Contents:
Today, organizations around the world are facing a perfect storm of inflation, smaller budgets, rising labor rates, and slower consumer demand. Against that backdrop, hackers are only getting more active.
Businesses therefore have some difficult choices to make.
Do you continue to invest in an expensive team of security experts, despite the rising costs and tightening budgets? Or do you risk leaving your business open to fines and reputational damage by reducing your security spend?
Luckily, there is a third way: MXDR. But to understand why it’s so valuable to today’s businesses, it’s helpful to first recap why effective cybersecurity has become so tough.
Check out the full webinar: This article is based on a Heimdal webinar presented by our cybersecurity expert Andrei Hinodache. Check out the full recording to find out more.
Cyber Crime Is on the Rise
If you’ve been paying attention to the world of cybersecurity in the last few years, it’ll come as no shock to hear that cyber crime has soared.
In unstable economic times, the promise of a quick buck through a cyber attack is simply too attractive to too many.
But it’s one thing to know that cyber crime is rising, and another thing entirely to see the numbers and understand the implications.
In our recent webinar, Heimdal cybersecurity expert Andrei Hinodache summarized five examples of rising cyber crime between 2022-23:
- Initial access brokers – This refers to a hacker who gains entry to an IT environment, only to sell that access on to others, usually via an auction on the dark web. Between 2022-23, initial access broker activity on the dark web more than doubled.
- Botnet activity – A botnet is a network of infected computers that generally don’t know they’ve been hacked. These networks are used to launch distributed denial of service (DDOS) attacks or to spread malware across infected devices. Over the same period, we saw instances of botnet-distributed exploit command injections increase from 8% to 26%.
- Ransomware – We’ve also seen a worrying rise in ransomware attacks over the last few years. In fact, instances of ransomware that resulted in a public data breach increased by 113% between 2022-23.
- Phishing – Phishing is one of the most common methods that hackers use to target and infiltrate IT environments. As such, it’s a good proxy for the overall rise in malicious activity. In total, we saw a rise in phishing attempts of 130% – another worrying sign.
- Supply chain attacks – Supply chain attacks are some of the riskiest and most damaging attacks. The thought of these keeps even the most proactive security teams up at night. Again, evidence of these has only grown, with a 142% rise being seen between 2022-23.
Long story short: The hackers have been busy. If it’s your job to keep an IT environment safe, you’ve certainly got your work cut out for you.
But this isn’t the only reason that the task has grown harder.
At the Same Time, Cybersecurity Is Getting Tougher
It’s not just about rising cybercrime. Developments in the economy and the cybersecurity industry over the last few years have made it increasingly difficult and expensive to run an effective in-house security operation. There are a few reasons for this:
1. More Tools = More Confusion
According to research unveiled in our webinar, the average enterprise now uses a staggering 45 cybersecurity tools. For medium companies, the average is 15.
As cybercrime evolves, companies are relying on more and more tools to stay safe, each with a different goal, approach, and functionality on offer.
This can include everything from data loss prevention, antivirus, patching, DNS security, password managers… the list goes on.
But more products create greater cost and confusion. This is why 75% of organizations are now looking to consolidate security products to both improve cybersecurity and reduce their costs.
2. Budget Cuts
In challenging economic times, we almost always see a rise in cybercrime and fraud. But at the same time, organizations are cutting budgets across the board. Too often, that includes spending on IT and security.
This is a huge issue at a time when the need for cybersecurity is only growing.
3. Labor Costs
The workforce shortage is a global concern that spans nation states and industries. Estimates suggest that by 2030, there could be a global talent shortage of more than 85 million workers.
In just six years, the forum says this significant talent squeeze could lead to an estimated $8.5 trillion in unrealized annual revenue. If this sum was the GDP of a country, it would be the third highest in the world after economic superpowers the US and China.
Security isn’t just about tools and processes; it also requires skilled professionals to monitor the technology you’re using and respond to alerts. The larger the organization, the more important this becomes.
According to the World Economic Forum, the talent shortage in cybersecurity could reach 85 million workers by 2030, causing some $8.5 trillion in unrealized annual revenue.
This means it’s getting harder to find skilled cybersecurity professionals. Inevitably, that also means the cost of attracting them is only growing.
So in summary: The last few years have seen a huge rise in both cyber attacks – as well as the cost and complexity of defending against them.
Amidst this perfect storm, you could be forgiven for wondering how any organization can stay safe.
Luckily, there are other options.
MXDR Makes Life Easier for Time-Poor Security Teams
This is where managed extended detection and response (MXDR) comes in.
MXDR is uniquely placed to help you improve your cybersecurity posture, reduce complex licenses, and lower your overall costs.
