Contents:
A phishing campaign poses as a Trezor data breach notification order to steal a target’s cryptocurrency wallet and assets.
Trezor is a hardware cryptocurrency wallet that allows users to store their cryptocurrency offline rather than in cloud-based or device-based wallets. Because the wallet is not meant to be connected to your PC, it offers protection from malware and compromised devices.
Users are given a 12- or 24-word recovery seed when they set up a new Trezor wallet, which can be used to recover a wallet if it is stolen, lost, or malfunctions. However, anyone who obtains access to this seed can also restore the wallet on their own devices, making them attractive targets for threat actors.
Phishing Campaign Targeting Trezor Users
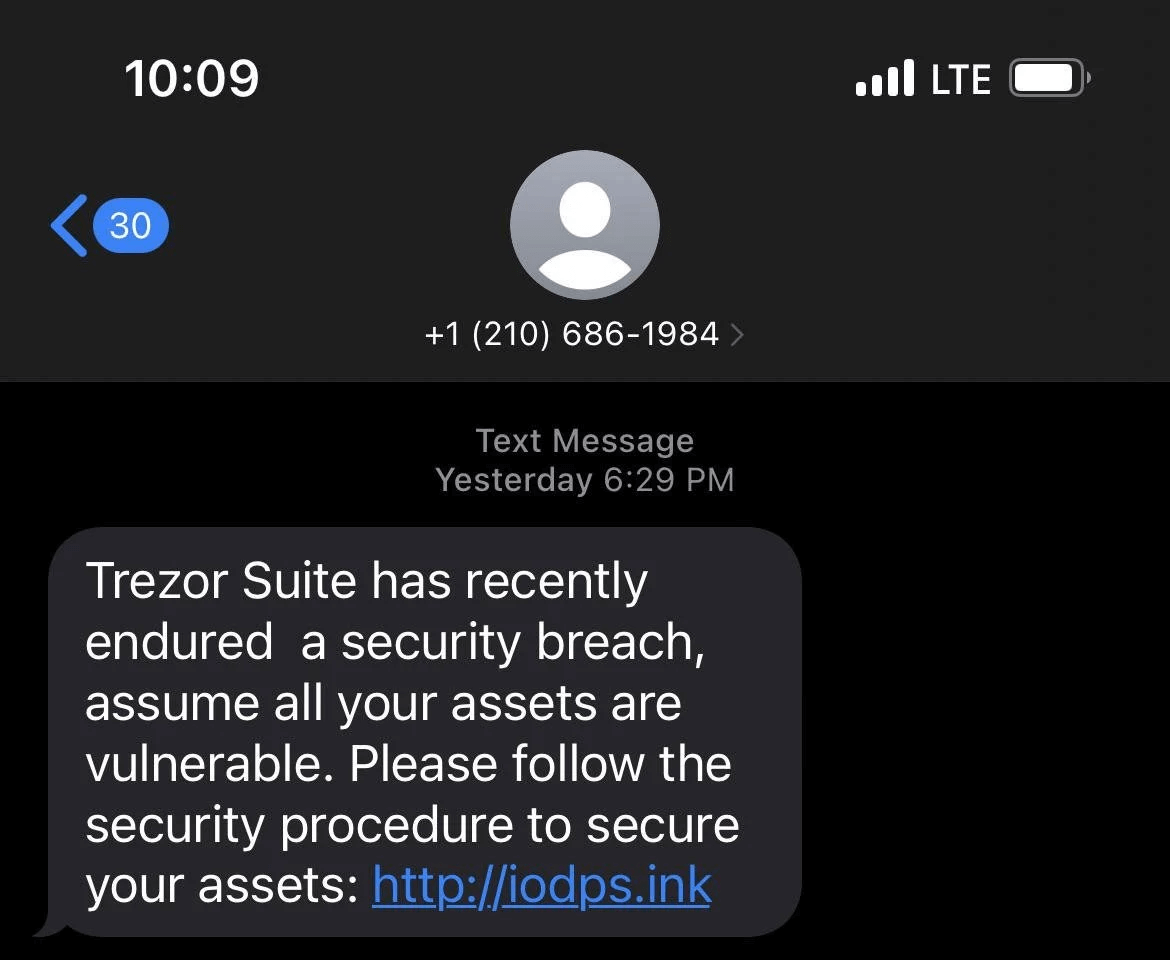
Trezor customers began receiving SMS and email phishing messages on February 27th, claiming the company had suffered a data breach. These messages direct the target to a specific website to secure their device.
Because Trezor Suite recently suffered a security breach, all your assets are at risk. Therefore, please follow the following security procedures to protect your assets: [phishing-site].
Reads the fake Trezor data breach warning messages.
One of these phishing texts was also sent to BleepingComputer. As shown below, a security researcher named Mich has also been receiving and reporting the numerous SMS phishing texts.
