Contents:
Three cyber espionage campaigns have been discovered. The malicious campaigns were targeting networks belonging to major telecommunications companies from Southeast Asia.
As reported by Cyware.com, the researchers from Cybereason Nocturnus released a report regarding the cyber attackers that are believed to be aligned with Chinese interests.
The attackers are now being tracked as DeadRinger.
What Happened?
It seems that the attackers compromised centralized vendors in order to be able to target the network of major telcos.
The attacks are suspected to be carried out by APT groups associated with the Chinese nation-state.
The association might be possible due to the similarities discovered in the tactics and techniques used also with other Chinese APT groups.
It seems that the goal of the malicious campaigns was to target telecommunication companies in order to facilitate cyber espionage activities by gathering important information and subsequently target high-profile assets of the firms.
The Attack Campaigns
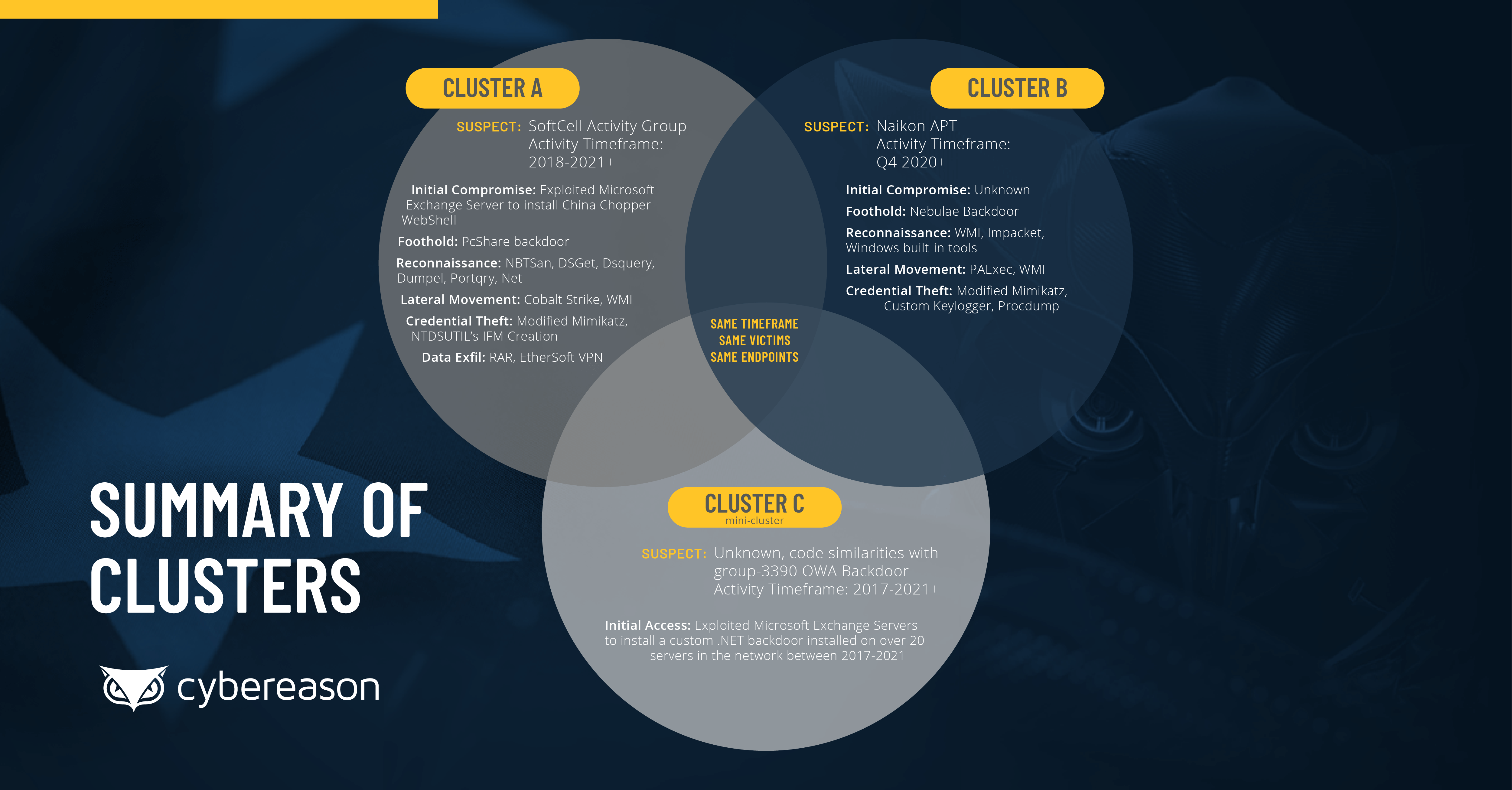
Experts discovered three clusters of malicious activity and traced the oldest attack back to 2017.
The First Attack
This attack was likely performed by the Soft Cell APT group. It is believed the attack started in 2018.
This threat group is active since 2012 and its attacks are probably aligned with the Chinese interests.
The Second Attack
This attack was allegedly linked to Naikon, the APT group that has been targeting telecommunication companies since the last quarter of 2020.
Naikon is suspected to have connections with the military bureau of the Chinese People’s Liberation Army (PLA).
The Third Attack
This campaign was linked to APT27, also known as Emissary Panda, and it was active between 2017 and the beginning of 2021.
The APT group was observed using a unique backdoor to target Microsoft Exchange servers.
The report published by Cybereason Nocturnus gives more information regarding the attack techniques used by the malicious actors.
The report details the exploitation of the Exchange Server vulnerabilities, the use of China Chopper, Mimikatz, and Cobalt Strike beacons, and backdoors with C2 for data exfiltration.
The APT groups are known to operate in the interest of the Chinese government.
It is concerning to note that the groups are considered to be adaptive, persistent, and evasive, as they worked diligently to obscure their activity and maintain persistence on the infected systems whilst dynamically responding to any mitigation attempts.
Another interesting fact is that similar to the HAFNIUM attacks, the threat actors were exploiting recently disclosed vulnerabilities in the Microsoft Exchange Servers.
The researchers are not sure though if the attack clusters are interconnected or operated independently from each other.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










