Contents:
Cyberattacks are quickly becoming the pandemic of 2021, marked by major incidents on an unprecedented scale.
In December 2020, the SolarWinds supply chain attack provided hackers with access into as many as 18,000 government entities and Fortune 500 companies, as to at least nine federal agencies and more than 100 companies were exposed to the breach. This incident set the stage for others: the Microsoft Exchange server attack, the five-day shutdown of U.S fuel pipeline operator Colonial Pipeline, the ransomware siege of the Irish health services system, and more.
IronNet’s 2021 Cybersecurity Impact Report, based on interviews with 473 security IT decision-makers from the U.S., U.K., and Singapore, revealed that 90% of respondents said their cybersecurity had improved over the last two years, but 86% suffered attacks that required a C-level executives or boards of directors meeting.
According to the study, 85% of businesses surveyed felt the impact of the SolarWinds attack as follows:
- Significant impact: 31%
- Slight impact: 39%
- Small impact: 15%
- No impact: 15%
Financial Impact
The same report points out that on average, the impact of the SolarWinds cost companies 11% of their annual revenue.
U.S. companies reported an average of a 14% impact on annual revenue, while the averages in the U.K. and Singapore are at 8.6% and 9.1% respectively.
As a result, 81% of respondents answered they are more likely to share best practices, defensive techniques, and insights to help other organizations in their sector to achieve greater security.
Additionally, the survey found that 67% of companies have started to share information with tech industry peers, while 50% started sharing more information with government leaders.
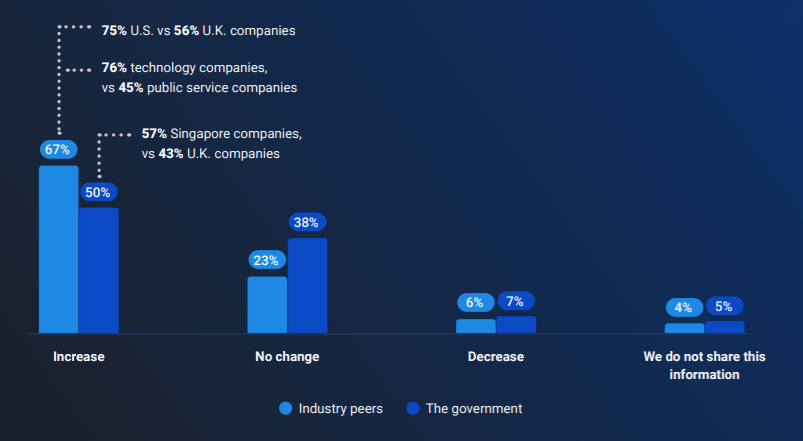
Image Source: IronNet
Singapore companies were most likely to share information with governments at 57%, followed by U.S. companies at 53% and U.K. firms at 43%. The factors that limited collaboration among industry peers include:
- Concerns about data privacy and liability (53%)
- The lack of an automated or standard mechanism to share information with peers (34%)
- The shared information may not be timely or relevant by the time companies receive it (33%)
The SolarWinds attack also forced companies to rethink supply chain security with 42% of companies having already implemented supply chain security.
Nine in 10 companies (91%) have re-evaluated the cybersecurity of their supply chain following the SolarWinds attack. IT security professionals think that better detection technology (44%) and better infrastructure for information sharing (41%) would have helped companies in the context of the SolarWinds attack. Almost all the companies (98%) agree that it is important to understand third-party risk within their business ecosystem.
Source: IronNet
How to Stay Safe
Traditional security solutions like Firewalls and Antivirus tools do not have sufficient capabilities to prevent security incidents on their own, this is why third-party software and Windows patch management strategies sustained by an ongoing patching process (alongside other layers of enterprise protection like DNS filtering, Privileged Access Management, and Advanced Email Security) become a vital requirement in today’s threat landscape.
Following the SolarWinds attack, Congress became interested in enacting a federal law requiring breach notifications. Last month, President Biden signed an executive order aimed to strengthen the federal government’s cybersecurity defenses.
A White House memo recommends corporate executives and business leaders take these steps to reduce the risk of cyberattacks:
I. Implement the key best practices from President Biden’s executive order
1) multi-factor authentication;
2) endpoint detection and response;
3) encryption;
4) a skilled, empowered security team.
II. Back up data, system images, and configurations, regularly test them, and keep the backups offline
III. Update and patch systems promptly
IV. Implement and test an incident response plan
V. Check the security team’s work
VI. Segment the networks


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










