Contents:
The macro virus was downright tony in the late ’90s and has certainly done its best to secure a great spot in the malware hall of fame. Some reports suggest that Melissa, a macro virus variant, has caused damages that amount to $1.1 billion.
The ‘wow’ factor is strong in this one considering that we’re talking about malware that was wreaking havoc long before the Internet became a commodity. No, I’m not nostalgic, though the 90s were amazing – macro viruses have made a comeback and, unfortunately, we can’t wish them away. This article is dedicated to this slice of history which instead of resting blissfully behind a dusty display glass, has decided to go on one last rampage.
What exactly is a macro?
According to Wiki, a macro (i.e. short for macro-instruction) is “a rule or pattern that specifies how a certain input sequence should be mapped to a replacement output sequence according to a defined procedure.” Translated from Klingon, the definition reads a way to automate keyboard or mouse commands within a computer program.
Macros were popularized by word-processing or spreadsheeting software like Microsoft’s Word and Excel but actually started being the norm with the advent of massive-multiplayer online gaming. To this day, creating macros in Excel or Word is a tricky process, since it requires some coding know-how – well, you can always copy-paste the pre-assembled code from online resources like GitHub.
Die-hard Excel users would immediately recognize the merit of macros, as they become vital when the workload increases. In MS Word and Excel, macros can be recorded by live-capturing keystrokes/mouse clicks with the Macro Recorder or by writing down the key-clicks sequence in a Visual Basic for Application window.
These macros can be as easy-peasy or complicated you would like them to be. For instance, you can use the Macro Recorder feature to transcript the mouse click sequence associated with creating a two-cell/two-column table. This macro can be enabled by appending a keyboard shortcut to it (e.g. CTRL + T).
So, every time you hit that key combo, the macro will auto-insert a table with the attributes I’ve just described. If you’re a hardcore user, you can always create custom macros, capable of handling more complex word-processing tasks or spreadsheet operations. My all-time favorite, code-spun macro is the so-called “Hello, world!” caption.
Basically, every time you open that workbook, a custom message box pops up on the screen. Why would you bother writing down all that code just for a meager popup? Well, there’s nothing wrong with learning to code.
The second, and most important reason, is that this message popping up on screen means that that the auto-run macro feature is enabled. Keep that in mind because we’re going to talk about it in the next section of this article. For those of you seeking VBA enlightenment, here’s the code for the “Hello, world!” caption.
Public Sub Example
Msgbox “Hello darkness, my old friend.”
End Sub
What is a macro virus?
Now that we’ve finally gotten the macro part of the way, let’s see where the macro virus fits in. So far, we’ve learned that macro-instructions can be utilized to automate some mundane word-processing tasks (e.g. insert popups, headers, tables).
But what would happen if the VBA code written inside these macro modules would have an entirely different purpose? Well, then you’ll get what is called a macro virus. Nasty little buggers they are and quite difficult to detect even with modern attachment scanners. Because we’ve grown quite fond of boorish and academically-arousing elucidations, here’s how SANS Institute’s paper Living with Malware defines the macro virus:
“A type of computer virus that is encoded as a macro embedded in a document. (…) These applications (i.e. Excel and Word) allow you to embed a macro in a document, and have the macro execute each time the document is opened.”
From this statement, we can infer the following facts:
- Macro viruses may exhibit worm-like behavior (explan. auto-replication with the purpose of infecting other hosts);
- Macro viruses can infect the host if the requirements are met (i.e. auto-run macro is turned on; the file is stored locally).
- Macro viruses can spread through any computer program that supports macro-instructions.
Considering that Microsoft disabled the Autoexec macro function back in the late ‘90s, it would be reasonable to say that we’ve dodged the macro virus bullet. Not quite; as the story goes, Microsoft’s ham-handed attempt at putting the kibosh on macros would not remain without a retort. Modern macro viruses are more than capable of working their way around these limitations.
Some have the ability to reinstate the Autoexec feature, while others would coax the users into switching on this option themselves. Another aspect I would like to submit your consideration is that macro viruses don’t just through macros embedded in Excel or Word documents.
They can also hide in email attachments. As you would imagine, the latter is more pervasive compared to the garden variety word-embedded malicious macro. How so? One possible explanation is killing two birds with one stone. Sending a fake email to several contacts at a time increases the likelihood of success.
The second reason is related to the existing email security infrastructure. Many companies use basic email security tools like spam filters, but very few take advantage of content scanning or other deep-mail inspection technologies. I’ll cover this in the last section of the article, which is dedicated to prophylaxis and remediation.
An interesting aspect of the micro virus is its ability to infect all past, present, and future files spawned by the application it’s piggybacking. For instance, if come across a not-so-suspicious and weaponized word doc, the virus will not only compromise the document itself, but all files of the same feather (i.e. extension) – past, present, and future.
