Contents:
The threat actor also known as Fancy Bear, Sednit, Sofacy, Strontium, or PwnStorm, used the SkinnyBoy malware in order to target military and government institutions earlier this year.
SkinnyBoy seems to be intended to be used in an intermediary stage of the attack, to collect information about the victim and retrieve the next payload from the command and control (C2) server.
It looks like APT28 started this campaign at the beginning of March, and focused on the ministries of foreign affairs, embassies, defense industry, and military sector, with multiple victims being in the European Union but the activity may have also impacted organizations in the United States as well.
SkinnyBoy gets delivered through a Microsoft Word document laced with macros that manage to extract a DLL file and act as a malware downloader.
The lure used is represented by a message containing a spoofed invitation to an international scientific event held in Spain at the end of July, and by opening the invitation, the infection chain is triggered.
The infection starts with extracting a DLL that retrieves the SkinnyBoy dropper (tpd1.exe), a malicious file that downloads the main payload, and once it gets in the system it establishes persistence and moves to extract the next payload, that is encoded in Base64 format and appended as an overlay of the executable file.
The payload deletes itself after extracting two files on the compromised system:
- C:\Users\%username%\AppData\Local\devtmrn.exe (2a652721243f29e82bdf57b565208c59937bbb6af4ab51e7b6ba7ed270ea6bce)
- C:\Users\%username%\AppData\Local\Microsoft\TerminalServerClient\TermSrvClt.dll (ae0bc3358fef0ca2a103e694aa556f55a3fed4e98ba57d16f5ae7ad4ad583698)
In order to be able to keep a low profile, the malware executes the files at a later stage, after it has already created a persistence mechanism via a LNK file under the Windows Startup folder, with the LNK file being triggered at the next reboot of the infected machine and looks for the main payload, SkinnyBoy (TermSrvClt.dll), by checking the SHA256 hashes of all the files under C:\Users\%username%\AppData\Local.
SkinnyBoy’s main purpose is to exfiltrate any information about the infected system, download, and launch the final payload of the attack, which remains unknown at this time.
SkinnyBoy’s is collecting the data by using the systeminfo.exe and tasklist.Exe tools that already exist in Windows, therefore allowing it to extract file names in specific locations:
- C:\Users\%username%\Desktop
- C:\Program Files – C:\Program Files (x86)
- C:\Users\%username%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Administrative Tools
- C:\Users\%username%\AppData\Roaming
- C:\Users\%username%\AppData\Roaming\Microsoft\Windows\Templates
- C:\Windows – C:\Users\user\AppData\Local\Temp
All the information extracted is then delivered to the C2 server and encoded in base64 format. It’s interesting to note that the attacker used commercial VPN services to purchase elements for their infrastructure, a tactic used by attackers to better lose their tracks.
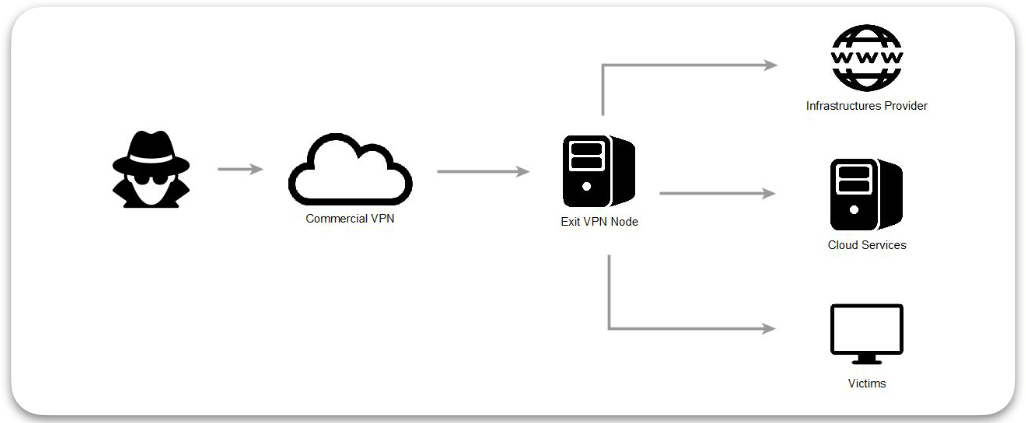
After observing the way in which Skinny boy operates, alongside its tactics, techniques, and procedures, researchers at Cluster25 believe that the implant could be a new tool from the Russian threat group known as APT28.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










