Contents:
Once more, the banking trojan dubbed TeaBot was discovered in the Google Play Store, this time disguised as a QR code app that spread to over 10,000 devices.
This is a gimmick that the malware operators used in January, and despite Google’s removal of these entries, TeaBot appears to have made it into the official Android app store once again.
As per a report from Cleafy, a company that helps banks and financial institutions scale up their fight against online fraud, these applications are acting as droppers.
Furthermore, the trojanized apps include the promised functionality, resulting in positive user reviews on the Play Store.
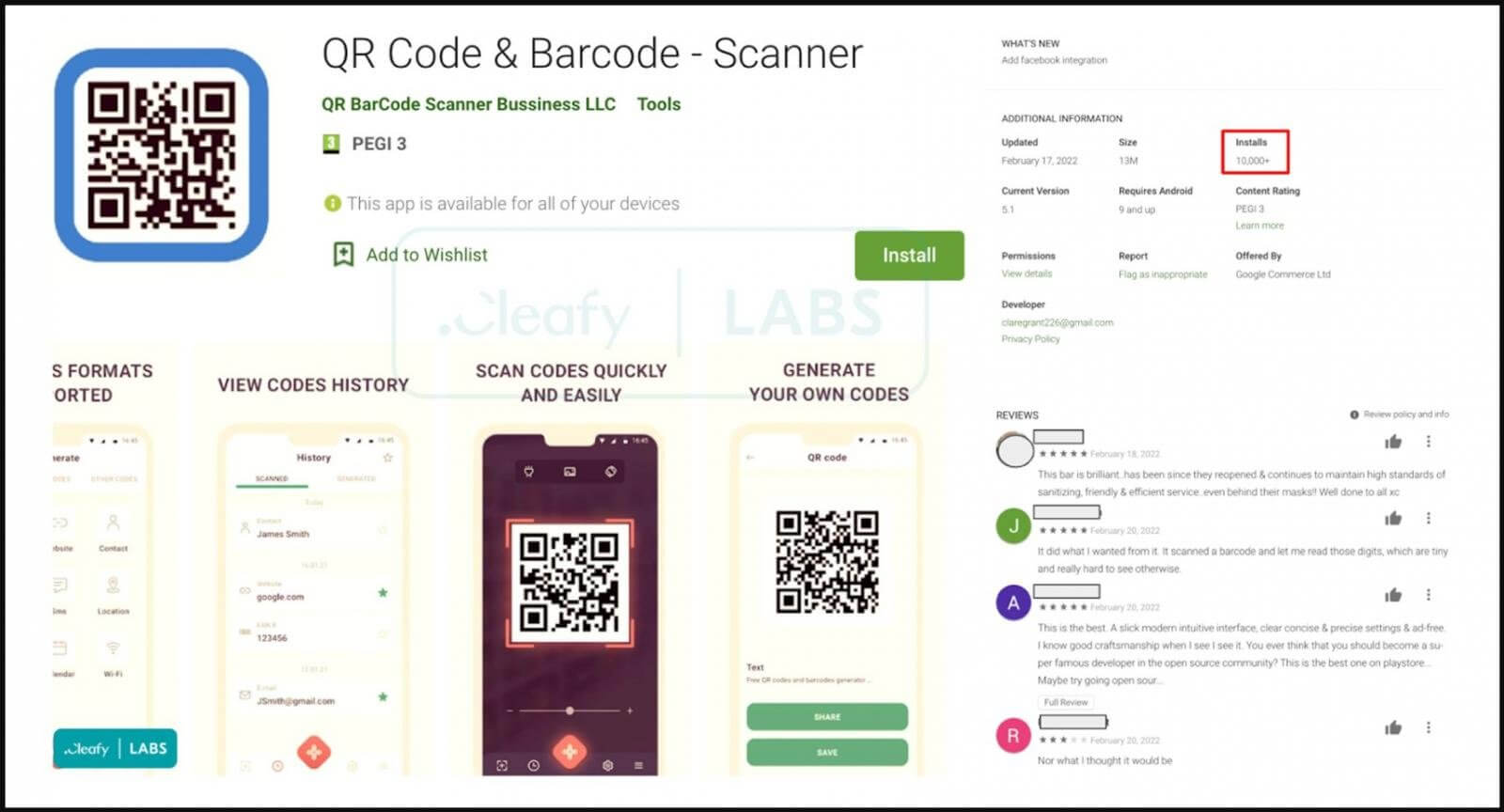
As explained by BleepingComputer, following its installation, the application asks for an update via a popup message, but contrasting with the usual procedure imposed by the Play Store rules, the update is fetched from an external source.
The download source was traced back to two GitHub repositories belonging to the same user (feleanicusor), which contained numerous TeaBot samples, uploaded on February 17, 2022.