Profiling macro viruses
A bit of background on macro viruses. WordMacro/DMV is the first macro virus. Fortunately, it did not have the chance of doing any damage because it never left the lab it was created in. DMV was a timid foray into advanced computer viruses. Joel McNamara, the comp scientist behind DMV simply wanted to study how a macro-aided virus can interact (and disrupt) OS operations.
DMV and lab coat humor
The virus itself simply displayed a message on the screen, making the user aware of its presence. McNamara’s virus, whose primary purpose was to educate computer users on the dangers of the digital world, was to become the source of inspiration for people who saw malicious potential in this otherwise benign creeper.
The year was 1994. Exactly one year later, the first macro virus was to be released into the wild. Its name was Concept and, very much like McNamara’s DMV, its purpose was to prove a point. Concept did not burn out hard drives, encrypt, or delete files.
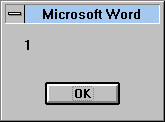
Actually, it did nothing of consequence. According to the researchers studying Concept, once the virus-infected Word file was opened, a dialogue box would have appeared on the user’s screen. This mysterious box contained the number “1” and a big “OK” button. Concept contained 5 infectious macro modules, the last one being “Payload”.
Image credits: Data Fellows
While one might be inclined to think that the latter module’s laden with destructive code. In reality, it contains a single text line that reads: “REM That’s enough to prove my point.” Cryptic, hectic, and utterly useless in the long run. As for the numbered dialog box, researchers theorized that it may be a countdown of the generations of macro viruses. Concept has had a few offspring of note – Concept. BZ aka Haifa, Concept.G, and Concept. F.
Melissa and Bart the Genius
Having proved their worth, micro viruses are needed now to prove their prowess. And the turn of the century provided the threat actors with ample opportunities to show just how devastating a macro virus can become. Come 1999, a new type of macro virus claws its way out of anonymity. Melissa is its name.
To compare Melissa to its predecessors would be like stacking up a match flame against a wildfire. And the facts back up this statement. According to Virus Wikidot, the compounded costs of Melissa amount to $1.1 billion. If the 9-figure number wasn’t enough, get this – Melissa was able to jump from host to host via email.
Whereas Concept only infected machines via compromised CDs or floppy disks, Melissa would use your contacts list to infect even more machines. So, what happens if your computer gets infected by the Melissa macro virus? As a side note, Melissa’s first encounter with its target has quite a lot common with second-generation malware – or the other way around.
More specifically, M. used to take advantage of people haphazardly opening emails before it was cool – a true-blooded hipster among viruses. How did Melissa compromise machines? Well, it all started with an inconspicuous email. Back then, sending an email or doing a mundane task like looking up a topic on Wikipedia as somewhat of a privilege.
Of course, I can’t say if that was true for the rest of the world or simply an Eastern European thing. Anyway, being a child of the ‘90s meant embracing novelty, however gauche or extravagant or nonsensical that ‘new’ may have been. So, it’s 1999, you’re at home and checking your email inbox. And there it is!
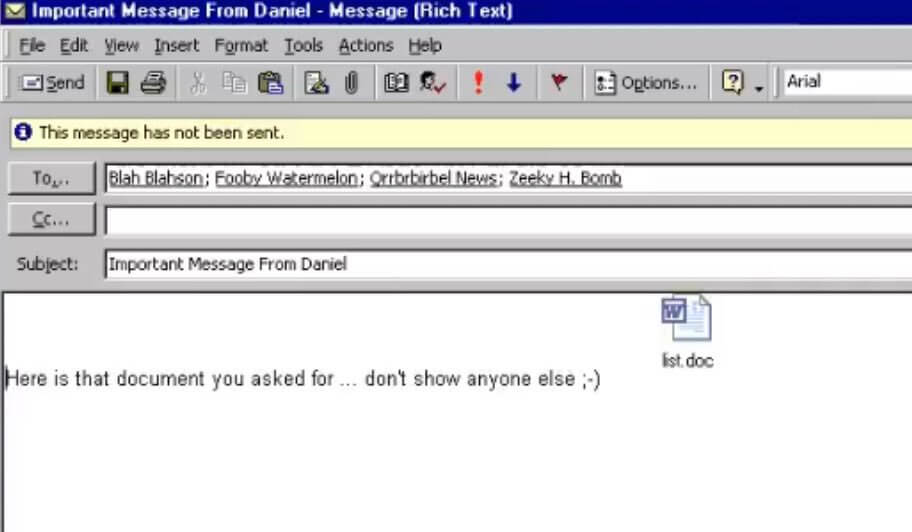
A new email from your best friend, crush, mother, father, or a friend to whom you haven’t spoken to in a while. Melissa’s subject lines followed the same pattern: “open me”, “check out this email”, “look at what I’ve found”.
So did the message’s body: “Here is that document you asked for…don’t show it to anyone (awkward 90s emoticon”). The email also contained a small .doc attachment called <list.doc>. Seeing that the email came from a trustworthy source, you don’t see any reason why you shouldn’t open the attachment. The <list.doc> contained a rundown of the most ‘popular’ porn websites.
