Contents:
The Terrapin attack, a newly identified security threat, jeopardizes nearly 11 million SSH servers that are accessible online.
Originating from academic research at Ruhr University Bochum in Germany, this attack specifically targets the SSH protocol, affecting both clients and servers.
It exploits vulnerabilities during the handshake process, especially when using certain encryption modes, compromising the integrity of SSH connections.
Mechanism and impact
The attack requires the perpetrator to be in a unique position – an adversary-in-the-middle (AitM) – to intercept and manipulate the handshake exchange.
This method enables attackers to downgrade public key algorithms for user authentication and neutralize protections against keystroke timing attacks, notably in OpenSSH 9.5.
The report by Shadowserver, a security monitoring platform, highlights the widespread vulnerability of these servers across the globe.
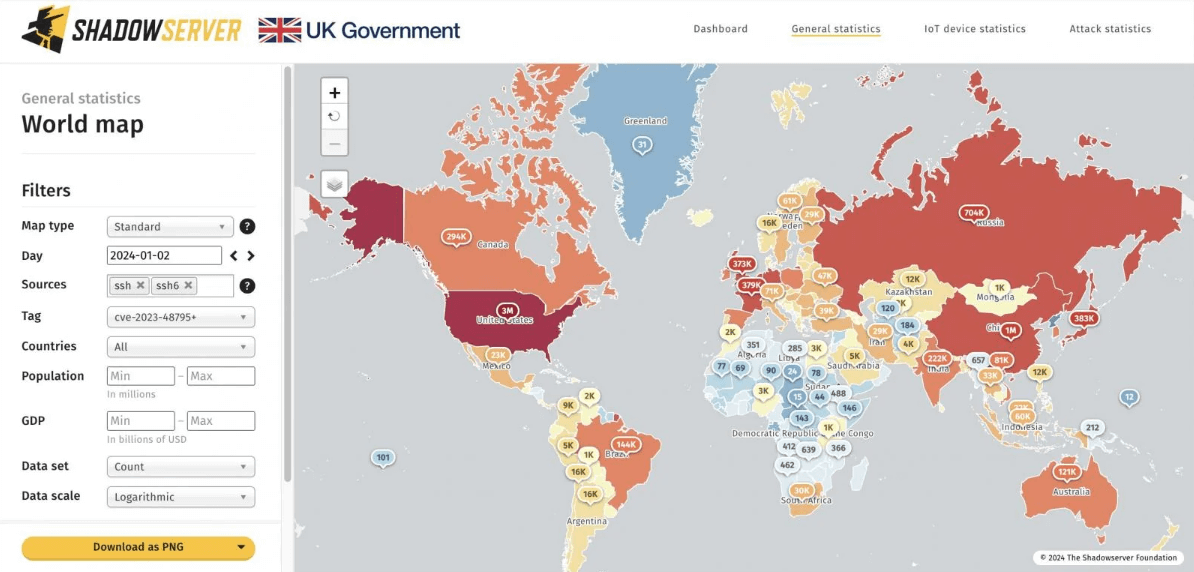
Map of vulnerable SSH servers (Source)
Geographical distribution and significance
Shadowserver’s findings show that the United States has the highest number of vulnerable servers (3.3 million), followed by China (1.3 million), Germany (1 million), Russia (700,000), Singapore (390,000), and Japan (380,000).
This distribution underlines the potential widespread impact of Terrapin attacks. Although not every one of the 11 million servers is at immediate risk, it reveals a significant pool of targets for potential attackers.
For those concerned about the vulnerability of their SSH client or server, the team from Ruhr University Bochum offers a specialized vulnerability scanner (Github).
If you’re interested in reading more about vulnerability management, check out this article: What Is Vulnerability Management [Everything You Need to Know].
And if you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








