Contents:
TikTok is undoubtedly one of the most popular social media outlets, and as a consequence, hackers are not far behind capitalizing trends to trick their victims. Currently, one of the TikTok challenges, Invisible Challenge, is being exploited to install malware on thousands of devices and steal their passwords, Discord accounts, and even cryptocurrency wallets.
This challenge requires users to film themselves naked while using TikTok’s Invisible Body filter, which removes the body from the video and replaces it with a blurry background.
As a means to capitalize on this, threat actors are creating TikTok videos offering an “unfiltering” tool which eliminates the initial effect to expose TikTokers’ nude bodies.
As you might have guessed already, this software is fake and actually installs the W4SP Stealer malware, known for stealing Discord accounts, passwords and credit cards stored on browsers, cryptocurrency wallets, and even files from a victim’s computer.
These videos promoting the fake filter remover received over a million views, while one of the threat actor’s Discord servers gathered over 30,000 members.
Targeting TikTok
In a report posted by cybersecurity firm Checkmarx, two particular videos posted by the attackers are given as example. The researchers determined that the now suspended TikTok users @learncyber and @kodibtc created the videos to promote a software app to “remove filter invisible body” offered on a Discord server called Space Unfilter. The videos quickly gained viewers, and thus potential victims.
Once the users join the Discord server, they see a link posted by a bot directing them to a GitHub repository that hosts the malware. The attack has become so successful that, according to BleepingComputer, the malicious repository has achieved a “trending GitHub project” status, and although it has since been renamed, it currently has 103 stars and 18 forks.
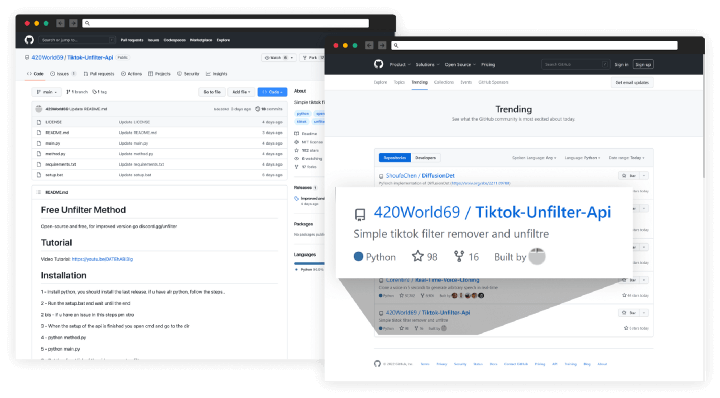
Into the Specifics
The project files contain a Windows batch file (.bat) that, upon execution, installs a malicious the WASP downloader and a ReadMe file that links to a YouTube video giving instructions on how to install the TikTok filter removing tool.
Checkmarx analysts further discovered the use of multiple Python packages hosted on PyPI, including “tiktok-filter-api”, “pyshftuler”, “pyiopcs,” and “pydesings,”, with new ones added every time the old packages are reported and removed. The malicious package imitates the original code but contains a modification for installing WASP malware on the host.
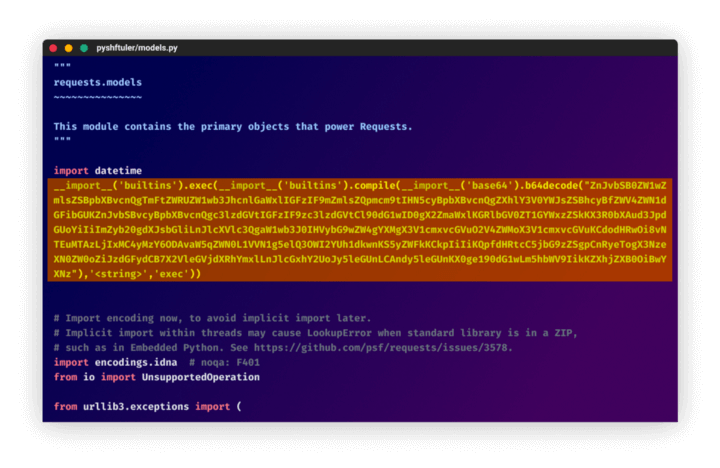
In addition, the attackers use the StarJacking technique, which means a package is published with an URL pointing to an already popular source code repository, in this case linking their project to a popular GitHub project they have no association with.
It seems this attack is ongoing, and whenever the security team at Python deletes his packages, he quickly improvises and creates a new identity or simply uses a different name. […] These attacks demonstrate again that cyber attackers have started to focus their attention on the open-source package ecosystem; We believe this trend will only accelerate in 2023.
The GitHub repository used by the attackers is still up, but the “TikTok unfilter” packages have been replaced by “Nitro generator” files, while the Discord server Unfilter Space was taken offline, with the threat actors allegedly moving to another server.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







