Contents:
In a spear-phishing campaign, Truist Financial Corporation has been impersonated by cybercriminals trying to spread malware that seemed to look like remote access trojan (RAT), a program used by hackers to take complete control of the victim’s computer to perform malicious activities.
Truist Financial Corp. is one of the largest banks in the United States operating 2.049 branches in 15 states that offers consumer and commercial banking, securities brokerage, asset management, mortgage, and insurance products and services.
According to the FBI, the unknown cybercriminals also adapted the campaign “to spoof the financial institution through registered domains, email subjects, and an application, all appearing to be related to the institution.”
The Private Industry Notification has been coordinated with DHS-CISA being created to help cybersecurity specialists and system administrators protect against threat actors’ malicious activity.
In February 2021, a US-based bank was informed of a spear-phishing endeavor that mimicked the financial organization’s brand to attack a renewable energy enterprise.
The phishing email’s concept required funding for a loan and ordered the receiver to download a Windows app to finish the loan process to obtain more than $62 million.
The fraudulent loan amount was in line with the victim’s business model. The phishing e-mail also contained a link to download the application and a username and password for access.
The phishing e-mail appeared to originate from a United Kingdom-based financial institution, stating the US financial institution’s loan to the victim was confirmed and could be accessed through an application which appeared to represent the US financial institution.
The attackers stored the Windows app reproduction on an illegal domain they registered before the attack and impersonating the financial institution.
It appears that Truist wasn’t the only financial organization involved in these types of attacks. MayBank, FNB America, and Cumberland Private seem to have also been impersonated in this spear-phishing campaign.
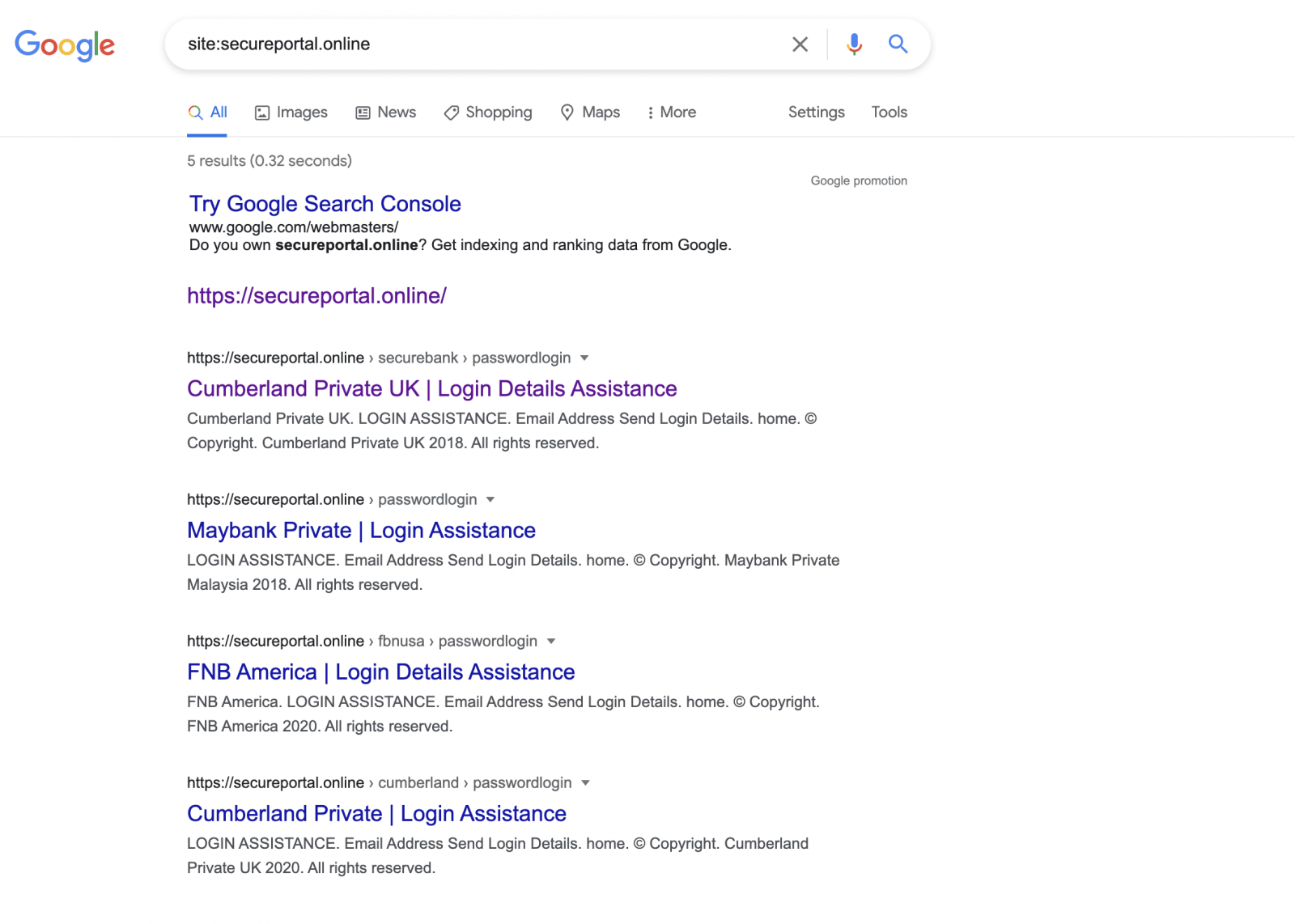
The threat actors employed malware that can’t be noticed by anti-malware machines on VirusTotal in order to increase their cyber assaults’ success. The malware used after the recipients download and install the malicious executable in the spear-phishing emails connect to the secureportal(.)online domain.
Apparently, threat actors can utilize the malware to register keystrokes and screenshot victim’s screens.
According to VirusTotal, the malware’s list of capabilities includes:
- Privilege escalation
- Communications over UDP network
- System registry manipulation
- Screenshot grabbing
- Listening for incoming communication
- Running a keylogger
- Communicating using DNS
- File downloader/dropper
- Communications over HTTP
- Code injection with CreateRemoteThread in a remote process
In order to protect your business from spear-phishing attacks, the FBI recommends:
- Well-maintained anti-virus software may avert employment of frequently used attacker tools distributed through spear-phishing so make sure you enable anti-virus and anti-malware software and signature definitions are updated regularly.
- Files downloaded via links in emails and attachments frequently include executable code. Use application control tools to limit users to only perform applications allowed by the organization.
- Restrict the use of administrator privileges. Spear-phishing is much more successful if users use email or browse the internet with admin privileges.
- Suspiciousness when receiving unrequested contact via social media or email from an unknown sender.
- Make sure to check the spelling of web addresses, websites, and email addressed that look reliable but can impersonate authentic websites.
- Make sure OPs and apps are updated to the latest version.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








