Contents:
Analyzing how ransomware operators choose their targets makes it possible to better understand the types of companies these threat actors have on their list. In this regard, Victoria Kivilevich, Threat Intelligence Analyst at KELA has released a profile of an ideal ransomware victim based on valuable criteria for cyber attackers buying access.
Key Findings
According to Kivilevich, 48 active threads were found in July 2021 where actors claimed they are looking to buy various types of accesses. Of them, 46% were created that month, pointing out the demand for access listings.
What’s more, 40% of the actors who were looking to buy accesses were operators, affiliates, or middlemen in the ransomware-as-a-service (RaaS) supply chain.
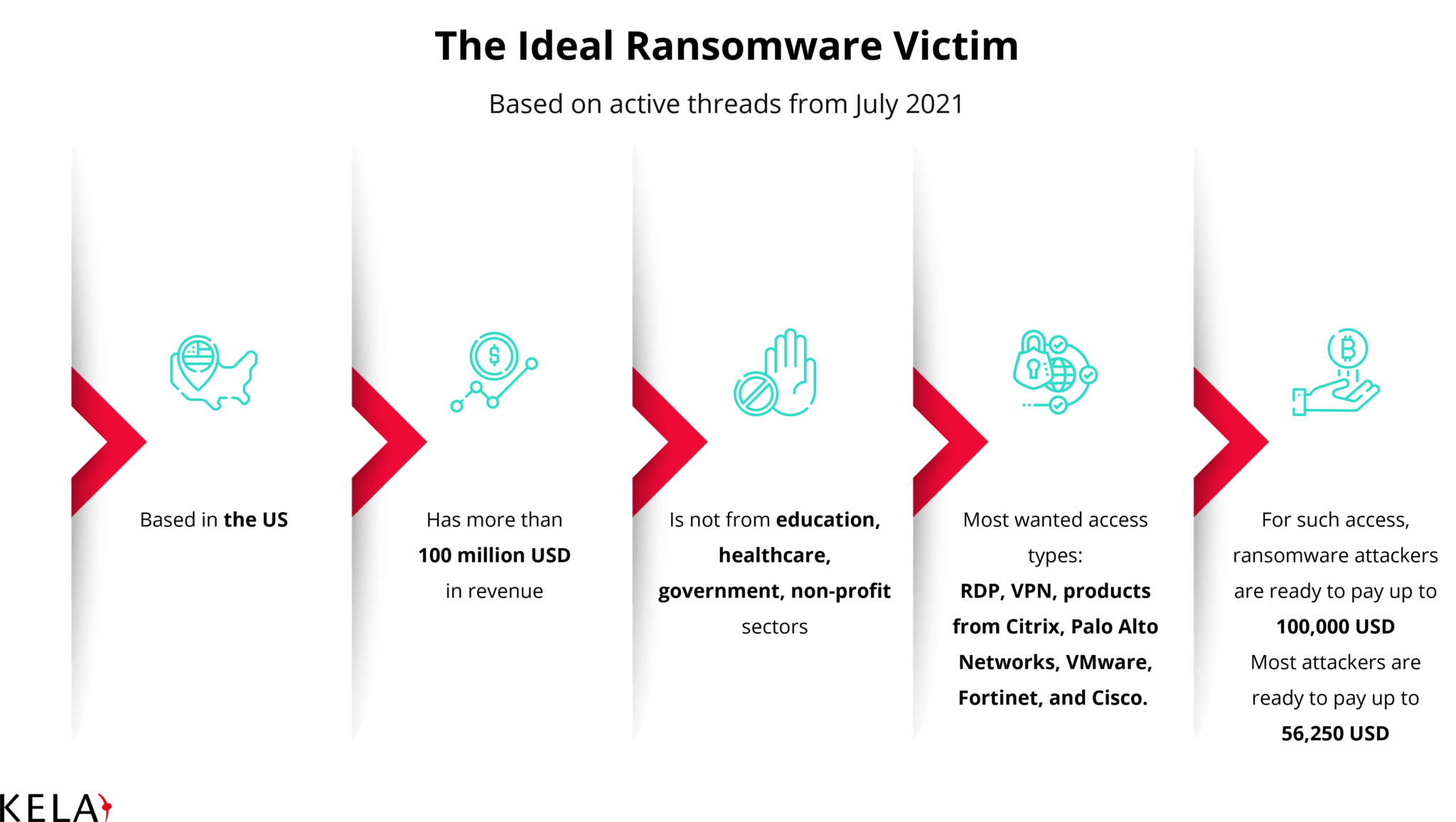
When it comes to “industry standards”, defining the ideal victim of ransomware attackers depends on its revenue and geography. Additionally, excluding certain sectors and countries from the targets list also comes in handy. On average, the threat actors that were active in July 2021 intended to buy access to US companies with over $100 million in revenue. What’s interesting is that almost half of them refused to buy access to healthcare and education companies.
RDP and VPN are the most basic requirements when it comes to buying all kinds of network access. The most common products mentioned were Citrix, Palo Alto Networks, VMware, Fortinet, and Cisco.
