Contents:
Four new vulnerabilities have been discovered in the TP-Link Tapo L530E smart bulb and TP-Link’s Tapo app. Researchers from Universita di Catania and the University of London say that hackers could exploit these flaws to steal WiFi passwords.
TP-Link Tapo L530E smart bulb is a top seller, including through Amazon and TP-Link Tapo smart device management app has over 10 million installations on Google Play. Researchers also examined the TP-Link Tapo TC60 camera model to compare vulnerabilities across different devices.
Their popularity is what made researchers from Italy and the UK analyze them. The paper containing this information focuses on highlighting security dangers in the numerous consumer IoT devices. Different firmware versions, such as 1.3.7 and 1.1.16, can contain varying security risks.
Among the identified risks there are hazardous data transmission and inadequate authentication procedures.
TP-Link acknowledged the findings and expressed the intention of fixing the bugs. However, it is unclear from the paper if the patches have already been released or not.
Details about the Vulnerabilities in Security Cameras
The first of the vulnerabilities (CVSS v3.1 score: 8.8) allows the threat actor to pretend to be the Tapo L503E device during the session key exchange phase on. A hacker could use this improper authentication high-severity flaw to steal passwords and manipulate the device. The vulnerabilities are often found within the device firmware, which can be extracted and analyzed to identify security flaws.
The second flaw is also a high-severity issue (CVSS v3.1 score: 7.6) arising from a hard-coded short checksum shared secret, which attackers can obtain through brute-forcing or by decompiling the Tapo app.
BleepingComputer (Source)
The third bug is of medium severity and refers to the cryptographic scheme’s predictability due to the lack of randomness during symmetric encryption. The encryption key used in the cryptographic scheme can be targeted to decrypt sensitive information.
The absence of tests for the recentness of received messages causes a fourth issue. This allows attackers to replay communications for 24 hours while maintaining the session keys’ validity.
Possible Attacks on IP Cameras
Using these TP-Link Tapo vulnerabilities, cybercriminals can attack users in several manners. These vulnerabilities make the devices easily hacked, allowing unauthorized access.
Threat actors can use vulnerabilities 1 and 2 to perform bulb impersonation and steal the user’s account details. Using the stolen data, the attacker can access the WiFi SSID and password, opening a path to all the devices connected to the network. IP cameras like the Tapo TC60 are particularly vulnerable due to poor security measures.
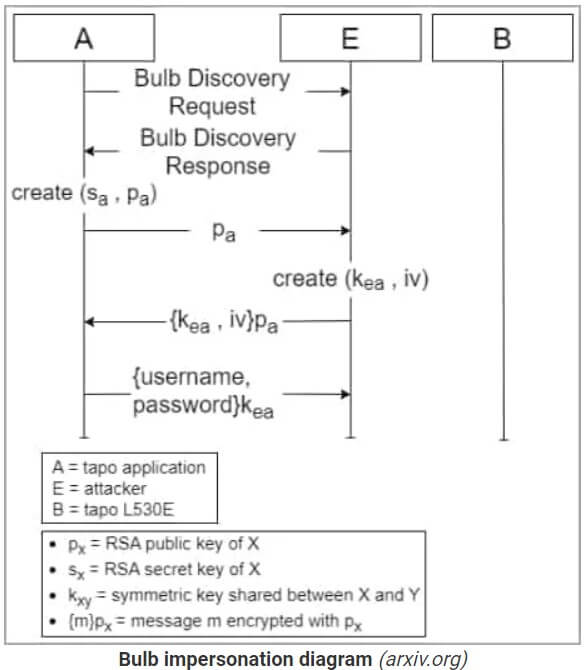
BleepingComputer (Source)
For this attack to work, devices must be in setup mode. But the attacker can reset the smart bulb’s authentication, causing the user to re-configure it in order to get it working again.
Another attack type explored by the researchers is MITM (Man-In-The-Middle) attack with a configured Tapo L530E device, exploiting vulnerability 1 to intercept and manipulate the communication between the app and the bulb and capturing the RSA encryption keys used for subsequent data exchange.
MITM attacks are also possible with unconfigured Tapo devices by leveraging vulnerability one again by connecting to the WiFi during setup, bridging two networks, and routing discovery messages, eventually retrieving Tapo passwords, SSIDs, and WiFi passwords in easily decipherable base64 encoded form.
BleepingComputer (Source)
Lastly, vulnerability 4 enables attackers to execute replay attacks, copying already intercepted communications to make changes to the device’s functionality. Unauthorized access to the video feed can compromise user privacy and security.
How to Stay Safe with Updated Device Firmware
IoT devices are more and more common, which is why IoT security becomes a crucial subject for cybersecurity.
Tips to stay safe:
- separate IoT devices from crucial networks
- use the most recent firmware updates and companion app versions that are available
- use strong passwords and multi-factor authentication to secure accounts
- narrow down internal and external port communication on your firewalls
- invest in network security solutions that can protect a network if a device gets breached
- use a virtual private network (VPN) to limit access to your home network.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security