Contents:
The Morse Code signaling system, first used in 1844, is not a common choice for operational security among cyber attackers, yet it was used to obscure malicious software. This is a reminder that, despite their complexities, modern offensive and defensive cyber measures often rely on the simple concept of concealing and cracking code.
On Thursday, Microsoft researchers revealed that threat actors were sending specific victims fake invoices to steal their credentials and to collect IP addresses and location data of victim machines. The hackers changed their encryption schemes every month to try to hide their activity.
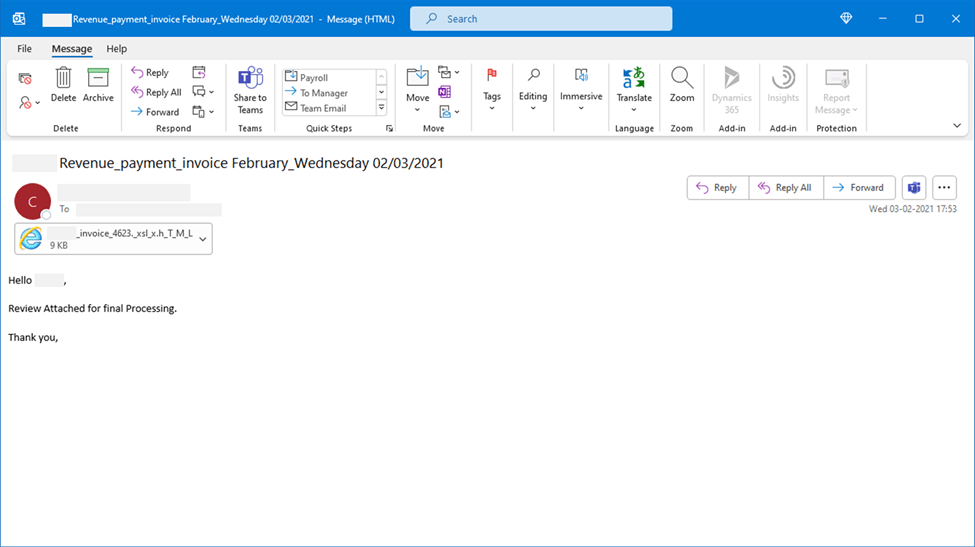
Sample phishing email message with the HTML attachment
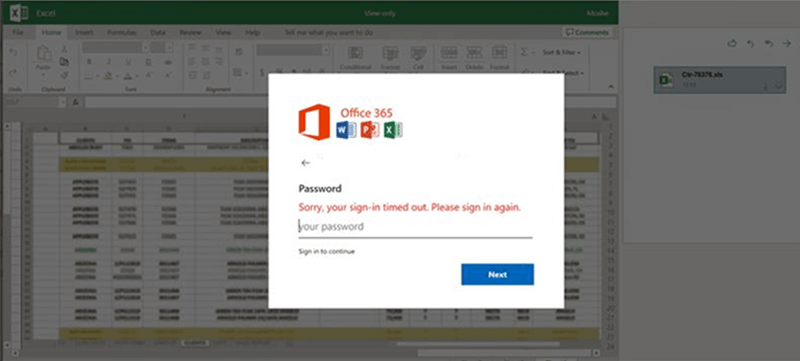
Using xls in the attachment file name is meant to prompt users to expect an Excel file. When the attachment is opened, it launches a browser window and displays a fake Microsoft Office 365 credentials dialog box on top of a blurred Excel document. Notably, the dialog box may display information about its targets, such as their email address and, in some instances, their company logo.
The user is asked to re-enter their password because their Excel document access has supposedly expired. Nevertheless, if the victim does enter their password, they receive a fake note that the submitted password is incorrect. In reality, the attacker-controlled phishing kit running in the background collects the password and other sensitive information about the user.
According to Microsoft’s M365 Security unit principal research manager Christian Seifert, the tech giant has yet to attribute the hackers to a known group.
The use of Morse Code was observed in the February (“Organization report/invoice”) and May 2021 (“Payroll”) waves, the researchers added.
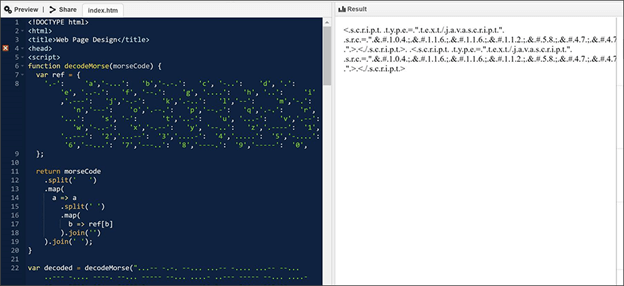
In the February iteration, links to the JavaScript files were encoded using ASCII then in Morse code, while in May, the domain name of the phishing kit URL was encoded in Escape before the entire HTML code was encoded using Morse code.
To reduce the impact of this threat, Microsoft researchers recommend applying these mitigations:
- Use Office 365 mail flow rules or Group Policy for Outlook to strip .html or .htm or other file types that are not required for business. Check your Office 365 antispam policy and your mail flow rules for allowed senders, domains, and IP addresses.
- Turn on Safe Attachments policies to check attachments to inbound email. Enable Safe Links protection for users with zero-hour auto-purge to remove emails when a URL gets weaponized post-delivery.
- Avoid password reuse between accounts and use multi-factor authentication (MFA);
- Educate end-users on consent phishing tactics;
- Turn on network protection to block connections to malicious domains and IP addresses.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security