Contents:
Software Asset Management is a critical aspect of any company’s cybersecurity posture. Read on to learn more about it and how to choose the best software asset management tool!
What Is Software Asset Management (SAM)?
SAM is defined as a business technique that manages and optimizes the acquisition, deployment, maintenance, usage, and disposal of software products inside an organization.
Moreover, as Deloitte adds, any SAM “includes all the necessary processes and infrastructure to plan, control, and protect your investments in enterprise software throughout each phase of the lifecycle.”
Therefore, software asset management is more than an app inventory tool; it is a framework that covers all software key areas: acquisition, deployment, usage, audit, retirement, and EOL.
Key Aspects of Software Asset Management
Licenses
Licenses are the foundation of SAM. Licensing is an asset that must be properly handled. Each license specifies the terms under which the software application can be installed and used, and any company must abide by the licensing agreement’s terms and conditions.
Compliance is the foundation of SAM. Software companies do not want you to use more software than you are licensed to. Despite the fact that SAM is far larger than compliance, compliance is the point at which license management becomes an integral aspect of your business strategy. And it’s the primary goal for most businesses when they begin using SAM.
Audits
Vendors may do software compliance audits to verify how their product is being used, how it is installed, and whether your licensing covers everything. An audit can result in one of two outcomes: compliance or noncompliance.
Noncompliance can lead to some serious fees, which can add up quickly if you’re not careful. An audit also interrupts your business and might go on for months without the assistance of licensing management technologies.
Optimization
Companies that over-license to ensure compliance end up paying for unnecessary maintenance in the long run. That inevitably leads to continuous additions. With SAM methods, this can be decreased or removed entirely.
SAM techniques also provide a high return on investment and help businesses save time through automation. By removing manual updates from the SAM process, SAM tools can help to avoid problems.
SAM and ITAM
Just as SAM is the framework for acquiring, operating, maintaining, and disposing of software, ITAM “entails the management of the physical components of computers and computer networks, from acquisition through disposal.” From container to ‘containee’ and containerization, everything in a company is an asset, and every little asset is subjected to policies.
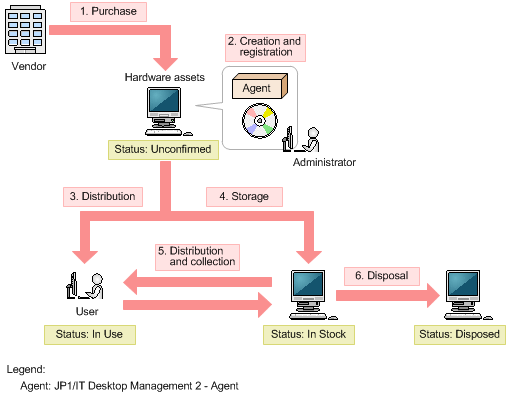
ITAM has, more or less, the same ruleset as SAM. The only thing that sets them apart is the financial aspect. Evidently, a piece of equipment does not amount to the same face value as a piece of software, all the more reason why your business case should be on point when recommending X hardware over Y hardware. Here’s what a typical ITAM flow looks like:
ITAM and SAM flows are, more or less, the same. Translated, the diagram above would read something along these lines – ITAM is a six-phased process: acquisition, creation & registration, distribution, storage, distribution & collection, and disposal. I would also add planning, ops, and maintenance to the flow.
Software asset management and IT asset management can both be viewed from a cybersecurity perspective. In this case, an asset equates or amounts to a potential vulnerability, one that can endanger privacy, compliance, and data integrity.
Software Life Cycle in the SAM Framework
Planning
The very first rule of software asset management is to conduct a minute inventory of what you have.
This includes software running on your desktop PCs, laptops, wearables, servers, IoT devices, routers, hubs, wireless access points, smartphones, tablets, and pretty much everything capable of running software – yes, even coffee machines and smart fridges fall into that category. Now that all your eggs are in the same basket, it’s time to make some determinations. These assumptions will help you move the ‘needle’ in the right direction. At this point, something visual like a checklist, a process tree, or a brain map can really speed up the process. Here are a couple of pointers to get you started:
- How many ACTIVE endpoints does your organization have?
- How many endpoints are COMPANY-OWNED? How many are BYODs?
- How many software apps are running on your endpoints?
- How many of those are company-sanctioned and how many are in violation of your company’s policies?
- How many endpoints are running unpatched or outdated software?
- How long will it take to deploy updates and security patches on all your endpoints?
- How many endpoints can pass off as major security risks?
- Can you measure software efficiency? If so, are the apps actually helping employees carry out their daily tasks, or do they create more bottlenecks?
- Cost vs efficiency in retiring EOLs and suboptimal software.
- What type of new software is required?
As you can imagine, the list is (almost) never-ending, and being disconcerted or getting lost in translation is actually fine and, why not, part of the process. Don’t forget that careful SAM planning can help you get rid of some nasty security and compliance issues.