Image credits: danooct1
Treasure trove or booby trap? I would say the later. While you were busy curating the list, Melissa would make some changes to your system registry. More specifically, upon opening the doc, this macro virus would have checked your MS Office registry key for a specific subdirectory called <Melissa? Exists with…by Kwyjibo”. If the value wasn’t set, Melissa would have to input it along with the subdirectory.
This MS Office registry key ‘instructed’ your default email agent to send the infected mail to 50 of your contacts. At the same time, dearest Melissa would have infected the Normal.dot template, which MS Word uses in all newly-created documents.
This serves two purposes: to compromise all future documents and leak sensitive information via the websites included in the list. As an extra goodie, some Melissa variants (e.g. Melissa alternative payload who infected files based on the time of the day) would taunt the victim with quotes from pop culture.
Here’s an example of messages one could find in Melissa-infected documents: “22 points, plus triple-word-score, plus 50 points for using all my letters. Game’s over! I’m outta here.” If you’re thinking Simpsons, you’re absolutely right.
Melissa had some noteworthy successors. To name a few, we have Melissa. BG or Resume (i.e. pops up in the email in the form of an infected job resume), Assilem (i.e. capable of infecting machines running clean, ‘unupdated’ MS Windows versions), and Melissa.W or Prilissa (i.e. covers documents in colored squares).
Echoes
In profiling macro viruses, the following statements were found to be true. So, macro viruses can and will:
- Take advantage of word-processing built-in functions (i.e. Macro Autoexec).
- Have various spread vectors (e.g. CDs, floppy disks, email attachment, etc.).
- Use social engineering techniques to increase the likelihood of success.
- Exfiltrate sensitive information if they can redirect the user to malicious webpages.
- Modify or corrupt registry files for obfuscation purposes.
Though believed to be extinct, macro viruses managed to make quite a comeback. Bear in mind that MS Office’s security features make it impossible for viruses to use this attack vector. On top of that, we have the ever-present AV layer. So, two countermeasures that protect your machine against macro viruses. So, do they still pose a threat? Very much so, but not on their own.
Modern macro viruses are usually a part of MaaS (Malware-as-a-Service) ‘business’ packages. For instance, Metasploit, whose primary purpose is pen-testing, can, and many times be used, to create malware.
Offensive Security, a website specialized in cybersec training, proves that Metasploit can inject infected macros in either Word or Excel documents. The Meterpreter payload gives the newly-generated malware some extra muscle, not to mention enhanced obfuscation capabilities. You can read about OFFSEC’s off-the-table experiment for more info on the topic.

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
Fighting History. Macro virus countermeasures.
How does one fight a fleeting shadow? By killing the lights, I guess. If that doesn’t work, you should probably improve your cloak-and-dagger game. It’s, by far, the most interesting and useful exercise one should indulge in for the sake of cybersecurity. Let’s review the basics.
| AV On Ensure that your antivirus software is running and up-to-date. Remember to check the agent from to time. Some malware goes about disabling the AV before going on a rampage. Having the AVs database up to speed increases the detection likelihood. | Watch for Spam Spammy emails are not only infuriatingly frustrating but can also harbor malware. If your company’s email employs some sort of spam filtering, ensure that the filter’s operational and inform support if any spam-like emails manage to circumvent the filter. Naturally, one should never open susp email or execute in-mail attachments. |
|---|---|
| Autoexec Macro Off Although Microsoft disabled the Autoexec macro feature (by default) some macro viruses can tacitly active this function without the user’s consent or requesting confirmation. To ensure that macros are turned off (Word & Excel) head to File>Trust Center>Trust Center Setting and select Macro Settings. Check if the box next to “Disable all macros without notification” is ticked. If not, check the box, click OK, and restart Word or Excel. | Secure external media drives Don’t forget that external media drives (e.g. thumb drives, CDs, floppy disks, memory cards, etc.) can harbor malware. Best to give them a scan before opening any type of content. Your AV or anti-malware software surely has an auto-scan option which should kick in every time you insert an external media drive into your machine. Refer to your AV vendor for more information about auto-scanning features. |
One last thing before you go; there’s no such thing as too much protection. Heimdal™ Security award-winning products offer complete protection against all types of malware, including macro viruses. And because antivirus is never enough, check out Endpoint Security Software, your personal go-to cybersecurity suite. Heimdal™ Security’s intelligence ensures that all malware is dealt with, regardless if they’re new or on the usual suspects’ list.
Conclusion
It’s too soon to talk about the mass extinction of the celebrated macro viruses. Naturally, the macro viruses we see today are infinitely different from the ones that plagued the ‘90s. So, refrain from opening spammy emails, keep your AV up-to-date, and never turn a blind eye to something just because it’s arcane.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security