Contents:
The REvil ransomware group managed to conduct one of the largest ransomware attacks that we’ve seen recently when it attacked MSPs and their customers in an operation that should have been extremely successful.
However, the ransomware group changed the typical tactics and procedures when handling this attack, thus leading to a disappointing number of ransom payments.
It’s a well-known fact that when ransomware gangs are conducting an attack, they usually start by breaching a network in order to steal data and delete any backups before ultimately encrypting the victim’s devices.
This way when a victim is seeing proof of stolen data whilst having the backups deleted, and their devices encrypted, the ransomware group has a much stronger incentive for the victim to pay the ransom to restore their data and prevent the leak of it.
Was the Attack Flawed?
This time things happened differently as the REvil affiliate responsible for this attack decided to forgo the standard tactics and procedure, and used a zero-day vulnerability in on-premise Kaseya’s VSA servers to perform a massive and widespread attack without actually accessing a victim’s network.
This tactic can be considered successful as it led to the most significant ransomware attack in history, with approximately 1,500 individual businesses encrypted in a single attack, but overall, from a financial standpoint, it looks like this attack is not nearly as successful as the REvil gang would have wanted.
You might be wondering why this attack did not pan out as REvil wanted and the answer stands in the M.O. as with backups not being deleted and data not stolen, the ransomware gang had little leverage over the victims.
Cybersecurity researchers familiar believe that the victims were lucky they were attacked in this way as the threat actors did not have regular unfettered access to networks and were forced to use automated methods of deleting backups.
The Emsisoft CTO Fabian Wosar managed to extract the configuration for a REvil ransomware sample that was used in the attack, the sample showing that the REvil affiliate made a rudimentary attempt of deleting files in folders containing the string ‘backup’.
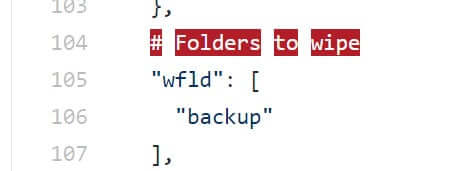
However, it seems that the method used was not successful as an MSP and multiple victims encrypted during the attack declared for the news publication BleepingComputer that none of their backups were affected as they chose to restore rather than paying a ransom.
Bill Siegel, the CEO of the ransomware negotiation firm Coveware, declared for BleepingComputer that was a popular decision amongst the victims of the attack as not one of their clients has had to pay a ransom.
In the Kaseya attack, they opted to try and impact EVERY Kaseya client by targeting the software vs direct ingress to an MSP’s network. By going for such a broad impact they appear to have sacrificed the step of encrypting/wiping backups at the MSP control level.
This may end up being a bit of a saving grace, even for MSPs that had poorly segmented backups for their clients.
While it is certainly impressive that Sodin was able to pull off this exploit, we have not seen the level of disruption that typically follows a single MSP attack where the backups are intentionally wiped or encrypted, and there is no other way to recover data without paying a ransom.
The disruption is still bad, but encrypted data that is unrecoverable from backups may end up being minimal. This will translate to a minimal need to pay ransoms.
Impacted MSPs are going to be stretched for a while as they restore their clients, but so far none of the clients we have triaged have needed to pay a ransom. I’m sure there are some victims out there that will need to, but this could have been a lot worse.
It’s important to note that the victims who ultimately had to pay a ransom most likely had poor backups to restore from.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
This comes to show how important it can be to have a proper cybersecurity strategy in place.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