Procurement
After having established the baseline, it’s time to tackle the procurement part. Now, buying new software is not as easy as going to the supermarket. It takes careful consideration and a whole lot of legwork – bear in mind that acquisition, in itself, is subjected to a workflow. Regardless of your acquisitions and pricing, you will probably need to make a business case.
Based on your recommendations, execs will determine if the investment is sound or a dead-end. On your end, please ensure that the need is real, all global deployment requirements are met, and that your business case features alternatives.
Operations & Maintenance
Provided that all went well during the planning and procurement phases, you’re now the proud owner of several new pieces of software. As part of the software asset life cycle, ops & maintenance is considered the longest and, sometimes, the most tedious. You will need to monitor everything, tend to hiccups, nurse broken apps back to health, and ensure that everything’s up to speed.
Ops & maintenance can also aid you in gauging the ‘life expectancy” of an app or suite; very important in figuring out if the worthiness of the investment.
Disposal
Is there software life after death? Yes and no – every piece of software, especially those of the open-source variety can be repurposed or recycled. Others just end up into, well, oblivion, I guess. Why is disposal important? Because EOLs and legacies become liabilities the moment the developing companies cease to release security patches and or updates. Those are entry points that can (and will) be used by malicious hackers to APT your networks and or endpoints.
To sum up: SAM or software asset management is a framework that describes the life cycle of every piece of software owned by a company. SAM frameworks may have slight alterations, but all of them rest on four major pillars: planning, acquisition, operations & maintenance, and disposal. Planning, acquisition, and disposal are less resource-intensive, while ops & maintenance are both resource-intensive and time-consuming.
How to Choose the Best SAM Tool for Your Company
Since there are many SAM solutions and service providers on the market and it might be difficult to make a responsible choice, here are a few things you should keep in mind before taking a decision:
- Consider the size of your firm before deciding on a SAM tool. SAM tools can help mid-size and large companies that use many programs and software licenses save time and money. Moreover, they will also help them control their application usage much more accurately.
- A SAM tool can be really beneficial to companies that were involved in a merger or acquisition, have several sites and are well-known on a global basis, and for those that have outsourced some of their operations.
- Consider your current systems, such as HR, IT asset inventory, and procurement, before selecting a SAM tool. Inquire with the SAM tool providers about integrating their product with yours. In addition, inquire about what features are available to better understand how the product will integrate into your existing infrastructure and how it will behave inside your firm.
How Can Heimdal™ Help?
Well, Heimdal™ Security’s Patch & Asset Management solution makes SAM easy, provides global patch or update deployment (for Microsoft, 3rd party and custom applications), and helps you compile inventory reports faster than you can say “software asset management”.
The system is totally customizable, operates as a set-and-forget for hyper-automated software and update distribution, and includes a full audit trail for increased compliance.
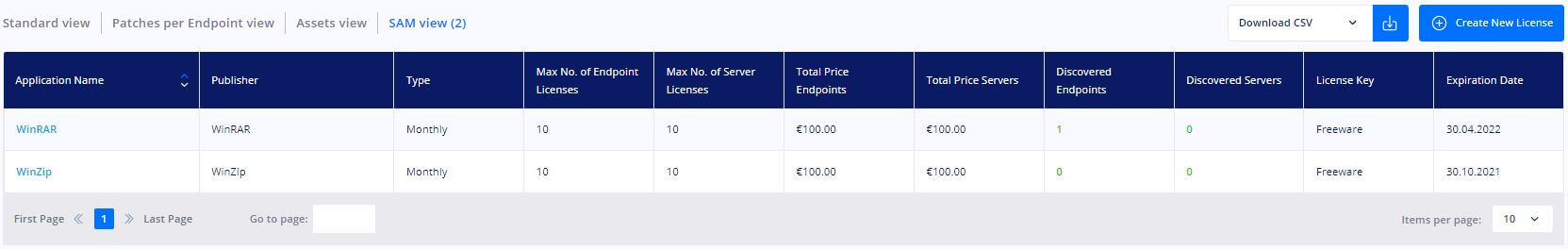
When it comes to software asset management, the Heimdal dashboard includes a specific view mode that shows a list of all software licenses identified on your organization’s endpoints. The Application Name, Publisher, Type, Quantity, Maximum number of Endpoint Licenses, Maximum number of Server Licenses, Total Price Endpoints, Total Price Servers, Discovered Endpoints, Discovered Servers, License Key, and Expiration Date are all displayed in this view.
Heimdal® Patch & Asset Management Software
Wrapping Up
As software is now a two-edged sword, both useful and important, but also burdensome – and even unpleasant – the software license agreements pile up, and suppliers’ audits get more aggressive. In this context, any firm can benefit substantially from software asset management if they select the right SAM tool.
Leave a comment below or contact us if you would like to clarify other aspects related to software asset management – or request a demo if you’d like to see for yourself how Heimdal’s Patch and Asset Management actually works.
P.S. Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security