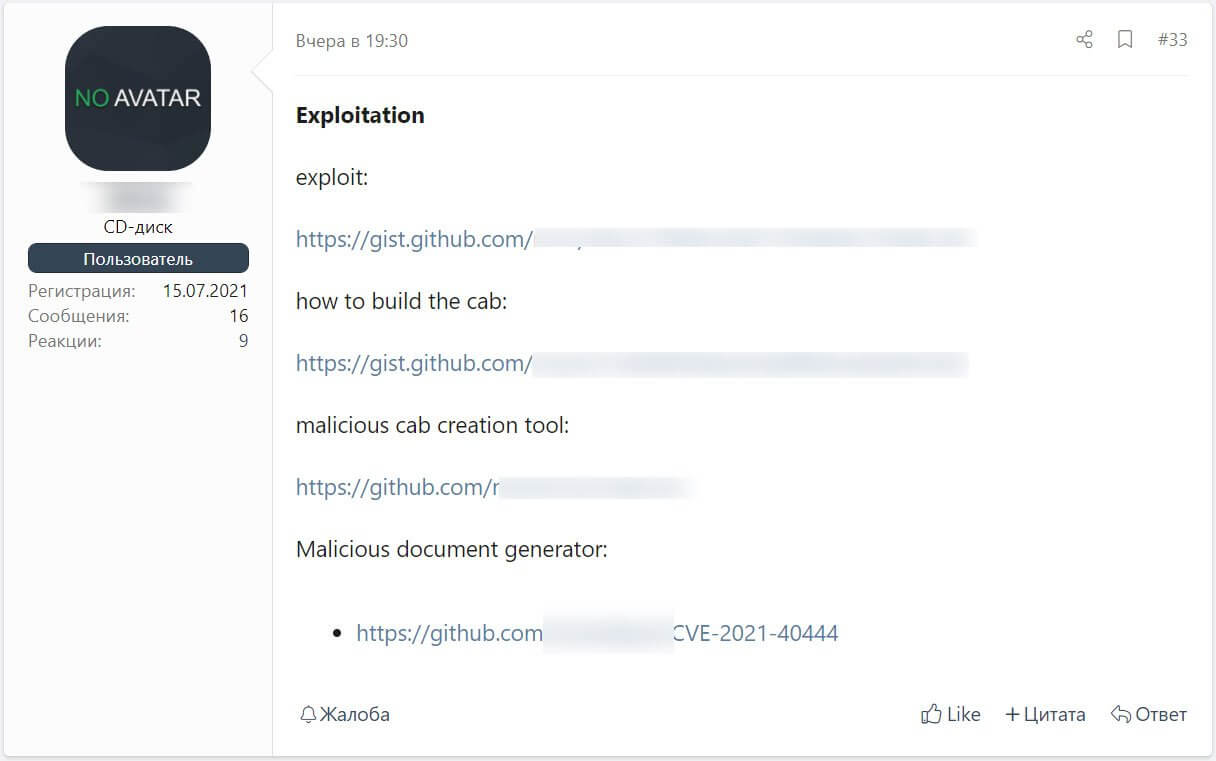
Fortunately, it seems that since the vulnerability was disclosed, Microsoft Defender and other security programs were able to detect and block the malicious documents and CAB files used in this attack.
It’s also worth noting that Microsoft has developed mitigations to prevent ActiveX controls in Internet Explorer, the MSHTML protocol’s default handler, and to block page preview in Windows Explorer.
While these mitigations will assist, users are still in danger until an official security patch is published.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