But to understand why, it’s helpful to first recap what it is and how it works.
XDR Basics: Understanding Extended Detection And Response
By definition, XDR is a platform that covers more than just technology – it’s about unifying cybersecurity layers.
This is so important, because it lets us eliminate unnecessary PC resource overhead and the huge number of security tools you’re using. We also eliminate some of the worry with day-to-day management and implementation. And of course, we eliminate some of the costs. This has a huge impact on reducing complexity and improving overall security.
Andrei Hinodache, Cybersecurity Architect & Technical Product Marketing Manager, Heimdal
To understand MXDR, it’s helpful to first consider the technology it’s built on: extended detection and response (XDR).
This is a cybersecurity product that aims to help organizations reduce the number of conflicting, overlapping licenses they have and create a tighter, more focused, and more effective cybersecurity platform.
Generally, XDRs consolidate a range of products, including EDR, SIEM, antivirus/ransomware protections, DNS security, and more. Some XDRs consolidate more of these products than others.
At Heimdal, we offer the widest XDR product on the market, adding tools like vulnerability management, email security, privileged access management, and more to this list.
The main goal of an XDR is to consolidate the ever-growing web of disparate cybersecurity tools that today’s businesses increasingly rely on.
The principle benefit is simple: To reduce costs, complexity, and overlapping tools. But crucially, this can also significantly improve your overall security posture.
To see why, let’s pretend a hacker has infiltrated your IT environment and is planning an attack. To do that, they’ve taken a very common hacking journey:
- First, they infiltrate the IT environment via phishing;
- Then they aim to accumulate extra privileges by exploiting an unpatched vulnerability;
- After this, they move laterally through the environment to perform reconnaissance and cover their tracks.;
- Finally, they’ll aim to install ransomware.
Traditionally, each of these four actions is picked up by four different cybersecurity tools: email security, vulnerability managers, SIEMs, and anti-malware/EDR tools, respectively.
Each product has its own dashboard and analyzes different signals to determine risk. In this context, you’ll have four security tools responding to the same attack at different times and in different ways – with none of them having visibility over the whole journey the hacker has taken.
Crucially, the first few stages in this process might seem quite low risk in isolation – it’s only when you view the hacker’s journey as a whole that the true risk becomes clear.
XDRs aim to avoid these issues by consolidating cybersecurity tools into a single dashboard.
From there, you can create one effective and targeted policy to stop the hacker in their tracks.
Read more: Admin Rights in Action: How Hackers Target Privileged Accounts
Taking XDR to the next level
MXDR is the evolutionary step from EDR. With managed extended detection and response, you get a next-generation, advanced detection and response cloud platform that goes beyond the traditional level of technology – except it’s also fully managed by experts.”
Andrei Hinodache, Cybersecurity Architect & Technical Product Marketing Manager, Heimdal
So where does the M come in?
MXDR adds an extra level to the XDR package: A dedicated team of the best security professionals in the business to fully manage the security products you’ve invested in.
Here are some of the managed services we include as standard in our Heimdal MXDR offering:
- Ongoing monitoring – Dedicated security professionals monitor your security tools 24/7 to identify suspicious behavior, making it much easier to find the real danger amidst the noise.
- Realtime threat response – When risky behavior is detected, we have a range of tools and processes in place to quickly respond and lock down the relevant endpoint or account. See the next section for more details.
- Vulnerability management – The best teams (like Heimdal…) will also proactively monitor your network and endpoints to identify unpatched vulnerabilities that can be used to infiltrate your IT environment or accumulate extra privileges.
- Proactive analysis – We also monitor your software, activity, and settings to identify potential sources of infection, misconfigurations, and other issues.
Crucially, this list includes both reactive and proactive support – unlike many of the industry’s most well-known security providers.
Generally, they focus only on responding to threats when they’re detected – rather than configuring your IT environment to avoid them in the first place.
Outsourcing your security team is both cheaper and more cost-effective than hiring in-house security professionals.
In order to get 24/7 monitoring support, you’ll need several trained professionals working shifts – which only increases costs in an ever-tightening labor market.
Instead, an outsourced team can monitor every alert in realtime and create an effective, targeted response when issues arise.
And with a single, scalable monthly subscription – this is much more cost-effective than an in-house team.
Our 4-Step Process to Keep Your IT Environment Safe
If you’re considering investing in MXDR, you might be wondering how the security team would respond in a crisis.
After all, the most cost-effective service in the world is next to useless if it can’t actually keep your organization safe.
When evidence of an incoming attack is discovered, time is of the essence. For that reason, we have a clear policy for how your outsourced team will respond.
