Contents:
Threat actors use search engines to advertise websites that spread ransomware or steal login credentials. The ads for various impersonated businesses and services appear at the top of search results and guide the victim to websites that spoof almost perfectly the real ones.
The announcement was made by the FBI, which warns that:
When a user searches for that business or service, these advertisements appear at the very top of search results with minimum distinction between an advertisement and an actual search result. These advertisements link to a webpage that looks identical to the impersonated business’s official webpage.
Cybercriminals purchase advertisements that appear within internet search results using a domain that is similar to an actual business or service. When a user searches for that business or service, these advertisements appear at the very top of search results with minimum distinction between an advertisement and an actual search result. These advertisements link to a webpage that looks identical to the impersonated business’s official webpage.
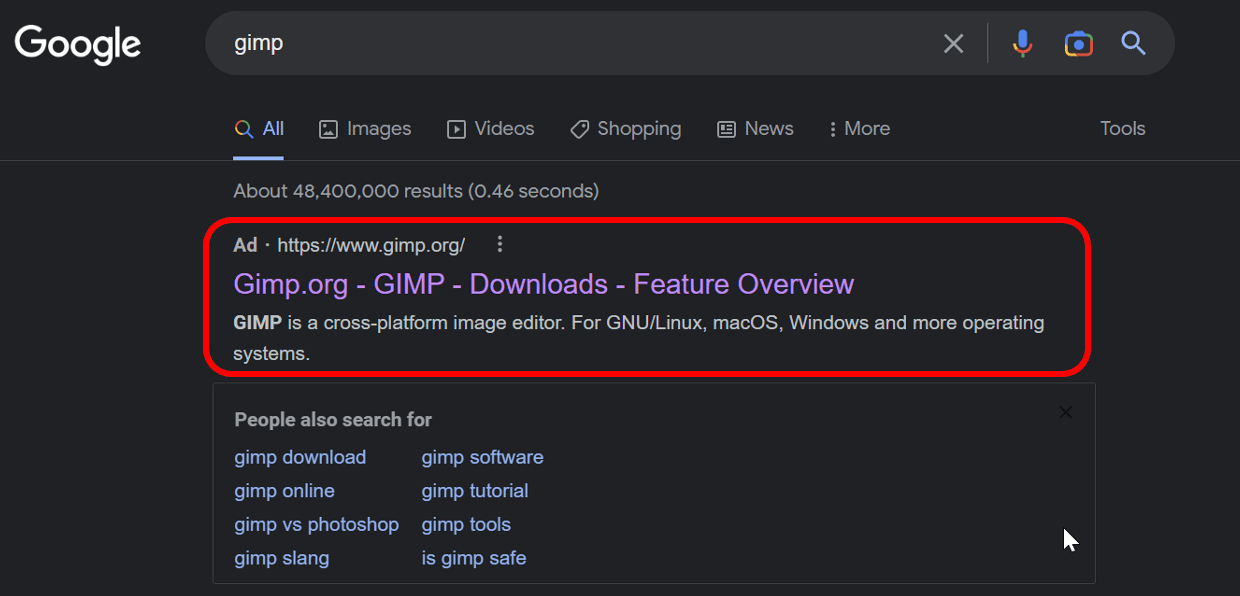
Users that are searching for certain programs to download should be aware that they may stumble upon one of that fraudulent web pages which will infect their endpoint with malware when the „download software” link is clicked. One can easily be tricked, as the download page domain corresponds to or is very similar to the name of the software that was searched for.
The same type of ads was used for impersonating sites related to financial services, like cryptocurrency exchange platforms. They look like real exchange platforms and unadvised users end up submitting their login credentials and other financial data. This is exactly what threat actors that are into phishing need for stealing their money.
How to Protect Your Business from Search Engine Malicious Ads
- Check the URL for typos or spelling errors before you click it.
- Type the business’s URL into your browser’s address bar so you can make sure you`ll really end up on that business`s official site.
- Use ad-blockers, to filter promoted results on Google Search.
- Educate your endpoint users to recognize spoofed websites and always check if the URL is correct
- Tell your endpoint users where they can find safe downloads for the programs they need.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







