Contents:
A new vulnerability has been found by security researchers. Dubbed StackRot, the Linux Kernel flaw is impacting versions 6.1 through 6.4.
The flaw is tracked as CVE-2023-3269 and is a privilege escalation issue. An unprivileged local user can trigger the flaw to compromise the kernel and escalate privileges.
As reported by BleepingComputer, responsible for discovering and reporting the vulnerability is security researcher Ruihan Li. He explains in a post that the flaw affects the kernel’s memory management subsystem, a component in charge of implementing the virtual memory and demand paging, memory allocation for the kernel’s needs, and the user space programs, as well as mapping files into the processes’ address space.
Understanding StackRot: Details on the Vulnerability
StackRot arises from the Linux kernel’s handling of stack expansion within its memory management subsystem, tied to managing VMAs (virtual memory areas).
The “maple tree,” a new data structure system for VMAs introduced in Linux kernel 6.1 that replaced the “red-black trees” and relied on the read-copy-update (RCU) method, is specifically the weak link.
Due to the way stack growth was handled, the maple tree was able to change a node without getting the memory management (MM) write lock, creating a use-after-free (UAF) issue.
In the “maple tree,” a new node is produced as the Linux kernel increases the stack and closes the space between VMAs, and the old one is flagged for deletion once the current reads are complete because of the maple tree’s RCU safety. However, a use-after-free problem could arise when a process accesses the old node within the RCU grace period, establishing an exploitable environment for privilege escalation.
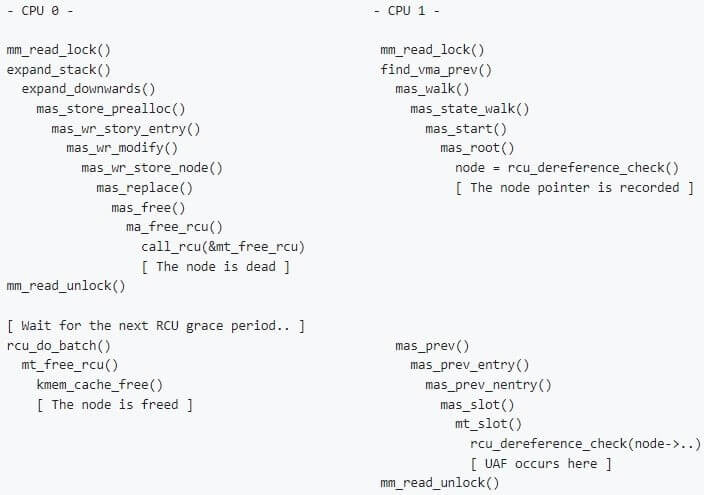
Race Condition in a Multi-CPU System Which Results in UAF Flaw (Source)
Ruhan Li notes that exploiting StackRot is a challenging task and that this vulnerability may be the first example of a theoretically exploitable use-after-free-by-RCU (UAFBR) vulnerability. The researcher announced that by the end of July, he plans on disclosing the complete technical details about StackRot and a PoC (proof-of-concept) exploit.
A patch is available for the affected stable kernels since July 1st, and we strongly advise you to patch the flaw as soon as possible. To be sure you are always protected against vulnerabilities, we recommend opting for an automated patch management solution, like our Heimdal®’s Patch & Asset Management solution. You can book a demo to see for yourself how our solution will improve your organization’s security.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










