Contents:
Cybersecurity specialists have discovered a new malware that affects Android phones. The new Android trojan dubbed GriftHorse was spread via the Google Play store as well as some third-party app stores and infected more than 10 million devices all over the world.
According to experts at Zimperium zLabs, the hackers behind this sophisticated malware distribution campaign probably made tons of money by subscribing unaware Android users to premium services.
They explained that the GriftHorse operation has been functional since at least November 2020 and through April 2021.
The malware has been planted in over 200 Android applications that have been approved for distribution on the Google Play store and other third-party app stores.
Zimperium has reached out to Google and notified them about the incident, after which the malware-related applications were immediately removed from the Play Store. Unfortunately, they can still be downloaded from third-party apps.
The researchers estimated that GriftHorse developers are currently making somewhere between $ 1.5 to $ 4 million every month by using this method.
GriftHorse Campaign Made Victims All Over the World
The GriftHorse trojan has been used by the threat actors in order to infect their targets and unknowingly subscribe them to paid services, making hundreds of millions due to this malicious campaign.
As mentioned by BleepingComputer, the majority of anti-malware solutions didn’t detect the infected applications and went noticed for roughly five months while the GriftHorse campaign was operative.
The specialists stated that 200 apps across multiple categories have been used to spread GriftHorse malware to over 10 million victims in more than 70 countries.
How Does It Work?
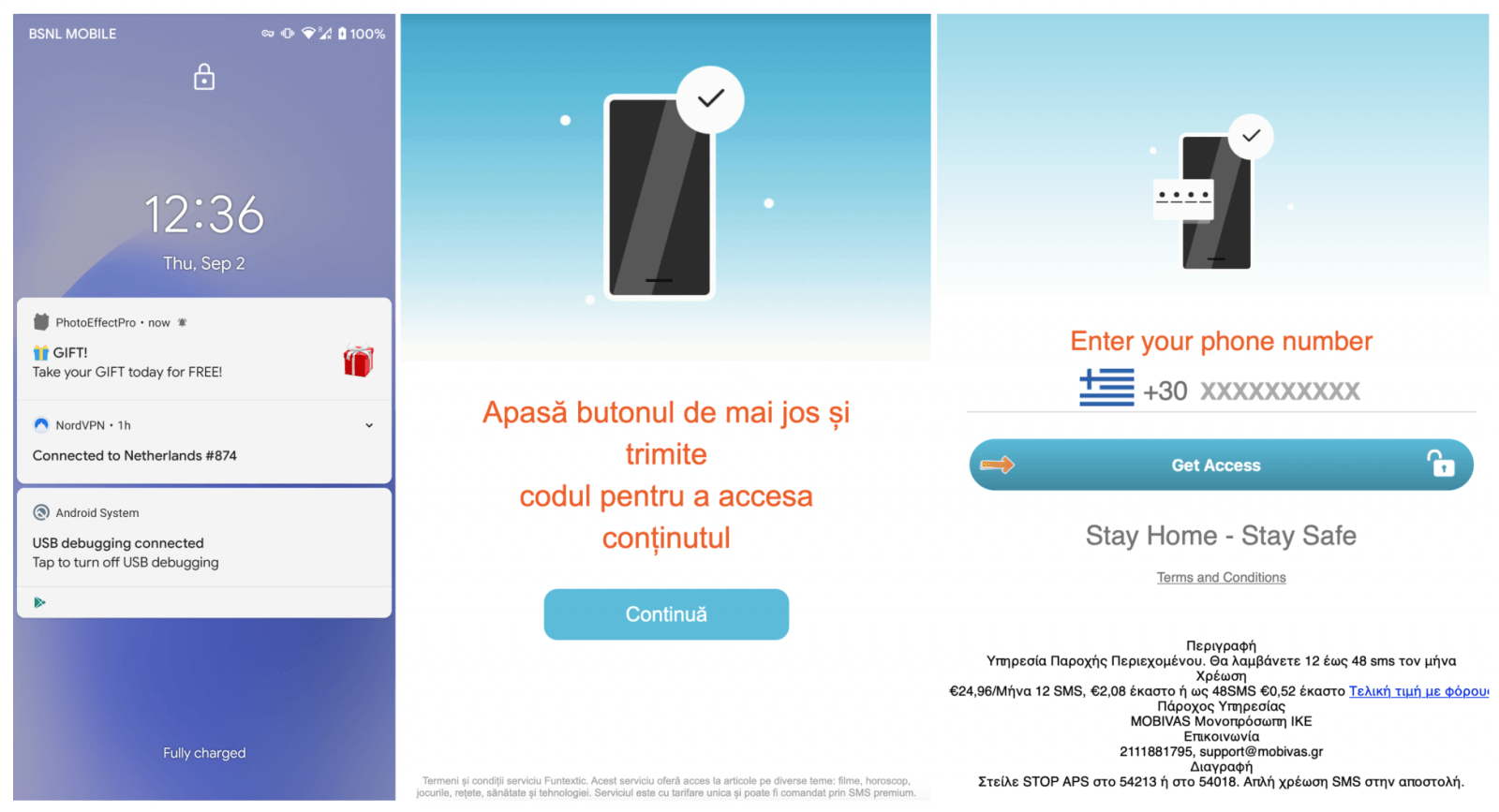
The way it works is that when a user installs one of these trojanized apps, GriftHorse will generate an insane amount of pop-ups and alerts that tempt the victim with prizes or special discounts. When the user taps on any of these notifications is redirected to a web page where they are required to confirm their phone number for verification.
What actually happens is that the users who clicked on the pop-ups are subscribing to premium SMS services that charge over $30 per month. This charge is added to the phone bill.
Zimperium zLabs recently discovered an aggressive mobile premium services campaign with upwards of 10 million victims globally, and the total amount stolen could be well into the hundreds of millions of Euros.
What Can the Victims Do?
The affected individuals who didn’t become aware of the problem on the spot had this charge added to their bills for months. Unfortunately, they can’t recover their money.
This means one of their first victims, if they have not shut off the scam, has lost more than €200 at the time of writing. The cumulative loss of the victims adds up to a massive profit for the cybercriminal group.
The numerical stats reveal that more than 10 million Android users fell victim to this campaign globally, suffering financial losses while the threat group grew wealthier and motivated with time.
Here you can find a list of all the infected applications.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