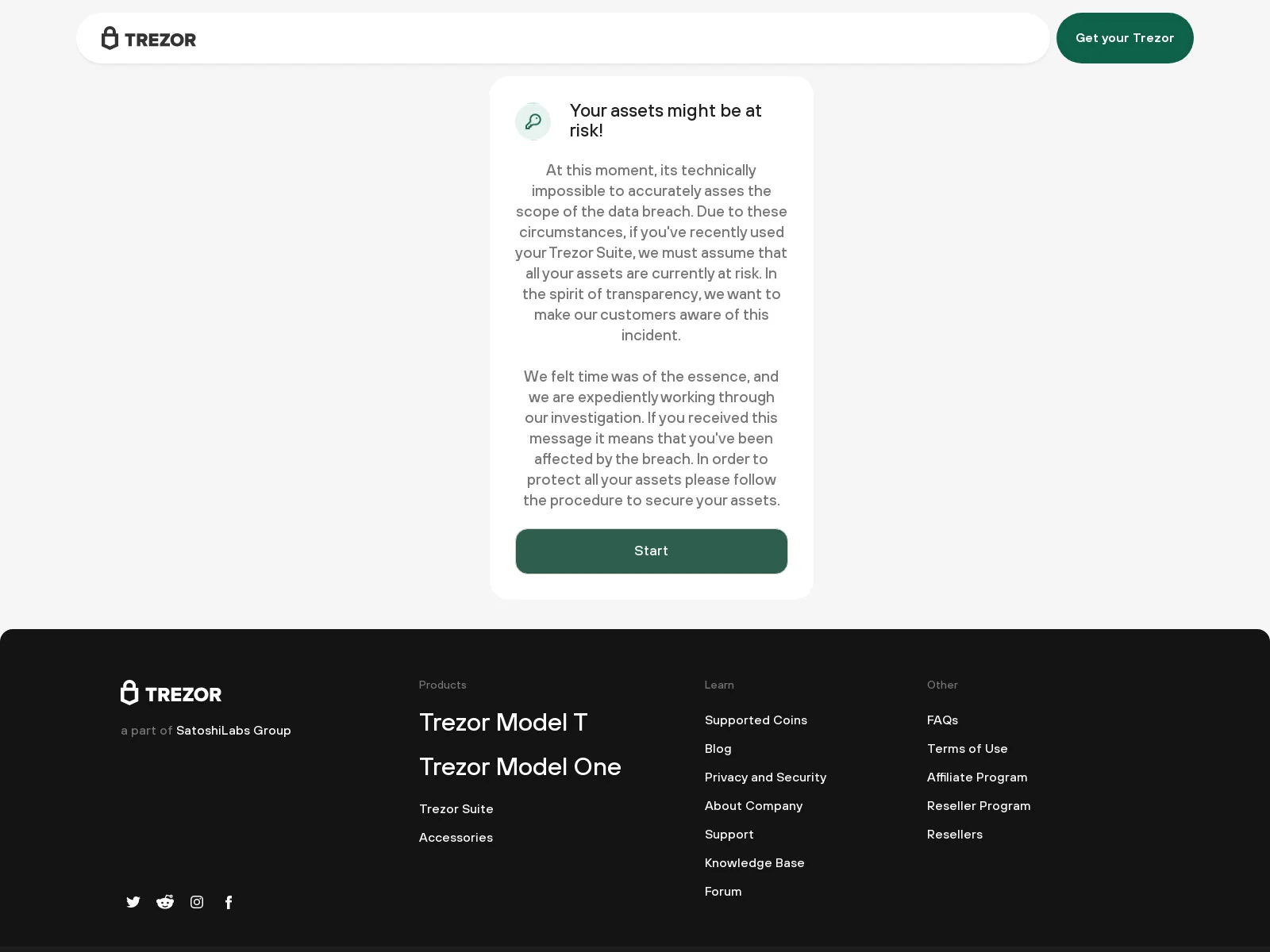
When visiting the listed domain, visitors will be directed to a bogus Trezor website that declares, “Your assets may be at risk!” and then prompts them to begin securing their wallet.
When users click the ‘Start’ button, they will be prompted to enter their recovery seed, which the threat actors will steal.
Once a recovery seed is stolen, the wallet owner is out of luck, as the threat actors will almost certainly transfer any assets to another address under their control.
The moral of the story? Never share your wallet’s recovery passwords, seeds, or phrases with anyone else, and never enter them on any websites.
The company warns users to be wary of phishing SMS texts and email warnings of a fake data breach. They have not found any evidence of a recent breach in their systems.
? Beware of the active phishing scam!
The attackers contact the victims via phone call, SMS and/or email to say that there’s been a security breach or suspicious activity on their Trezor account.
➡️ Please ignore these messages as they are not from Trezor. ⬅️
More info in?? pic.twitter.com/nzfSzfwcZ1
— Trezor (@Trezor) February 28, 2023
While it is unclear how threat actors are obtaining Trezor customers’ phone numbers and email addresses, they may be using a marketing list stolen in a MailChimp breach. The threat actors stole data from 102 MailChimp customers, mainly from cryptocurrency and finance companies.
In April 2022, threat actors sent a massive wave of fake data breach notifications, leading to a fake Trezor Suite website. This Trezor Suite would prompt the user to enter their recovery seed, which was then returned to the threat actors.
No fake software is being used in the current phishing campaign, but the threat actors are still trying to steal your recovery seed. Therefore, as we said earlier, never share your recovery seed with anyone.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security