Contents:
MyKings botnet appeared in the wild five years ago and is one of the most analyzed botnets in history.
A botnet is a collection of infected computers or other internet-connected devices that collaborate to carry out the same malicious acts, such as spam campaigns or distributed denial-of-service assaults. Online criminals can remotely manage the network to serve their own goals, allowing them to escape detection and legal prosecution by law enforcement agencies.
What Makes MyKings Botnet Special?
The MyKings botnet, also known as Smominru, is a mash-up of multiple security trends. The creators of MyKings have also experimented with steganography, a common technique used for hiding malware in a benign-looking picture.
The botnet was able to conceal its dump (in.exe format) behind pictures utilizing steganography, therefore making it able to hide an.exe (an executable file) within a JPEG image file.
The dangerous .exe file self-executes and launches a cryptocurrency miner to generate Monero because antivirus software only checks the genuine JPEG image.
This botnet is particularly interesting for researchers as it uses a complex infrastructure alongside versatile features, like bootkits, miners, droppers, and clipboard stealers.
The researchers at Avast were the last ones to run an analysis on the botnet after they gathered 6,700 unique samples.
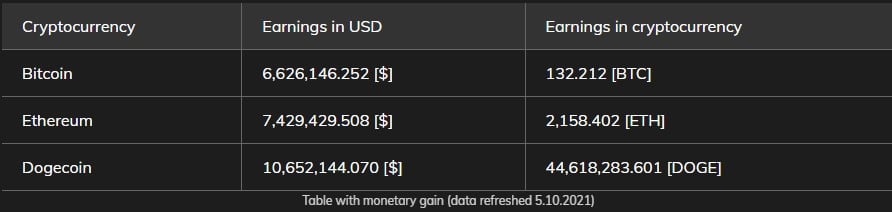
The botnet seems to own a large number of bitcoin wallet addresses, many of which have a lot of money in them. The clipboard stealer and crypto mining components have amassed the cryptocurrency in these wallets.
The earnings from MyKings wallet account for a total of $24.7 million. However, since the botnet uses more than 20 cryptocurrencies in total, this figure represents only a small portion of the botnet’s overall financial profits.
The virus works by encrypting itself in the hardcoded wallet address value with a rudimentary ROT algorithm to prevent it from being extracted and analyzed.
The researchers have discovered a new monetization strategy employed by MyKings operators leveraging the Steam gaming platform, in addition to the wallet address substitution that diverts transactions.
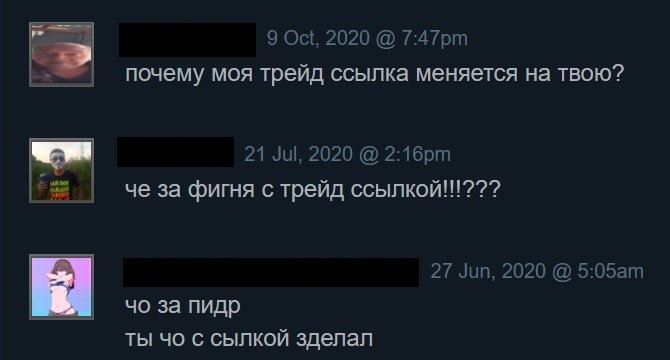
The attackers designed a URL manipulation mechanism inside the clipboard stealer module within the newest versions of the malware to hijack Steam item trade transactions. The module alters the URL of the trade offer, putting the actor on the receiving end of the transaction and allowing him to steal valuable in-game goods, among other things.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