One crucial thing to remember is this: We won’t take any action on a client’s IT environment without express permission.
Instead, we’ll work with the client to develop ready-made response policies for common threats ahead of time.
If an attack starts and we haven’t already developed a policy, we’ll aim to get in touch with you as soon as possible to organize the response.
Nonetheless, with the client’s permission, there are a range of tools at our disposal to contain and eliminate the threat. This takes place over four main stages:
1. Initial Investigation
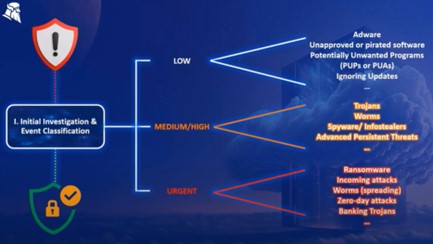
The first stage involves deciding what the relative risk of the incoming threat is. Since lower-risk threats will require a less urgent response, this decision will inform the actions we take in stages three through four.
- Low risk – These are issues that might be used to aid an attack at some point, including adware, use of unapproved or pirated software, potentially unwanted programs, PUPs/PIAs, or uninstalled updates.
- Medium risk – More immediate risks might involve trojans, worms, spyware or infostealers, and advanced persistent threats.
- High risk – The most urgent alerts usually include ransomware, urgent incoming attacks, evidence of worms spreading, zero day attacks, and banking trojans.
From here, we have a variety of choices for how we’re going to respond to the threat.
2. Take Action
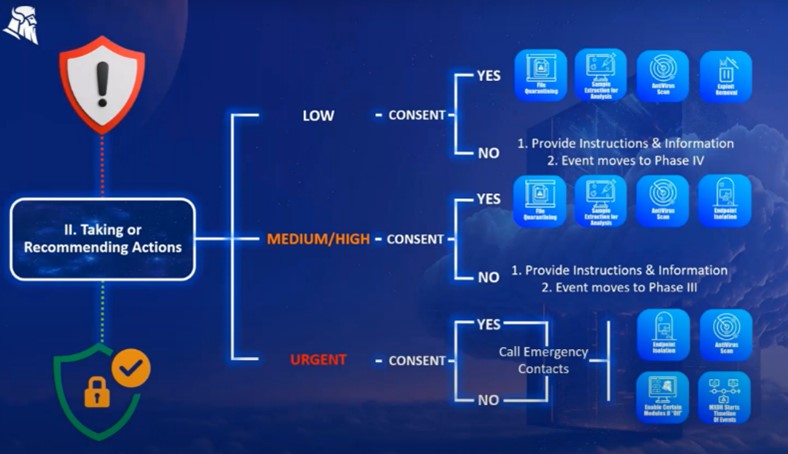
In stage two, our goal is to stop the immediate risk and prevent the threat from spreading. The specific actions we’ll take will depend on the risk profile we identified in the first stage:
- Low risk – When low risk threats hit, our options include quarantining files, extracting samples for extraction, running an antivirus scan, or removing an exploit. If we don’t have prior consent for these actions, we’ll provide a set of instructions and recommendations to the client, before proceeding to stage four.
- Medium risk – The options for medium risk attacks are quite similar – the only real difference is the urgency. With higher-risk threats, we may also isolate endpoints here – which isn’t generally needed for the low risk category. If we don’t have prior permission for these actions, we’ll again provide a set of instructions and then proceed to stage three.
- Urgent risk – When urgent threats strike, we’ll aim to reach our emergency contacts as soon as possible. From there, we can isolate endpoints or run an antivirus scan to diagnose and contain the threat.
For the most urgent threats, we will also generally turn on whatever Heimdal modules we need to quickly eliminate the risk – even those the client isn’t already paying for. At this stage, our priority is to protect your IT assets, whatever it takes.
