Contents:
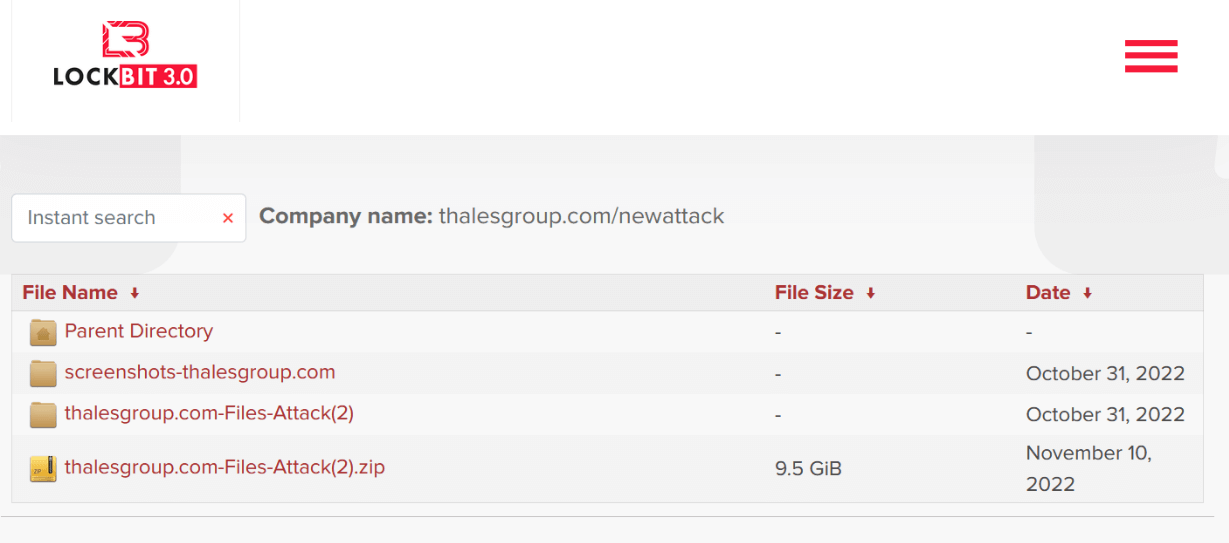
The Lockbit 3.0 ransomware group began leaking a 9.5 Gb archive file that is presumably stolen information from the Thales Group, after the company refused to pay the ransom.
Thales Group is a French multinational high-tech company, with over 81,000 employees worldwide. The company is known for investing in digital and “deep tech” innovations such as: big data, artificial intelligence, connectivity, cybersecurity, and quantum technology.
What Happened?
After adding Thales to its list of victims on October 31, the Lockbit 3.0 group threatened to release stolen data on November 7, 2022, if the company did not pay the ransom.
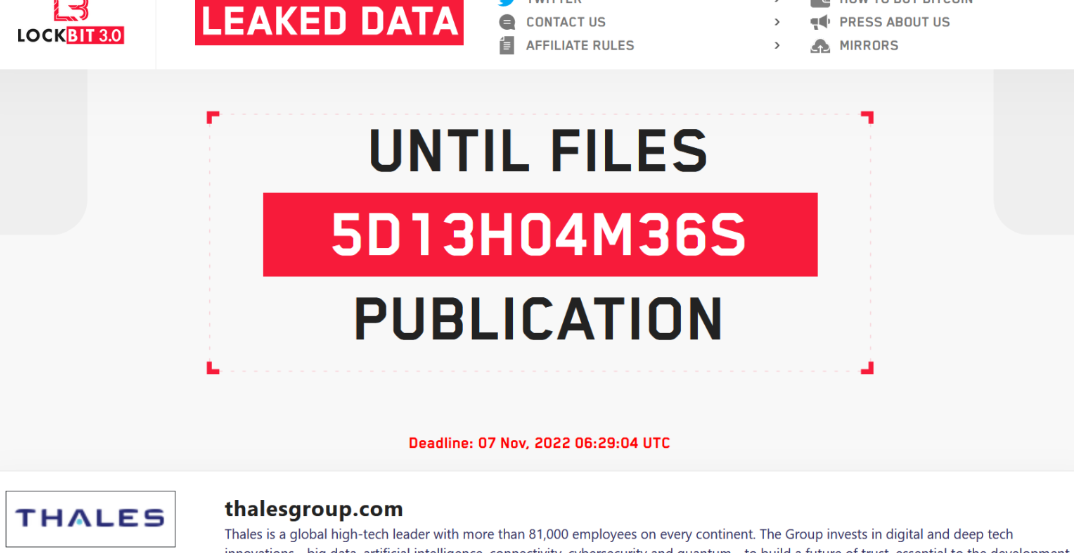
The deadline was met, and the ransomware gang kept its word and followed through with its threats. The organization first began releasing the company’s private information on the 11th of November, according to Security Affairs.
Thales Group’s Position
The French Company revealed last week that it was aware of the ransomware gang claiming to have stolen some of its data, but clarified that “there has been no intrusion of its IT systems”.
Thales security experts have identified one of the two likely sources of the theft, which has been confirmed through the user account of a partner on a dedicated collaboration portal. This has led to the disclosure of a limited amount of information.
Thales Group’s complete official position on the ransomware attack is available here.
This is Lockbit’s second cyber attack on Thales this year. In January, when the first incident occurred, the corporation similarly declined to pay the demanded ransom. Hundreds of Zip archives were disclosed by the group at the time, the most current of which was from January 1, 2022. The leaked files included internal code, explains Security Affairs.
These 1,320 files were no longer available for download on Tuesday morning. (…) Thales group acknowledged the exfiltration of data and specified that “most of the stolen files which appear to have been copied from a code repository server (“code repository”), hosting data with a low level of sensitivity and which is external to the group’s main information systems.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