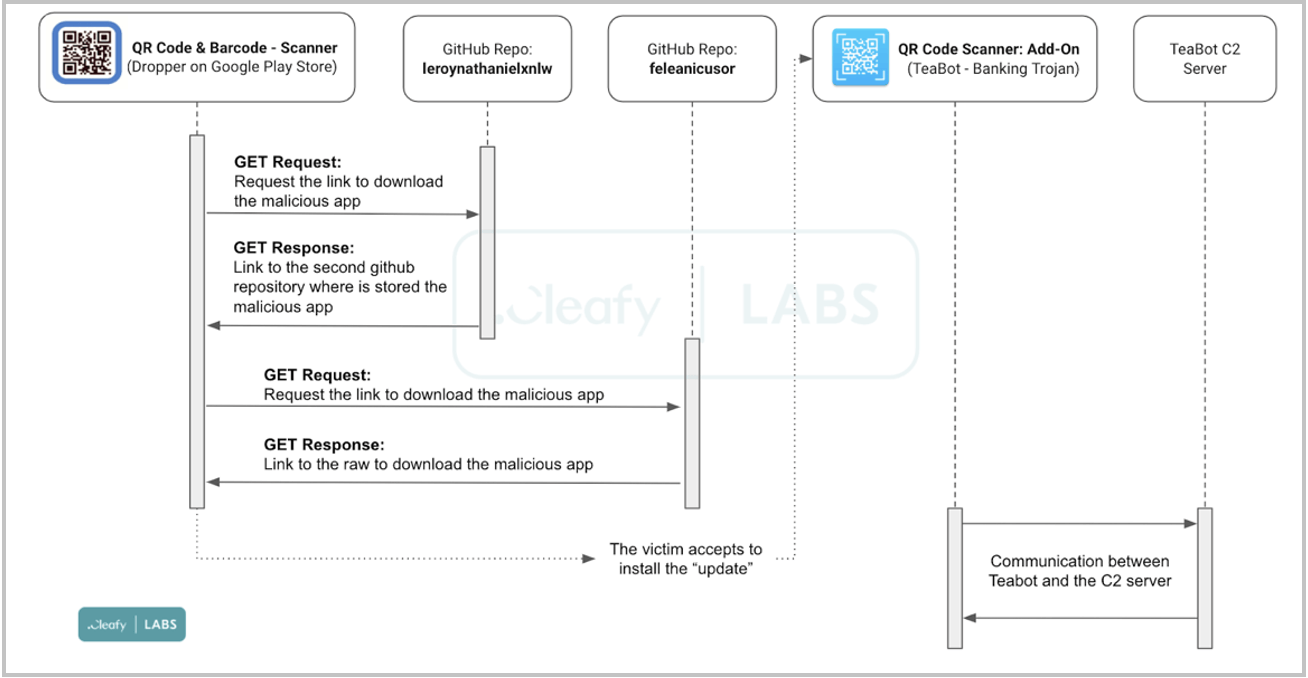
How Does It Work?
When the victim approves the installation of an update from an untrusted source, the TeaBot banking trojan is installed on their device as a new app called ‘QR Code Scanner: Add-On.’
The new app launches automatically and asks for permission to use the Accessibility Services in order to visualize the device’s screen and capture screenshots that disclose logins, 2FA codes, text messages, and other sensitive information.
It will also perform actions in the background, such as auto-granting additional authorizations, without needing user interaction.
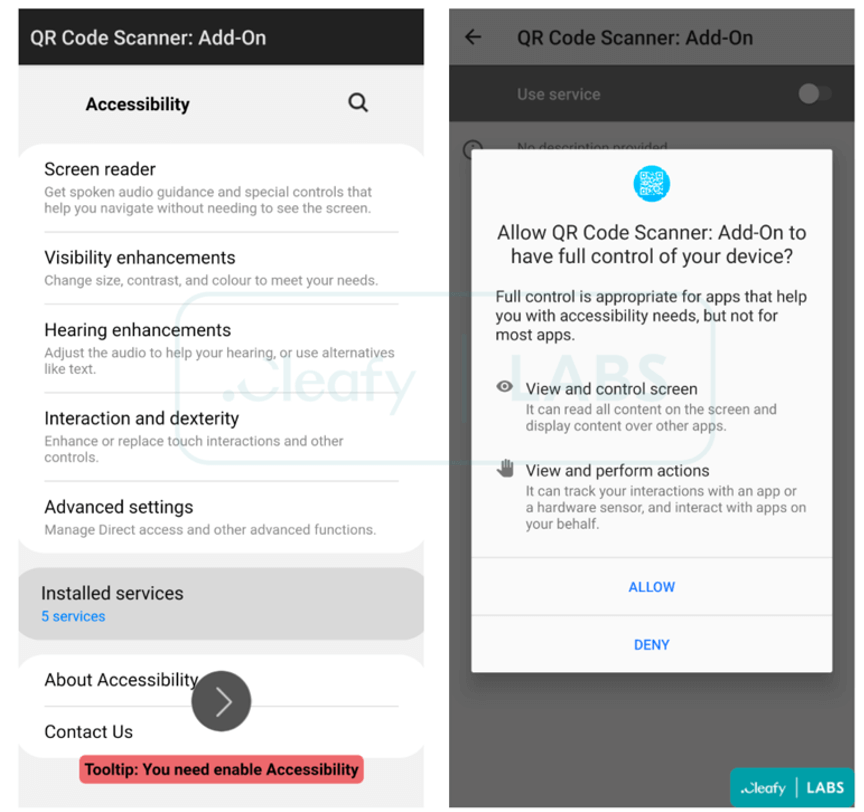
Although Google has made some security-minded API changes to the Accessibility Service in Android 12, this continues to be the most commonly abused permission by banking trojans.