Finally, ransomware operators are prepared to pay up to $100,000 for access, with the majority of them setting the limit at half of that price.
The similarities between ransomware-related actors’ requirements for victims and access listings and conditions for IABs illustrate that RaaS operations act just like corporate enterprises.
By analyzing the want ads from nearly 20 posts created by threat actors related to ransomware gangs, the researcher was able to conclude that a typical ransomware actors’ advertisement includes the following characteristics of the victim:
Geography
The reason behind this geographical focus is that attackers choose the wealthiest companies which are expected to be located in the biggest and the most developed countries.
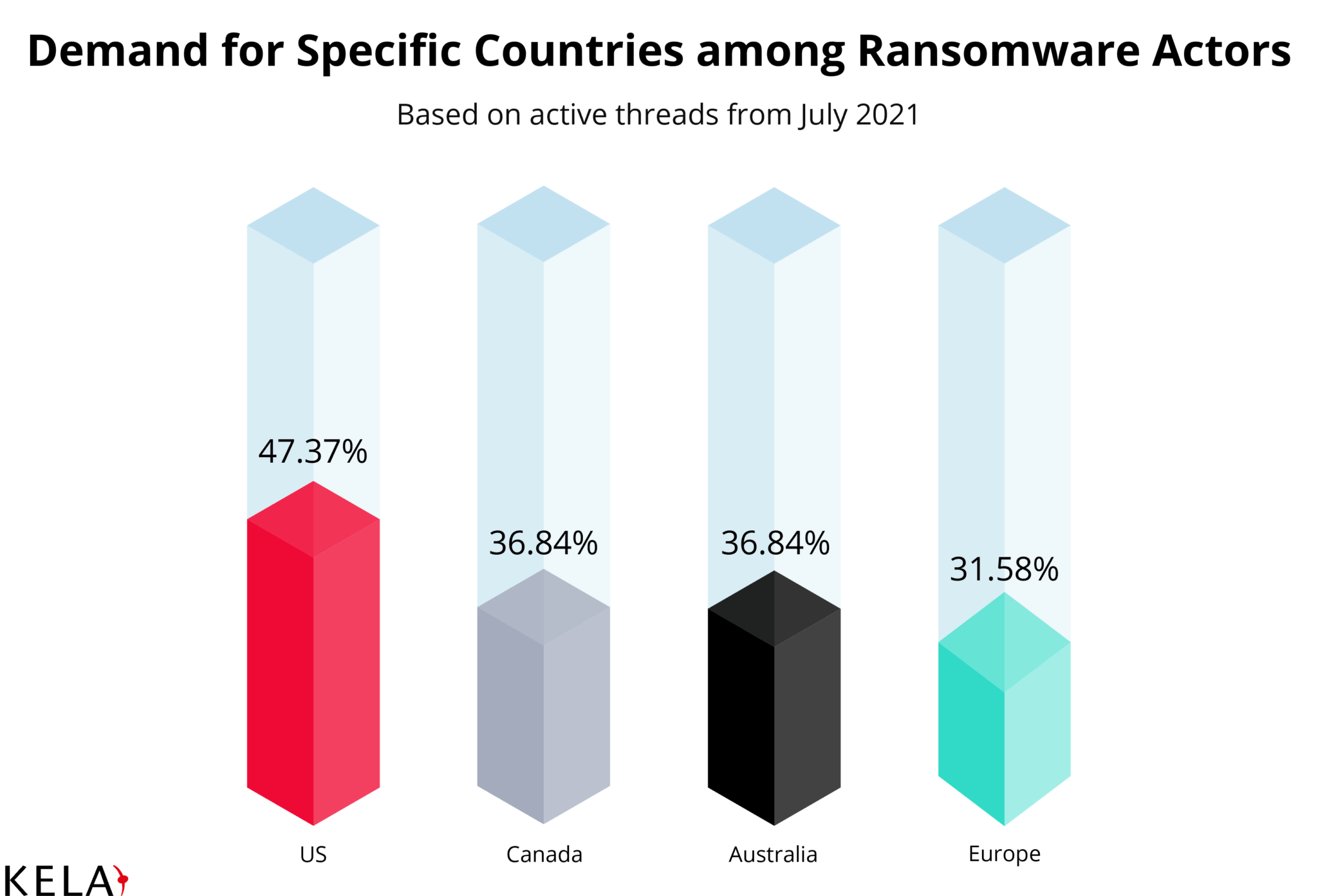
The majority of requests mentioned the desired location of victims, with the US being the most popular choice – 47% of the actors mentioned it. Other top locations included Canada (37%), Australia (37%), and European countries (31%).
Revenue
In general, the attackers stated only the minimum desired revenue in attempts to cut off victims that are unlikely to pay a significant ransom.
The average minimum revenue wanted by ransomware attackers is 100 million USD, with some of them stating that the desired revenue depends on the location. For example, one of the actors described the following formula: revenue should be more than 5 million USD for US victims, more than 20 million USD for European victims, and more than 40 million USD for “the third world” countries.
