Contents:
Threat analysts have recently noticed a surprising tendency in ransomware gang strategies. According to them, the initial stages of victim extortion are becoming less visible to the public, as cybercriminals prefer to use concealed or anonymous entries.
The fact that the ransomware groups do not reveal their target’s identities right away gives them a longer period of time to negotiate the ransom payment in secrecy while still putting pressure on the victims threatening to leak the stolen data.
The Q1 2022 ransomware study from KELA, an Israeli cyber-intelligence firm, explains this trend and outlines multiple changes in the field:
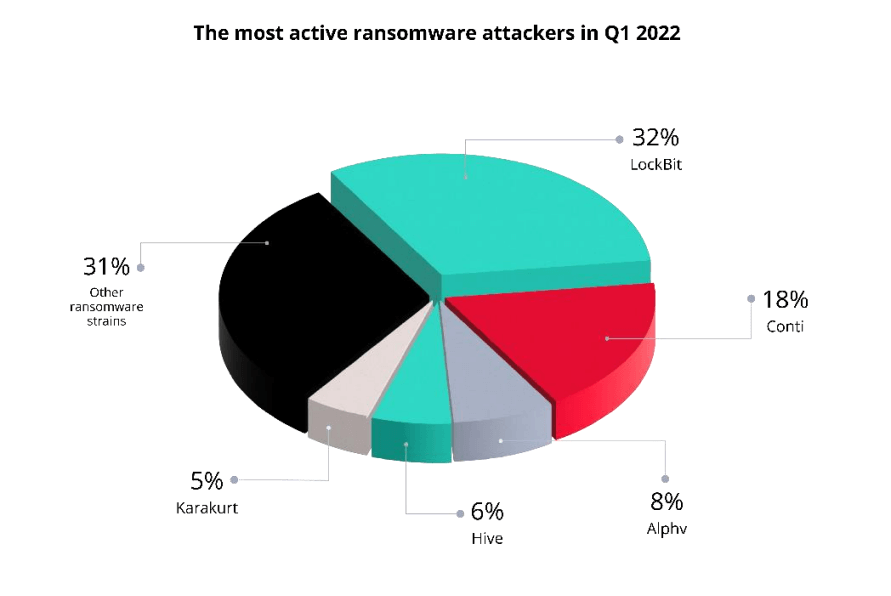
As per the report, the total number of companies that fell victims to ransomware attacks (698) dropped by 40% in Q1 of 2022 compared to Q4 2021 (982), with LockBit dethroning Conti as the most active cybercrime organization since the beginning of the year.
The number of attacks carried out by the Conti ransomware group decreased in January 2022 but increased after Conti’s internal data was publicly revealed.
LockBit, the most widespread and well-known ransomware threat, reported 226 victims, nearly identical to the previous quarter.
LockBit, Conti, Alphv, Hive, and Karakurt (recently discovered to be a side operation of Conti) were the most productive ransomware organizations in Q1, each reporting more than 30 victims.
Most Targeted Industries
The most targeted sectors in ransomware attacks were:
- manufacturing & industrial products,
- professional services,
- technology
- finance
The finance sector made it to the top 5 attacked industries, with a rise of 40% in the number of victims compared to Q4 of 2021. The LockBit gang was responsible for 40% of the 46 attacks.
Top Targeted Countries
The US is the most targeted country, impacted by nearly 40% of ransomware attacks in Q1, followed by organizations from the UK, Italy, Germany, and Canada. The report noted a minor difference from the previous year: France was among the top five countries in Q4 of 2021, but Italy took its place in Q4 of 2022.
New Tactic: the Victim’s Names Are Hidden
The strange phenomenon that emerged in Q1 2022 is that now ransomware groups keep their victims’ names secret and only describe them by their sector, size, and stolen data.
According to the report, Midas, Lorenz, and Everest ransomware gangs used this technique, threatening the target that they would add their brand name to the extortion Tor site if they failed to pay the requested ransom.
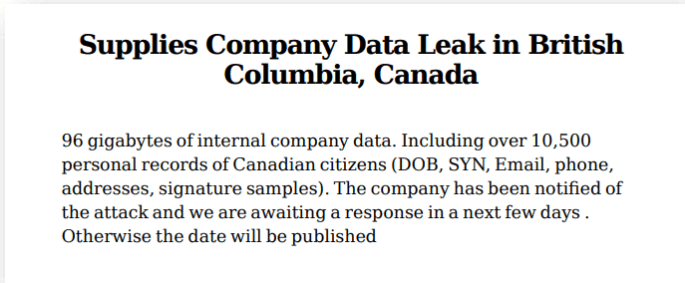
Other ransomware groups use this strategy as well, creating hidden web pages on their data leak sites and providing the URL only to the victim. This way, the threat actors show evidence of the data that has been collected without compromising their negotiating position.
When a ransomware gang discloses the identity of their victim right away, they usually minimize the chance of successful negotiation and receiving the ransom.
Cybercriminals may have discovered that it is essential to have a more cautious and protected strategy, at least in the early stages of the extortion.
If Ransomware Concerns You…
Join us on Tuesday, June 21st, 1pm BST/2pm CEST for our next webinar, when Cyber-Security & Heimdal Product Expert Andrei Hinodache and Pre-Sales Engineering Manager Robertino Matausch will explain why ransomware is on the rise, and how should executives evaluate their company’s ability to prevent and recover from ransomware attacks.
What’s more, we will be showing you how to do this LIVE! Our experts will walk you through ransomware incident preparedness, technical testing through live simulations, detection, and suggestions for thwarting attackers by hardening systems and infrastructure.
Make sure you register here!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










