Contents:
On Tuesday, Verizon released its 15th annual Data Breach Investigations Report (DBIR), which, as usual, provides security professionals and executives around the world with an overview of global trends and patterns concerning cyberattacks and data breaches.
The most recent edition of the report looked at over 23,000 security incidents (of which 5.212 were confirmed data breaches) that occurred between November 1, 2020, and October 31, 2021.
Let’s take a look at the key findings of Verizon’s 2022 Data Breach Investigations Report.
Credential Theft
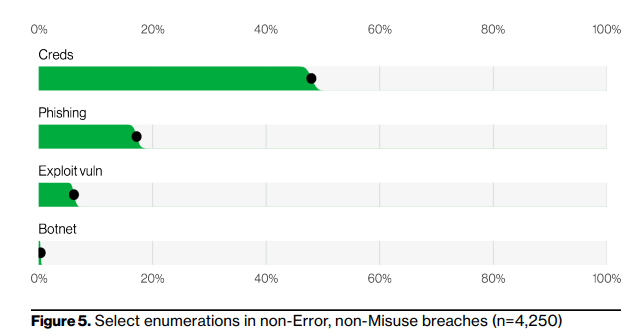
The report showed that a worrisome percentage of the incidents that took place last year were carried out by cybercriminals using a particular type of cybercrime: stolen credentials.
Credential theft was noticed in third-party breaches, phishing campaigns, Basic Web Application Attacks (BWAA), and system intrusions, accounting for almost 50% of all cyberattacks.
As per the report, there has been a nearly 30% rise in stolen credentials since 2017, making it one of the most successful ways to obtain access to an organization for the past four years.
Ransomware
The report notes that ransomware has increased by nearly 13% this year, which is more than the previous five years combined (for a total increase of 25% this year).
40% of Ransomware incidents involve the use of Desktop sharing software and 35% involved the use of Email. There are a variety of different tools the threat actor can use once they are inside your network, but locking down your external-facing infrastructure, especially RDP and Emails, can go a long way toward protecting your organization against Ransomware.
The Human Element
The human factor is still driving breaches. This year, the human factor was involved in 82% of breaches. Individuals continue to play a significant part in cyberattacks and breaches, whether through the use of stolen credentials, phishing, misuse, or simply a mistake. The report reminds us once again that employee training is an important part of improvement.
Other Findings
As per the DBIR report, this year, supply chain attacks accounted for 62% of system intrusion incidents, which involves malicious actors hacking partners or organizations.
The report also says that the combination of data breaches and ransomware incidents resulted in significant growth in stolen credentials and malware.
External threat actors accounted for 80% of all global data breaches, four times the rate of internal ones. According to the report, external actors were responsible for 90% of attacks in the North American region alone.
Cybercriminals are primarily motivated by financial gain, which has been a top motive since Verizon started monitoring the motivations behind data breaches in 2015.
These actors are still motivated by greed (financial gain) and are stealing personal data because it is easy to monetize.
According to the Data Breach Investigations Report, hacking was the most common malicious activity that resulted in the disclosure of unauthorized information. 70% of data breaches were caused by hacking. The most common types of hacking were web applications and Denial of Service (DoS) attacks.
For the first time in the report’s 15 years, software updates were among the top vectors in the DBIR. This is followed by human carelessness, which is associated with mistakes like misdelivery and misconfiguration.
As per the DBIR team, the report and the data it contains are intended to raise awareness of what strategies malicious actors are likely to employ against businesses in various industries. It is recommended that readers consider it a tool to encourage executives to support much-needed security initiatives, as well as a way of showing employees the importance of cybersecurity and what they can do to help.
To read the full report, click here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








