Contents:
Threat actors are leveraging TeamViewer to gain initial access to the endpoints of organizations and attempt to deploy encryptors based on the leaked LockBit ransomware builder.
Being one of the most popular remote access tools, used by enterprises from all over the world, TeamViewer is also cherished by scammers and ransomware actors, who use it to gain access to remote desktops to drop and execute malicious files unbothered.
Threat Actors and TeamViewer
Security researchers conducted tests on two compromised endpoints, and analysed log files (connections_incoming.txt). The results of the analysis showed connections from the same source in both cases, indicating a common attacker.
The researchers discovered several employee accesses to the first compromised endpoint in the logs, demonstrating that the staff was actively using the program for proper administrative functions.
The logs for the second analysed endpoint, which has been operational since 2018, showed no activity for the previous three months, suggesting that it was not being watched as often, which would have made it more appealing to attackers.
The attackers attempted to use a DOS batch file (PP.bat) on the desktop to launch a DLL file (payload) using the rundll32.exe command in order to distribute the ransomware payload in both instances.
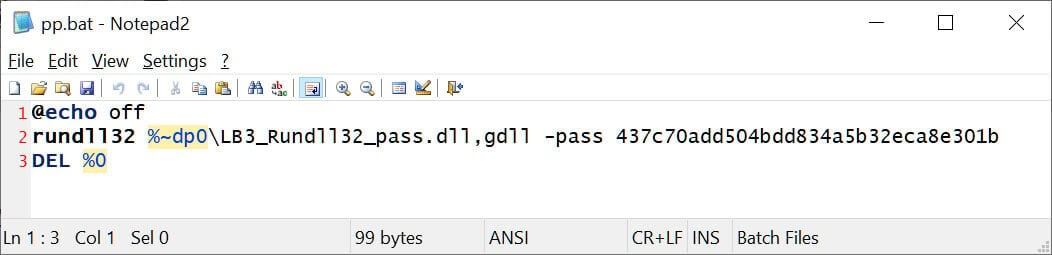
The PP.bat File Used by the Threat Actors to Execute the Ransomware Operation (Source)
The attack on the first endpoint succeeded but it was quickly contained. While on the second one, the antivirus managed to stop the effort, forcing repeated payload execution attempts with no success.
Although cybersecurity researchers haven’t been able to positively identify any ransomware groups as the source of the attacks, they have noticed similarities with LockBit encryptors made with a leaked LockBit Black constructor, which leaked back in 2022.
You may make several variants of the encryptor with the leaked builder, such as an executable, a DLL, and an encrypted DLL that needs a password to open.
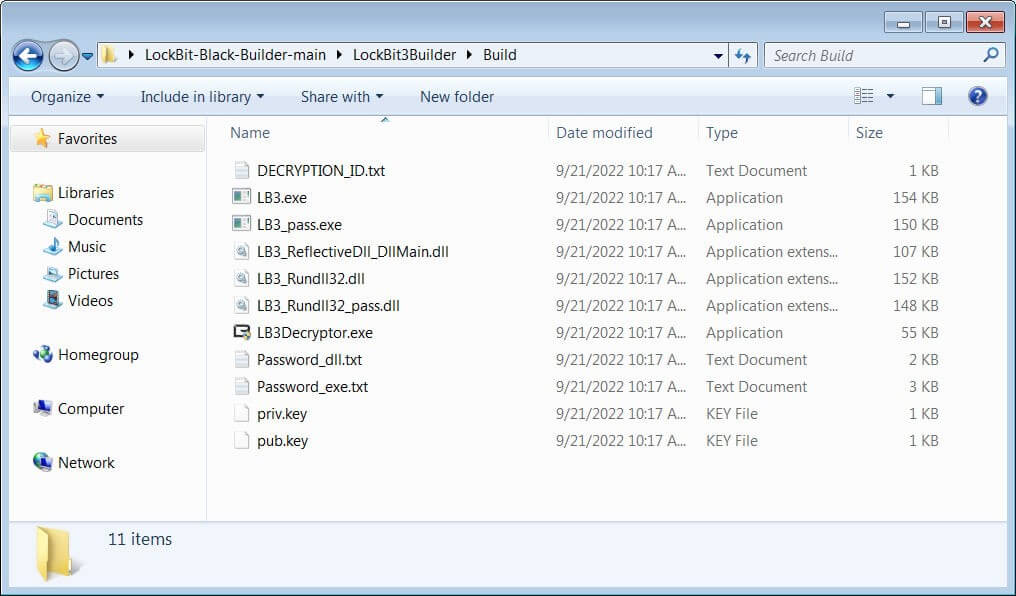
The Leaked LockBit 3.0 Builder (Source)
Based on the IOCs, the attacks distributed through TeamViewer appear to be using the password-protected LockBit 3 DLL.
TeamViewer Addresses the Situation
In a statement shared with cybersecurity news website BleepingComputer, TeamViewer declared that they take the security and integrity of their platform extremely seriously and condemn any form of malicious use of their software.
Our analysis shows that most instances of unauthorized access involve a weakening of TeamViewer’s default security settings. This often includes the use of easily guessable passwords which is only possible by using an outdated version of our product.
TeamViewer (Source)
The company also emphasized the importance of maintaining strong security practices, such as using complex passwords, enabling multi-factor authentication (MFA), allow-lists, and regular patching and updates.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








