Contents:
The Department of Justice has taken down 48 domains and charged six individuals for operating “booter” or “stresser” platforms that allow anyone to conduct denial of service attacks efficiently.
Some sites use the term “stresser” in an effort to suggest that the service could be used to test the resilience of one’s own infrastructure; however, as described below, I believe this is a façade and that these services exist to conduct DDoS attacks on victim computers not controlled by the attacker, and without the authorization of the victim.
Stressers offer the same DDoS features as other products but claim to provide these for legitimate purposes.
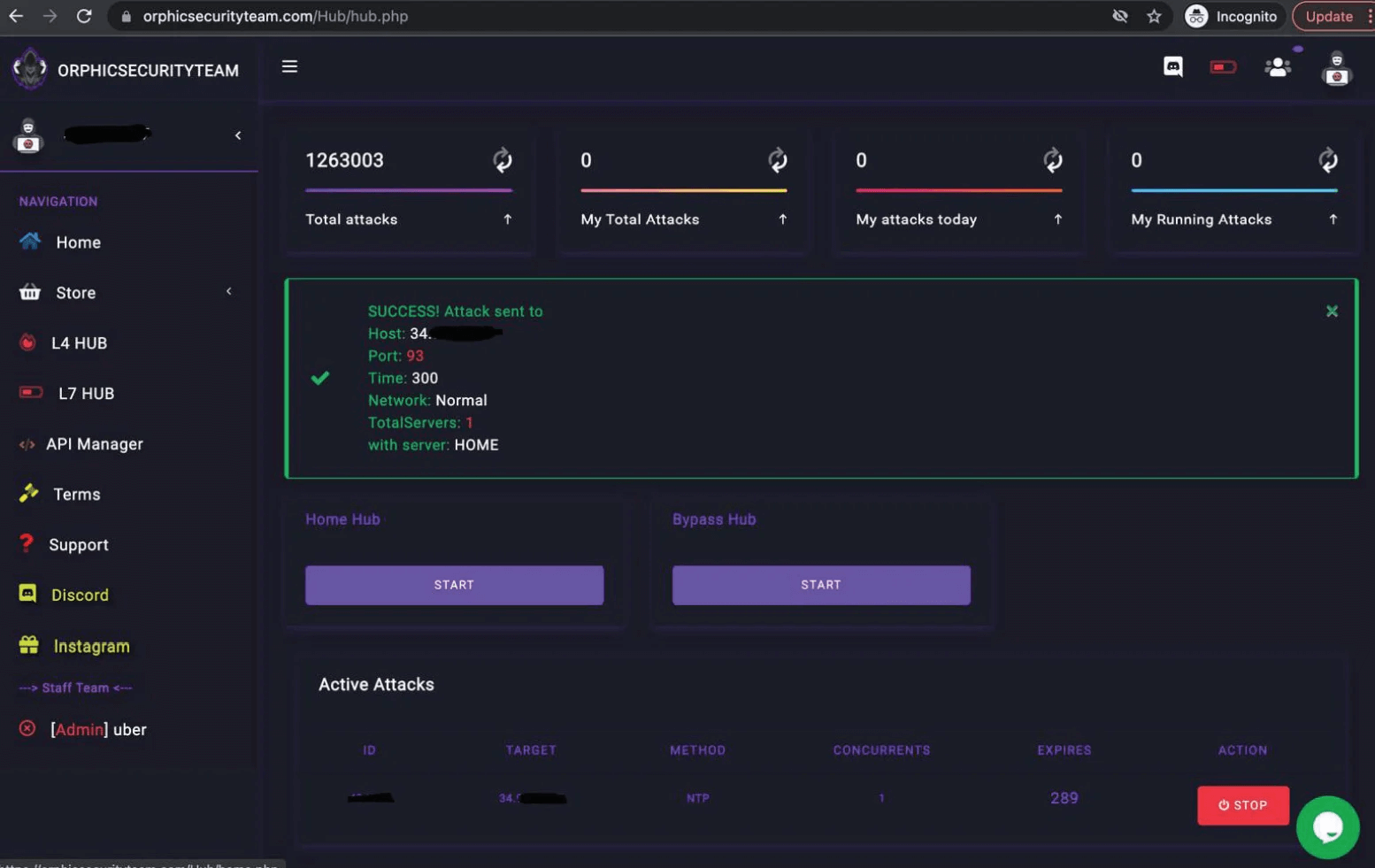
The term “stresser” is sometimes used to suggest a service could be used to test the resilience of your infrastructure. However, as we read in an affidavit by FBI Special Agent Elliott Peterson from the Alaska field office, this is a façade, and most sites are for conducting DDoS attacks on unsuspecting victims.
Cryptocurrency-based ransomware service providers have specific requirements for the user to use their services. For example, the threat actor must register an account, deposit cryptocurrency, and then use the funds to pay for their desired service.
While you cannot guarantee the person you buy a booter/stresser service from won’t use it for malicious purposes, these services attract some shady characters. It’s possible that whoever takes the time to set up their site could also be a criminal trying to profit off online dependability.
In many cases, the service’s owner(s) will promote it on cybercrime sites or through affiliates that make a commission by upgrading it.
Targeting DDoS Platforms Worldwide
Today, the US Attorney’s Office in the Central District of California and the US Attorney’s Office in the District of Alaska announced charges against six individuals for operating booter/stressor sites.