Blacklist of sectors
Kivilevich has spotted a significant difference between the ad of threat actors buying access for ransomware attacks and cybercriminals with other specializations. Almost a half of ransomware-related threads included a blacklist of sectors, and after the Colonial Pipeline, Metropolitan Police Department, and JBS attacks, many ransomware gangs are not ready to buy access to companies from specific industries.
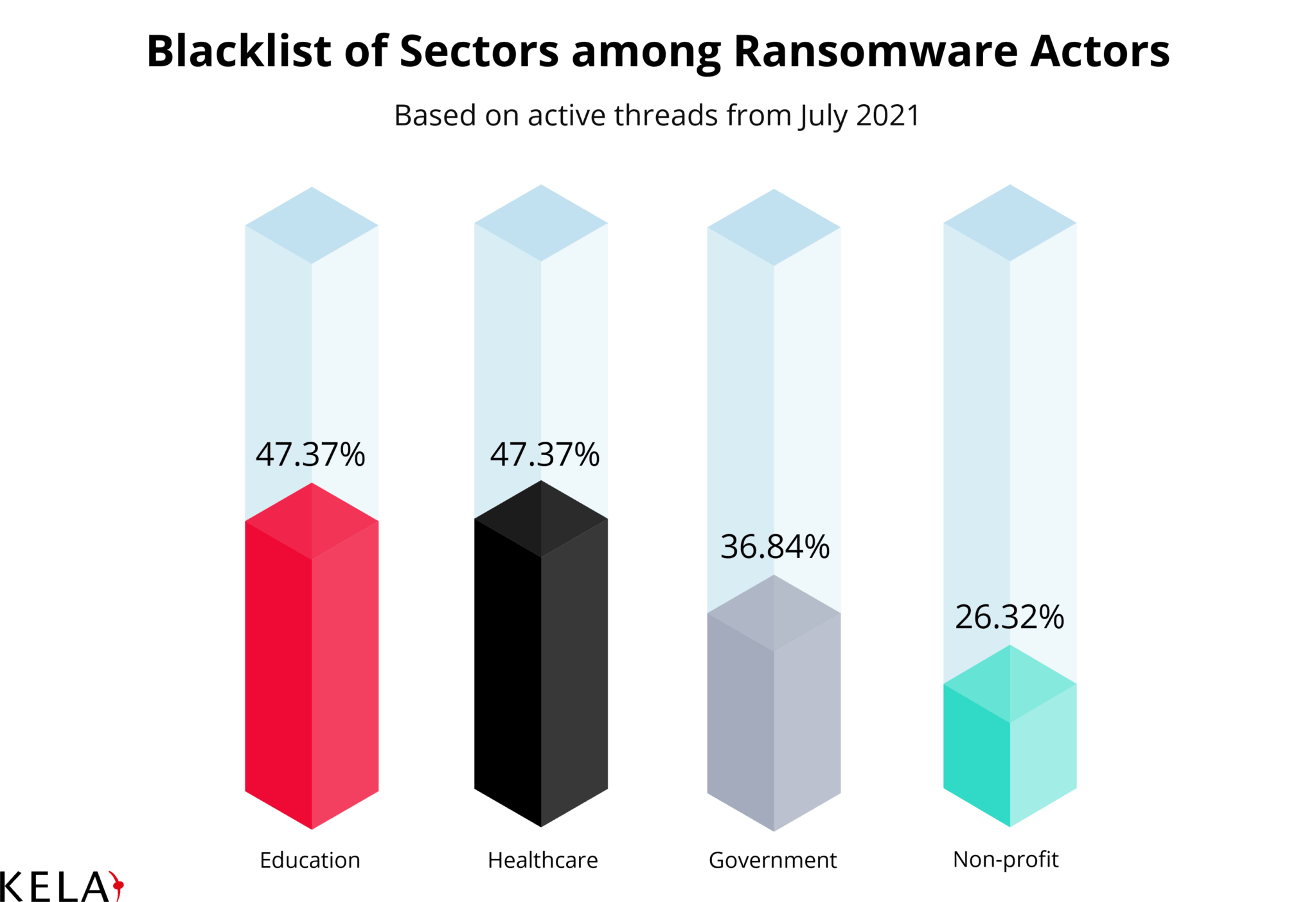
47% of ransomware attackers refused to buy access to companies from the healthcare and education industries. 37% prohibited compromising the government sector, while 26% claimed they will not purchase access related to non-profit organizations.
Blacklist of countries
Last but not least, certain countries are out of ransomware operators’ interests. Mainly CIS (Commonwealth of Independent States), according to the old Russian-speaking hackers’ rule “do not work in Ru”.
Attackers operating in CIS assume that if they won’t target these countries, local authorities will not go after them. Other countries mentioned as “unwanted” included South America and third world countries – most likely due to low chances of getting a financial gain.
It should be reminded that even though most ransomware gangs prefer victims with these characteristics, it does not necessarily mean they won’t breach a network independently. Access to a company in the wrong hands may be exploited not only for deploying ransomware and stealing data but also for other malicious campaigns.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








