Contents:
Key Takeaways:
- Vulnerability prioritization is about deciding what to patch, and in what order.
- Many organizations use unsatisfactory methods when prioritizing patches.
- Learn how a holistic, risk-based approach to vulnerability prioritization can improve patch management.
- Find out how automated vulnerability prioritization technology helps.
Picture the scenario. An organization’s monthly cybersecurity meeting is in full swing. The patching project manager is clicking through her presentation, and a chart appears showing her team has patched 10% more vulnerabilities than the month before.
But instead of praise, the new cybersecurity exec puts his hand up and asks: “Why have you focused on these patches in particular?”
It’s a challenging question, and one that’s not always easy to answer.
For most businesses, severity is the main metric used to decide what to patch first – a 2021 survey found 86% of organizations use it as the basis for planning.
But this isn’t, in and of itself, an especially effective strategy for vulnerability management. Just because a threat could have severe consequences, it doesn’t follow that it should be your most urgent priority.
Why is this? And are there better methods for vulnerability prioritization?
What’s Wrong With How Companies Prioritize Vulnerabilities? An Analogy
Most organizations focus on threat severity when deciding which patches to install first.
The standard approach is to use the Common Vulnerability Scoring System (CVSS). This is a free, open standard that grades the severity of known software vulnerabilities and is kept up to date by the US government’s National Vulnerability Database.
But while severity is undoubtedly an important consideration, it’s not always the most important factor.
An analogy can help show why.
Imagine you’re planning a summer beach vacation. Sensibly enough, you decide to buy travel insurance. When comparing quotes, you need to decide if you want to pay extra for ‘add ons’.
The insurer offers additional cover for all kinds of activities – from scuba diving to paragliding. However, you’re afraid of heights – so you’re unlikely to need the paragliding cover’.
Now, lacking insurance for this activity would have severe consequences for people in general if they had a paragliding accident. However, since you’re unlikely to do it, the risk to you is negligible.
On the other hand, you might want to go on some underwater adventures. So, you’d certainly want to prioritize the scuba cover.
Vulnerability prioritization is a little like travel insurance ‘add ons’. For example, a bug in a specific file storage system could pose a severe risk to many organizations, since the system could contain invaluable data. However, if your organization only uses that system to store low-value information, then patching it needn’t be your top priority. CVSS is not the same thing as risk.
He writes: “A risk is a potential for loss or damage if a threat exploits a vulnerability (which is a weakness in hardware or software)”, whereas a CVSS is a way to “describe the relative severity of security vulnerabilities in a consistent, quantitative way”.
Why Do Organizations Prioritize the Wrong Vulnerabilities?
Modern businesses face a seemingly endless stream of potential cyber threats. They use dozens of apps, with numerous users, all kinds of hardware and complex systems that must be kept up to date.
This results in the common problem of ‘patching paralysis’. They are overwhelmed by the sheer number of updates they need to install, and struggle to keep up.
The obvious solution? Prioritize those deemed most severe.
It’s a reasonable conclusion, and is entirely understandable. Focusing on threats that national authorities have ranked as potentially severe means:
- High impact cyber threats could be averted.
- It is easy to explain to the business why a system needs to be taken offline to be updated.
- In a context of endless patches, it appears to provide as good a rule for prioritization as any.
- For under-pressure cybersec teams, it offers a defensible explanation of why they’ve focused on certain patches over others.
Nevertheless, this is the wrong approach. It exposes organizations to real risks, while they expend time and energy patching unimportant vulnerabilities.
Threat Severity Does Not Equal Risk
As explained above, just because a security flaw in a product could be severe to some organizations, it doesn’t mean it’s a serious threat to you.
The opposite is also true. Just because a threat is generally not viewed as severe for most businesses, it could be extremely damaging if hackers used it to get into your systems.
And this is why a CVSS score should only ever be one part of your vulnerability assessments. As researchers writing in a 2022 edition of scientific journal Electronics point out: “CVSS remains a generic model that does not address the specificity necessary for successful prioritization in organizations.”
So, if ‘severity’ is not enough, how else should you be ranking vulnerabilities?
