Contents:
Cybersecurity authorities around the world have published a list of the top 15 vulnerabilities regularly exploited by malicious actors in 2021, in collaboration with the NSA and the FBI.
In a joint alert, the cybersecurity authorities recommended enterprises patch these security holes as soon as possible and adopt patch management systems to decrease their attack surface.
Hackers have been spotted targeting internet-facing systems, such as email and virtual private network (VPN) servers, employing exploits targeting recently reported vulnerabilities all around the world.
U.S., Australian, Canadian, New Zealand, and UK cybersecurity authorities assess, in 2021, malicious cyber actors aggressively targeted newly disclosed critical software vulnerabilities against broad target sets, including public and private sector organizations worldwide. To a lesser extent, malicious cyber actors continued to exploit publicly known, dated software vulnerabilities across a broad spectrum of targets. The cybersecurity authorities encourage organizations to apply the recommendations in the Mitigations section of this CSA. These mitigations include applying timely patches to systems and implementing a centralized patch management system to reduce the risk of compromise by malicious cyber actors.
What Are the Vulnerabilities in Question?
In the same advisory, a table containing all the 15 discovered vulnerabilities was provided. You can see it below:
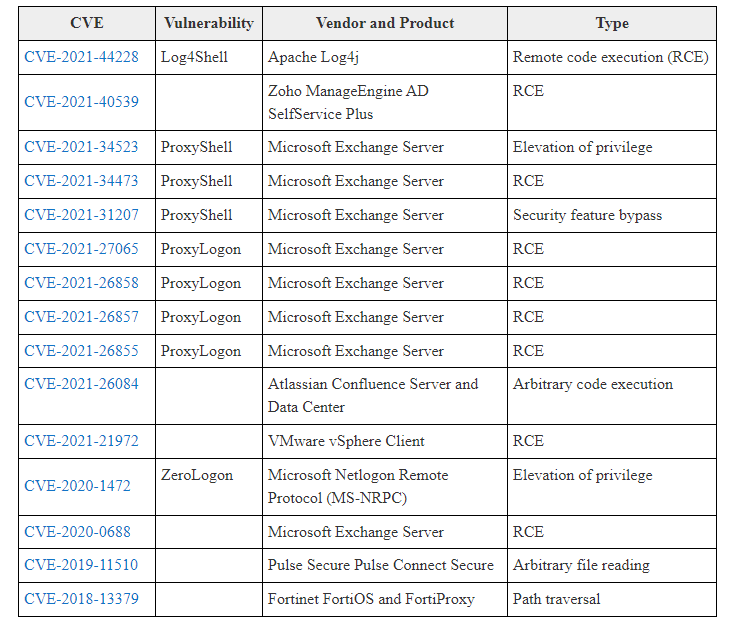
However, some attackers targeted older vulnerabilities that had been patched years ago, indicating that some firms refuse to upgrade their systems even when a patch is available, says BleepingComputer.
The cybersecurity agencies of the United States, Australia, Canada, New Zealand, and the United Kingdom have also discovered and disclosed 21 additional security vulnerabilities that hackers usually abused in 2021, including ones that affect the Accellion File Transfer Appliance (FTA), Windows Print Spooler, and Pulse Secure Pulse Connect Secure.
Mitigation steps are included in the joint recommendation, which should help reduce the risk associated with the topmost misused flaws listed above.
In partnership with the Australian Cyber Security Centre (ACSC) and the United Kingdom’s National Cyber Security Centre, CISA and the FBI also released a list of the top 10 most exploited security bugs from 2016 to 2019 and a list of commonly exploited flaws in 2020.
How Can Heimdal Help?
As we always say, prevention comes first in the process of a proper cybersecurity strategy, so vulnerability management plays a huge role in securing holes in the system that might become sooner or later the path a hacker takes to infiltrate a company’s network. Choose Heimdal Patch & Asset Management and enjoy A to Z patch management along with advanced patch scheduling and the shortest vendor-to-end-user waiting time (you have the patch ready to be deployed in less than 4 hours from the release). Keep your system updated and close off security gaps!

Heimdal® Patch & Asset Management
- Create policies that meet your exact needs;
- Full compliance and CVE/CVSS audit trail;
- Gain extensive vulnerability intelligence;
- And much more than we can fit in here...
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