This week, we’ve taken major steps to eradicate criminal activity threatening the internet’s infrastructure and our ability to function in a digital world.
-said United States Attorney Martin Estrada.
These booter services allow anyone to launch cyberattacks that harm individual victims and compromise everyone’s ability to access the internet.
The suspects in this case include:
- Someone from Texas.
- Three people from Florida.
- One person from New York.
- One other person is suspected of operating a stressor/booster site.
These websites are RoyalStresser.com, SecurityTeam.io, Astrostress.com, and Booter. Sx, Ipstressor.com, and TrueSecurityServices.io.
The FBI and international law enforcement recently ramped up their efforts to take down DDoS platforms by seizing 48 Internet servers. This is just one component of the larger Operation PowerOFF they’ve been conducting.
Once a domain has been seized and transferred to law enforcement’s DNS server, a seizure message will warn that these services are illegal.
Thom Mrozek from the LA US Attorney’s Office told BleepingComputer that the FBI has been working with domain authorities to apply the seizure messages but that the platforms have already been taken down.
As an outside agent, the FBI works with law enforcement agencies from other countries to identify malicious websites that offer illegal “booter” services. Then, they display these ads in search engine results when people search for these services.
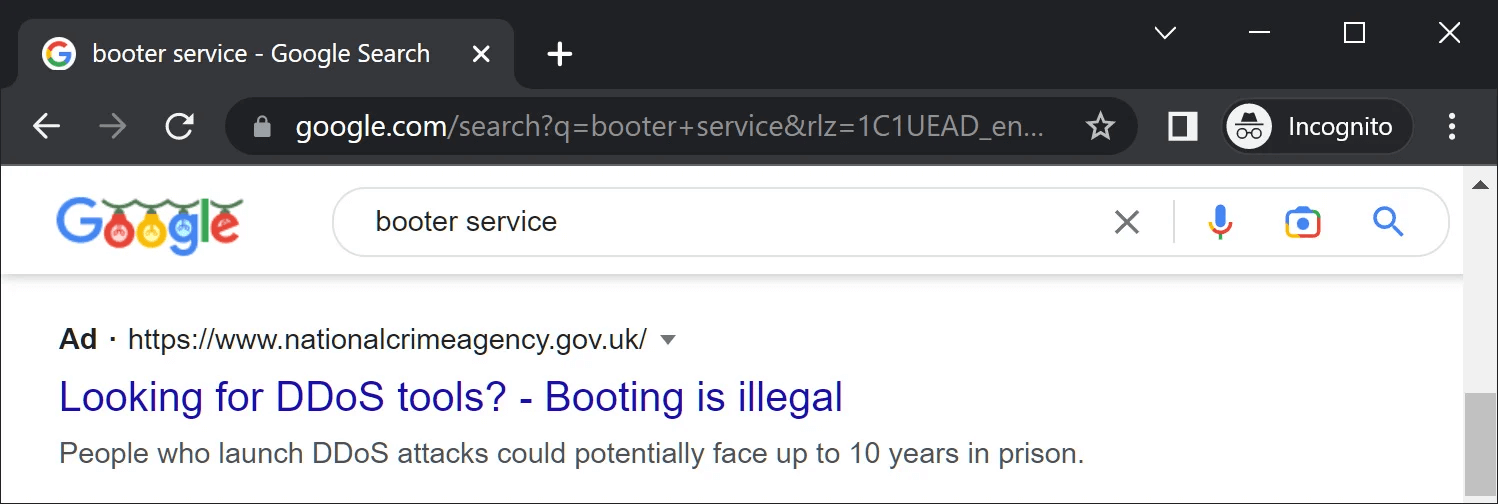
Let’s say that you’re looking for DDoS tools on Google. One result when we searched for ‘booter service’ was an ad saying, “Looking for DDoS tools? Booting is illegal.”
In the UK, a cyber advertisement leads to a Cyber Choices page with information about how people can “make informed choices and use their cyber skills in legal ways.” A similar ad from the FBI leads to a web page managed by the Anchorage field office that explains why DDoS attacks are illegal.
The complete list of domains seized by the FBI:
- anonboot.com
- api-sky.xyz
- astrostress.com
- booter.sx
- booter.vip
- brrsecurity.org
- buuter.cc
- cyberstress.us
- dragonstresser.com
- dreams-stresser.io
- freestresser.so
- instant-stresser.com
- ipstress.org
- ipstress.vip
- ipstresser.wtf
- orphicsecurityteam.com
- ovhstresser.com
- quantum-stresser.net
- redstresser.cc
- royalstresser.com
- silentstress.net
- stresser.app
- stresser.best
- stresser.gg
- stresser.is
- stresser.net/stresser.org
- stresser.one
- stresser.so
- stresser.top
- supremesecurityteam.com
- truesecurityservices.io United States France Namecheap 1
- vdos-s.co
- zerostresser.com
- ipstresser.xyz
- kraysec.com
- securityteam.io
- blackstresser.net
- ipstresser.com
- ipstresser.us
- stresser.shop
- exotic-booter.com
- mcstorm.io
- nightmarestresser.com
- shock-stresser.com
- stresserai.com
- sunstresser.com
- bootyou.net
- defconpro.net
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








