Contents:
DPDgroup is a package delivery business that operates on a global scale. DPD is an abbreviation for Dynamic Parcel Distribution, which comprises trademarks such as DPD, Colissimo, Chronopost, Seur, and BRT, among others. The company is established in France and is primarily involved in the expedited road-based transportation sector.
What Happened?
Customers are required to input a parcel number and a postcode in order to monitor the status and location of their package, and if the information they provide matches a legitimate record in the database, they will be granted access to the shipping information.
Researchers from Pen Test Partners investigated the system and discovered that they could use parcel codes to make API calls and get back OpenStreetMap addresses along with the recipient’s location on a map as a result.
An unauthenticated API call was identified in DPD Group’s public API that could allow a user with a valid package ID to, with some basic OSINT, discover the package’s destination postcode and thus obtain all details about the package.
DPD Group were prompt in the triage and resolution of the vulnerability, which was fixed in October 2021.
In spite of the fact that the call resulted in just a snapshot of the map, it is rather simple to deduce the postcode in the majority of situations by referring to the street names on the map.
An unauthorized user might get access to someone else’s tracking page, which would disclose delivery details if they had a valid parcel number and a matching postal code.
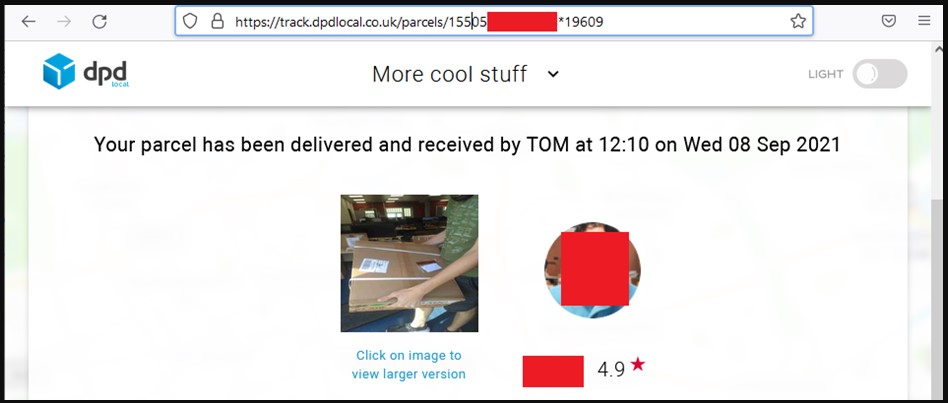
As BleepingComputer reports, when a valid session token is provided, one may examine the underlying JSON data, which includes the person’s complete name, email address, cell phone number, and other personal information about them.
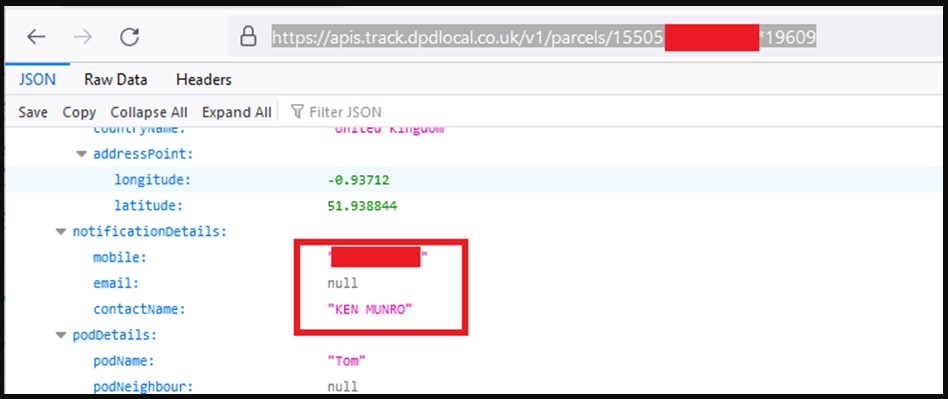
The problem was found last year in September, and a solution was made available in October, leaving the API access vulnerability exploitable for at least a month, although the window of opportunity was most likely considerably longer than that.
Despite the fact that the researchers were most likely the first to find this, the possibility of “silent” long-term misuse cannot be ruled out.
Even though the manner in which this API attack operated was random, since it was impossible to estimate parcel numbers for given identities, it would still be beneficial in the hands of phishing perpetrators.
Knowing the delivery status data as well as the contact information for the company that ships the package lays the groundwork for a successful phishing attack.
This is not the first time when a package delivery company faces security issues as just last year we uncovered a large spam campaign that was using GLS’s identity.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