How to Prioritize Vulnerability Remediation Using a Risk-Based Approach
At Heimdal®, we believe that a holistic, contextualized and risk-based approach is the only effective way to prioritize patches.
But what does this mean in practice when you’re sitting down for vulnerability management prioritization meetings? What metrics should you be using to decide the order you’ll patch things in?
Here are some of the additional factors to consider when trying to judge your organizations risk:
- Has a risk been exploited in the wild?
If criminal actors are already known to have exploited a vulnerability at other organizations, then it’s more likely you will be next.
- What would its impact be on critical systems?
Does a vulnerability affect business critical systems, or does it mainly affect apps of lesser importance? The focus, evidently, should be on threats that would disrupt customer facing apps, financial and HR tools, or systems containing sensitive data.
- The qualitative perspective
Your IT teams should also be consulted to understand what impact a potential threat would have to your specific IT environment.
To illustrate – a known ransomware could block access to a data archive. But if your IT team knows that it is backed up daily to a secure third-party environment, the risk would be lower than for organizations without a backup.
Do It Yourself – Using a Vulnerability Prioritization Matrix
Proper vulnerability prioritization requires more effort than purely basing your patching plans on a CVSS score. Nevertheless, it will help you to manage your work much more effectively, and avoid wasted time and effort installing updates that aren’t essential.
A vulnerability prioritization matrix is a helpful tool for doing this. It can be as simple or as complex as you like, but is essentially a method for ranking risks.
To begin using a vulnerability prioritization matrix, you should first have completed an asset inventory, and know which vulnerabilities affect them. You can then start to fill in a matrix as follows:
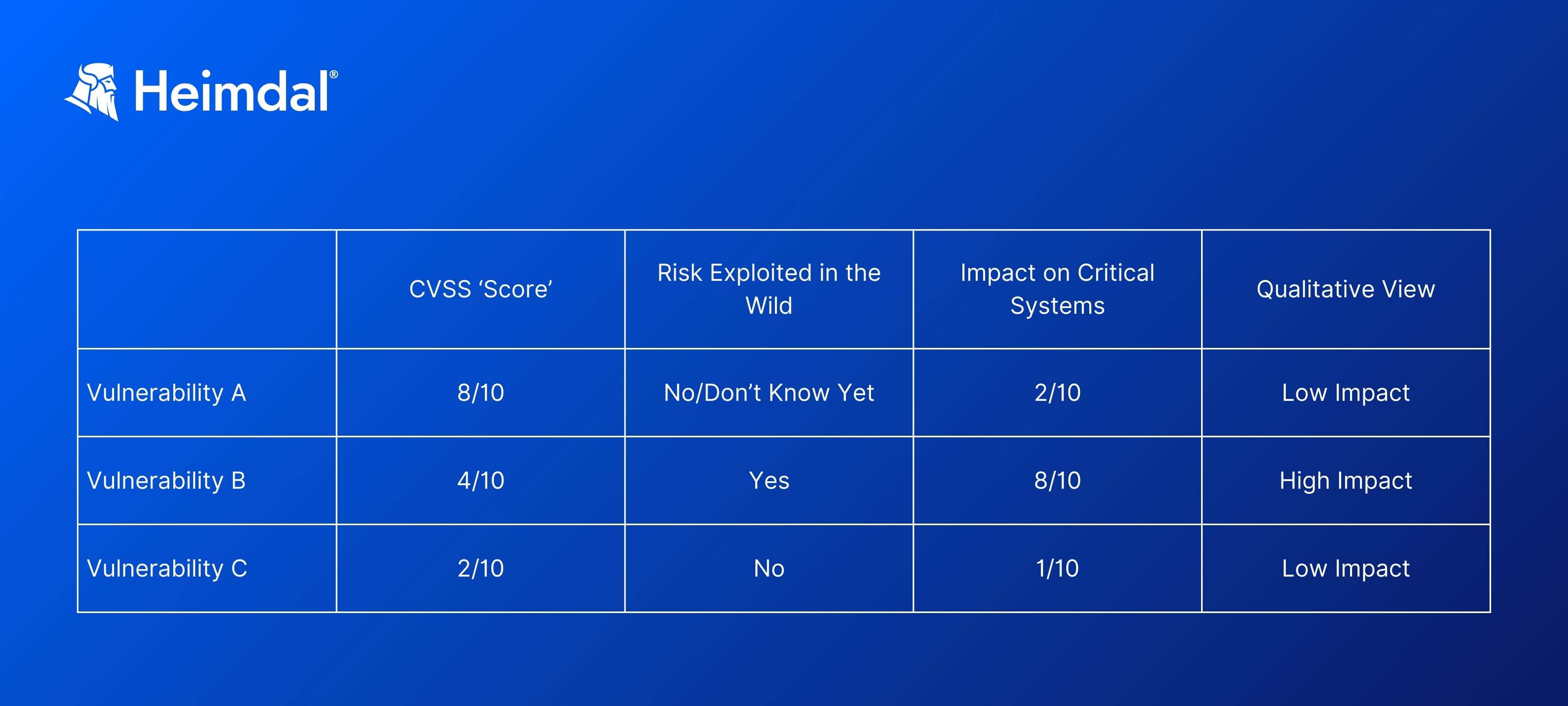
As the simplified matrix above suggests, Vulnerability B should be the top priority for the business. Even though Vulnerability A has a higher CVSS ranking, its impact on the business appears to be low, and it has not yet been exploited ‘in the wild’.
Automate Vulnerability Prioritization
Although it’s perfectly possible to carry out holistic vulnerability prioritizations manually, this approach has drawbacks:
- It’s time consuming.
- It tends to rely on in-person meetings.
- It is only done periodically (weekly or even monthly).
- It requires a large amount of discussion and analysis.
And this is where automated vulnerability prioritization technology comes in.
