Contents:
Last week, the U.S. District Court for the Eastern District of Virginia has accused three men of money laundering and aggravated identity theft as part of a Business Email Compromise (BEC) campaign.
What Is BEC?
As explained by my colleague Dora, Business Email Compromise (BEC) is a type of targeted scam in which an attacker impersonates a company executive or high-level employee with the intent of defrauding or extracting sensitive data from the company or its partners.
The end goal of a BEC fraud is to persuade the target to make a money transfer or send sensitive data to the attacker while believing they are executing a legitimate and regular business operation.
According to BleepingComputer, between January 2018 and March 2020, Onyewuchi Ibeh, 21, of Bowie, Maryland, Jason Joyner, 42, of Washington, D.C., and Mouaaz Elkhebri, 30, of Alexandria, Virginia, hacked the corporate networks of small and large businesses in the United States and around the world.
Operation Mode
Through phishing attacks or malware deployment, the three individuals compromised their victims’ computer systems, including their email servers and email accounts.
Following the initial attack, the hackers spent several months blocking communications and learning everything they could about payment systems, communication patterns, distributors, customers, people in charge of transactions, and so on.
Afterward, the scammers reportedly sent fake emails to a staff member, displaying a payment request looking just like a legitimate transaction that was due for payment at the time.
The attackers were able to redirect the money to their bank accounts by using all of the specifics of the real transaction, including full invoice information.
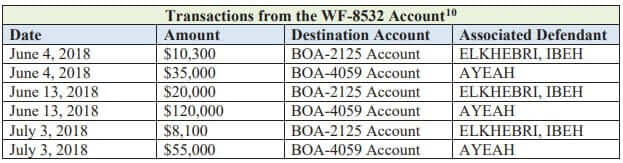
According to the superseding accusation, the suspects reportedly laundered approximately $1.1 million gained illegally from at least five targeted companies through a BEC scam.
Different Roles in the BEC Attack
Onyewuchi Ibeh’s reported part in the operation was to oversee the money laundering by arranging for conspirators to create bank accounts, which he then used to send money both locally and abroad.
Joyner’s role in the plan was to take cash from the scam profits and deliver it to other participants.
The third man, who worked for Bank of America and TD Bank for three years, was in charge of opening bank accounts in the names of his co-conspirators and their victims, and he also falsified bank book records.
In response to legal process, Bank of America produced personnel records for Elkhebri, who worked as a personal banker and relationship manager there from 2015 until 2017. During his time at Bank of America, Elkhebriopened multiple Conspirator Accounts, including an account that Ibehused in furtherance of the scheme.
In response to the legal process, TD Bank also produced personnel records for Elkhebri, who worked there from 2017 until 2018. During his time at TD Bank, Elkhebri opened multiple Conspirator Accounts, including an account that Ayeah used in furtherance of the scheme.
Up to 52 Years in Prison
If found guilty, Ibeh and Joyner face a maximum sentence of 20 years in prison, while lkhebri faces a mandatory minimum of two years in prison and a maximum sentence of 52 years in jail.
As mentioned in the indictment, the actual sentences for federal crimes are usually less than the maximum penalties.
A federal district court judge will determine any sentence after taking into account the U.S. Sentencing Guidelines and other statutory factors.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










