Contents:
Researchers discovered that hackers actively exploit a critical SQL injection vulnerability in multiple versions of the web-based billing and invoicing system BillQuick to deploy ransomware on exposed systems.
BillQuick Web Suite from BQE Software is a project management software that includes accounting, billing, and time-tracking features. According to the organization, it has around 400,000 users all over the world.
Cybersecurity experts at Huntress Labs said that the bug, tracked as CVE-2021-42258, can be easily exploited by sending login requests with invalid characters (a single quote) in the username box.
As mentioned by BleepingComputer, the issue has been addressed earlier this month, on October 7, after Huntress Labs alerted the company of the bug.
However, eight other undisclosed security issues are yet to be patched including:
- CVE-2021-42344,
- CVE-2021-42345,
- CVE-2021-42346,
- CVE-2021-42571,
- CVE-2021-42572,
- CVE-2021-42573,
- CVE-2021-42741,
- CVE-2021-42742.
The researchers declared:
Our team was able to successfully recreate this SQL injection-based attack and can confirm that hackers can use this to access customers’ BillQuick data and run malicious commands on their on-premises Windows servers.
We have been in close contact with the BQE team to notify them of this vulnerability, assess the code changes implemented in WebSuite 2021 version 22.0.9.1, and work to address multiple security concerns we raised over their BillQuick and Core offerings (more to come on these when patches are available).
They also said that the SQL-injection vulnerability was used in attacks against an unnamed U.S. engineering organization. The flaw, which allows for remote code execution (RCE), was successfully leveraged to obtain initial access and launch a ransomware attack.
The actor we observed did not align with any known/large threat actor of which we are aware. It’s my personal opinion this was a smaller actor and/or group based on their behavior during exploitation and post-exploitation.
However, based on the issues we’ve identified/disclosed, I would expect further exploitation by others moving forward is likely. We observed the activity over Columbus Day weekend (08-10 October 2021).
Who Is Responsible?
The ransomware threat actor who conducted these attacks isn’t known yet, and its developers haven’t left any messages asking for ransom on the encrypted systems. Hence, they can’s be identified.
Up to this point, the attackers didn’t make any ransom demands in exchange for a decryption key that would help their victims recover their files.
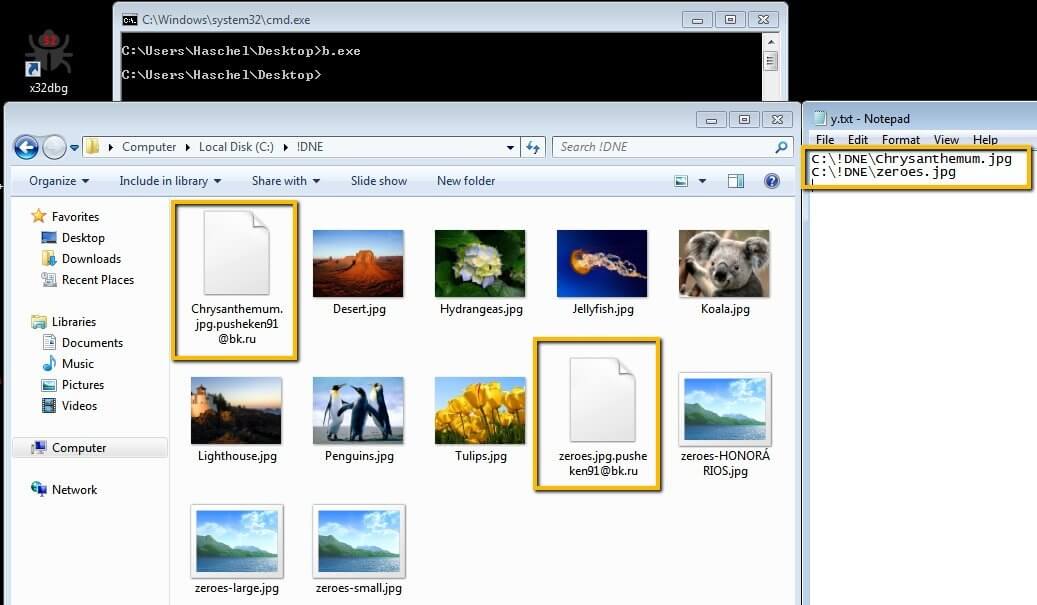
According to BleepingComputer, the ransomware deployed by these threat actors has been active since at least May 2020, and it copies code from other AutoIT-based ransomware types.
When installed on victim networks, it will append the pusheken91@bk.ru extension to all encrypted files, but no ransom note has been seen so far.
At the end of August, the FBI and CISA were urging organizations to make sure they have good defense capabilities in place. The two agencies advised to not let down defenses against ransomware attacks as they’ve noticed an increase in attacks during the weekends or holidays.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