3. Perform Complex Analysis
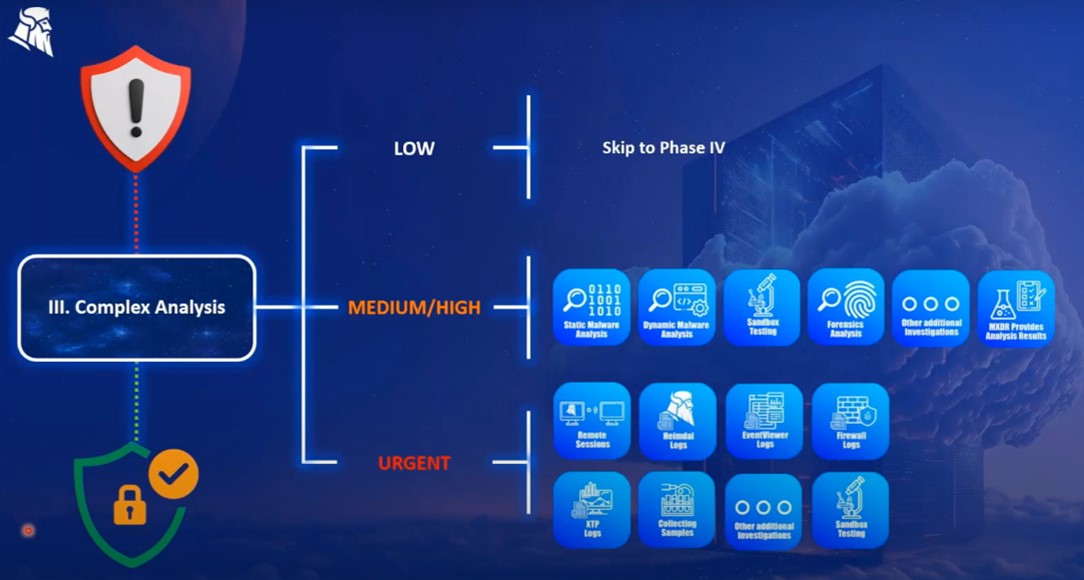
By stage three, the immediate threat has generally been isolated. Our goal here is to understand more about what caused the attack so we can ensure it has been completely eradicated and prevent similar attacks from being successful in future.
- Low risk – Low risk threats generally don’t require complex analysis, so we’ll skip straight to stage four here.
- Medium risk – Here, our options involve either static or dynamic malware analysis, sandbox testing, forensic analysis, and a thorough analysis of Heimdal’s XDR results.
- High risk – To investigate the most urgent threats, we’ll generally run remote sessions, collect samples, complete sandbox testing, and analyze logs from a range of sources, including EventViewer, firewalls, XTP, and Heimdal XDR data.
4. Remediation And Eradication

In this section, we aim to give the client all the information they need to understand what’s happened and avoid it from taking place again in future. There are also several actions we can take to repair and strengthen the IT environment:
- Low risk – For low risk threats, the Heimdal XDR platform will provide analysis results that we’ll then share with the client. This will generally include information like what the threat was, how it happened, how dangerous it was, and how to avoid in future.
- Medium risk – Depending on the threat, there are several actions we could take here, including system patching, exploit removal, and remediating vulnerabilities. We’ll also enhance our monitoring of the IT environment in the immediate aftermath of the attack, to make absolutely sure no residual threat remains. We will then conduct a full post-incident review with the client.
- Urgent risk – Here, the post-attack actions we take are the same as with medium risk threats. Along with the post-incident review, we’ll also organize a call between the client and the security team to discuss the attack and its ramifications in detail.
Through all four stages, our goal remains the same: To do whatever we can to isolate and eliminate the threat. Then, we’ll give you whatever tools we can to repair the damage and reduce the chance of similar threats emerging again in future.
Beat the Market AND the Hackers With Heimdal MXDR
Effective cybersecurity is certainly more difficult today than it was just a few short years ago.
Amidst tightening budgets and rising cybercrime, we’re now faced with an increasingly complex set of tools designed to keep us safe. But complex doesn’t always equal effective.
Instead, MXDR gives you the tools to consolidate your cybersecurity licenses, reduce costs, and improve your overall security posture.
And with a team of dedicated experts, you’ll have everything you need to proactively defend your IT environment and quickly respond to incoming threats.
If you want to find out more about Heimdal’s MXDR service, check out the full page here or get in touch with our sales team to arrange a chat.
Frequently Asked Questions: MXDR
What does MXDR stand for?
Managed extended detection and response (MXDR) is a managed security service operated by many cybersecurity vendors and MSSPs. It includes ongoing analysis, response, remediation, and several other services to help respond to incoming threat signals. These services include a license to the underlying technology used to monitor your IT environment, known as XDR.
What is the difference between XDR and MXDR?
XDR stands for extended detection and response. This is a cybersecurity product that aims to consolidate a range of disparate threat detection tools, including SIEMs, EDRs, DNS security, and more. Managed extended detection and response (MXDR) includes an extra managed service, meaning a team of IT experts also monitors your environment and responds to incoming threats.
What is EDR vs XDR vs MXDR?
Endpoint detection and response (EDR) is a threat detection tool that specifically monitors realtime threats on laptops, smartphones, and other devices. Extended detection and response (XDR) consolidates EDR functionality with a range of other cybersecurity tools to create a more holistic approach to security. MXDR is the term for when security providers offer an additional managed service alongside the XDR license.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