At Heimdal®, we have developed vulnerability prioritization tools that continually scan your systems to identify gaps. Our platform can then prioritize patches based on a range of factors informed by our expertise, known threat intelligence, and your needs. The technology can automatically apply patches (following your approval), test them and deploy them across your networks.
By automating vulnerability prioritization with Heimdal®, you can:
- Be confident that your real risks are being managed.
- Avoid unnecessary patching on systems that are a low priority.
- Focus your time, energy and resources on patches that actually matter.
Learn more about Heimdal®’s Patch & Asset Management software, or request a demo today.

Heimdal® Patch & Asset Management
- Create policies that meet your exact needs;
- Full compliance and CVE/CVSS audit trail;
- Gain extensive vulnerability intelligence;
- And much more than we can fit in here...
Frequently Asked Questions
What is vulnerability prioritization?
Vulnerability prioritization is a key step in the patch management process. It involves ranking cybersecurity vulnerabilities based on a defined, consistent set of values. Organizations may use a limited range of measures to prioritize vulnerabilities (e.g., prioritizing patches based purely on the ‘severity’ of vulnerabilities), or a more holistic approach that includes various contextually-driven factors (e.g., business impact, ease of exploitability, qualitative perspectives, etc.).
What are the limits of the Common Vulnerability Scoring System (CVSS) in vulnerability prioritization?
Although CVSS is a very useful tool for understanding the possible impact of a cybersecurity threat, it only tells part of the story. There are many other factors which are just as – if not more – important than severity when judging the impact of a particular vulnerability. To better prioritize vulnerabilities, you could try integrating EPSS scores in your vulnerability prioritization process.
How should you prioritize vulnerabilities?
A holistic approach to vulnerability prioritization offers the most effective and reliable method for patch planning. It considers multiple ways that a specific vulnerability could affect your organization, including the severity of the vulnerability, its impact on your specific business systems and activities, your organization’s existing security measures, your risk appetite and more.
Who is responsible for vulnerability prioritization?
While this varies from one organization to the next, vulnerability prioritization is often most effective when done as a collaborative exercise. The patching team should take the lead, but it is important to get insights from other members of the wider cybersecurity and IT teams, and relevant department heads too.
If you want to keep up to date with everything we post, don’t forget to follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