TeaBot Targets More Countries
The banking trojan is now actively focusing on users in the United States, also adding Russian, Slovak, and Chinese languages, suggesting that the malware is targeting a global audience.
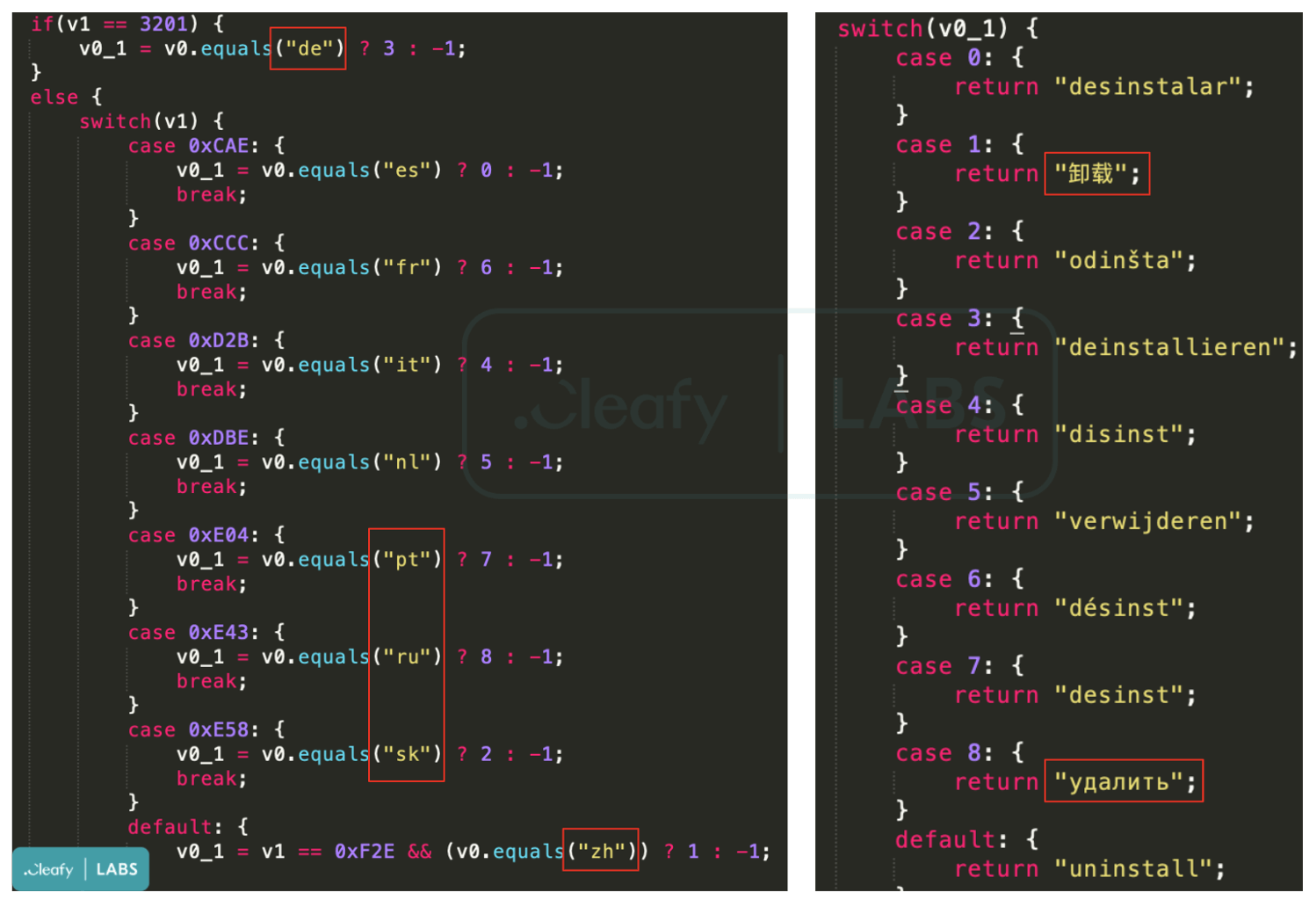
After being “tested” on smaller markets for a while, it’s possible that TeaBot’s developers now believe their tool is ready for larger-scale operations.
To reduce the possibility of infection from banking trojans even when using the Play Store as your exclusive app source, keep the number of installed apps on your device at a minimum.
It’s also a good idea to keep an eye on your device’s battery consumption and network traffic volume for the first few days after installing a new app to observe any dubious patterns.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








