Contents:
Bitter, an APT group reportedly engaged in cyber espionage activities, has been observed targeting the Bangladesh government by leveraging new malware that shows remote file execution functionalities.
The campaign has been active since at least August 2021 and represents a good example of what the Bitter scope is.
Bitter APT Group Campaign: More Details
Threat analysts at Cisco Talos discovered and offered details about this malicious campaign in a report they published.
Considering C2 IP address overlaps with past campaigns, string encryption similarities, and methodology involved in module naming, the researchers attributed this campaign to the Bitter APT group.
The experts noticed two infection chains. Both of them began with a spear-phishing email and targeted different groups within the Bangladeshi government.
These emails come from false email addresses that seem to be from Pakistani government institutions.
This was most probably achieved by exploiting a bug located in the Zimbra mail server that let threat actors send messages from an email account/domain that did not exist.
What makes the difference between the two infection chains is the type of file attached to the malicious email: one includes an .RTF document, while the other contains an .XLSX document.
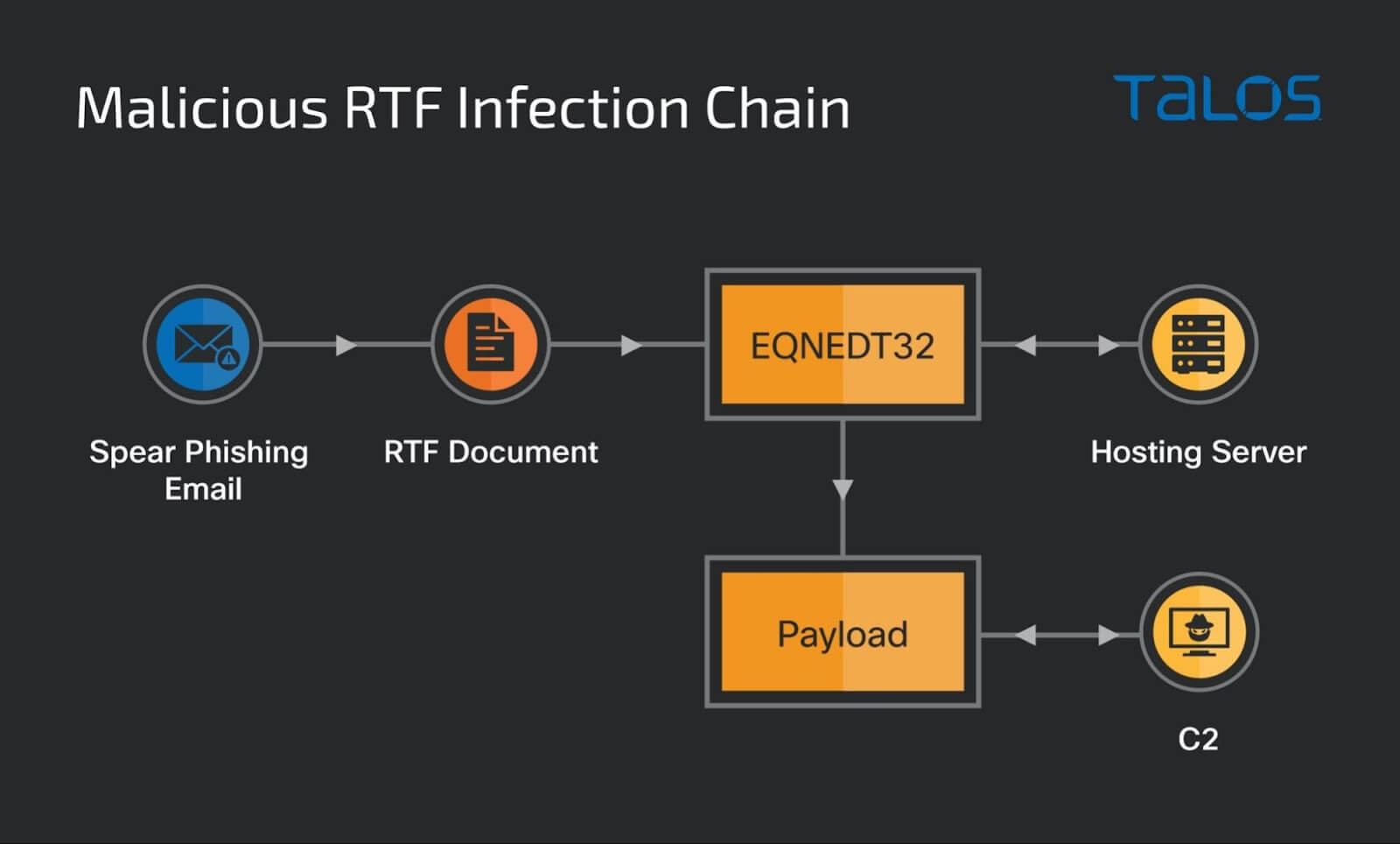
This campaign targets an elite unit of the Bangladesh’s government with a themed lure document alleging to relate to the regular operational tasks in the victim’s organization. The lure document is a spear-phishing email sent to high-ranking officers of the Rapid Action Battalion Unit of the Bangladesh police (RAB). The emails contain either a malicious RTF document or a Microsoft Excel spreadsheet weaponized to exploit known vulnerabilities. Once the victim opens the maldoc, the Equation Editor application is automatically launched to run the embedded objects containing the shellcode to exploit known vulnerabilities described by CVE-2017-11882, CVE-2018-0798 and CVE-2018-0802 — all in Microsoft Office — then downloads the trojan from the hosting server and runs it on the victim’s machine.
These emails are linked with call records and number verification associated with genuine government activities.
When you view an Excel worksheet, you activate an exploit for CVE-2018-0798 and CVE-2018-0802, which allows remote code execution on outdated Microsoft Office versions.
In this particular scenario, getting the payload is handled by two exploit-created scheduled tasks that connect to the hosting server and perform downloading of the trojan every five minutes after the first infection.
The experts depicted the malicious RTF infection chain in their report:
About the Trojan Dubbed ZxxZ
The trojan was dubbed ZxxZ by security analysts at CiscoTalos. It’s a 32-bit Windows program that downloads and runs modules with generic names like “Update.exe,” “ntfsc.exe,” and “nx.exe.”
We named the trojan “ZxxZ” based on the name of a separator that the payload uses while sending information to the C2. This trojan is a downloader that downloads and executes the remote file. The executables were seen with the filenames “Update.exe”, “ntfsc.exe” or “nx” in this campaign. They are either downloaded or dropped into the victim’s “local application data” folder and run as a Windows Security update with medium integrity to elevate the privileges of a standard user. The actor uses common encoding techniques to obfuscate strings in the WinMain function to hide its behavior from static analysis tools.
An information-stealing function is then activated, which dumps victim profiling data into a memory buffer and sends it to the command and control server (C2). The answer from the C2 is represented by a portable executable located in “%LOCALAPPDATA%\Debug\”.
If the ZxxZ malware does not manage to fetch that executable, it tries 225 more times before stopping.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










