Contents:
The latest surge of Android apps making their way onto the Google Play app store are posing as harmless file managers, but they actually infect Android users with the SharkBot malware.
The apps do not have a malicious payload during installation to avoid detection by Google Play but instead retrieve it later after the installation. The trojan apps are file managers, so requesting permissions such as loading malware is less suspicious.
Money and Credential Stealing Features of SharkBot
SharkBot employs four main strategies that can help it steal banking-related information on Android:
- Overlay attack: The most effective use for SharkBot is to steal credentials by tricking an unsuspecting user into providing them. The bot is programmed to recognize when a banking app has been launched and automatically hijack it with a false log-in page (a phishing attack).
- Keylogging: The SharkBot botnet can perform a keylogger attack, logging accessibility events (related to text field changes and button clicks) and sending these logs to the command and control server (C2).
- SMS intercept: SharkBot can hide/intercept SMS messages.
- Remote control/ATS: SharkBot hooks into Accessibility Services to capture the full power of an Android device.
How Does SharkBot Infect Android File Manager Apps?
Cleafy Threat Intelligence Team discovered an Android banking malware named “SharkBot” in October 2021.
The Cleafy blog post discusses how SharkBot, a new Android malware, can initiate money transfers via an automated transfer system. This is an advanced technique that researchers don’t usually see in Android malware, so it’s something to keep your eye out for!
Cybersecurity researchers found that they need to turn infected devices into bots to spread this fake Antivirus.
That’s where SharkBot comes in. It abuses the ‘Direct Reply’ feature on Android that automatically sends a reply notification with a message to download the fake Antivirus app.
The malware constantly changes its appearance, popping up on the Play Store in different forms or loaded in trojan apps.
New research by Bitdefender found that while researching Android trojan apps, they discovered a new one disguised as a file manager. They reported the malicious Android app to Google, and it has since been removed from the Google Play Store.
Although hundreds of people may have downloaded these apps in the past, there is a possibility that some still have them installed on their phones or are suffering from undiscovered malware infections.
The first malicious app was ‘X-File Manager’ by Victor Soft Ice LLC. It was downloaded 10,000 times via Google Play before it was removed to prevent future damage.
Furthermore, SharkBot will only activate on Great British and Italian SIM cards, which means it’s a targeted campaign.
As Bitdefender points out, the list of possible mobile bank apps targeted by malware could change anytime. This is because the threat actors can remotely update it whenever they want.
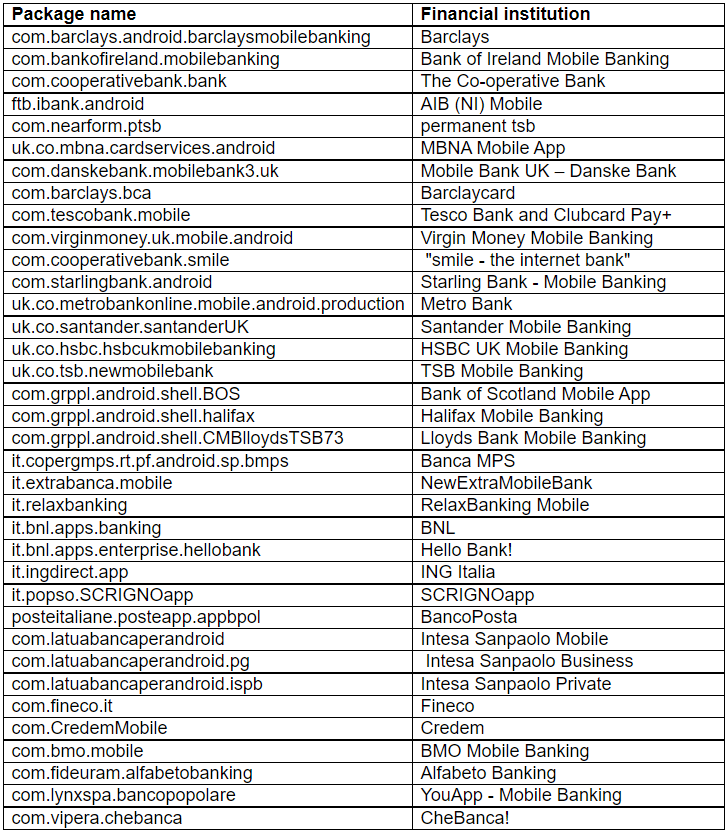
Bitdefender’s telemetry data reveals that the narrow targeting of the campaign has been seen mainly in the United Kingdom, followed by Italy, Iran, and Germany.
The malicious app asks permission to access your phone’s external storage, install new packages, read and write your account details, delete containers, and wipe traces.
However, these permissions may seem ordinary and expected within the context of file management applications, so users are unlikely to treat the request with any concern.
SharkBot aspires to be a fake program update. The user is prompted for approval before installing the X-File Manager.
The most common way the banking trojan is installed is through an app called FileVoyager by Julia Soft Io LLC. This app was downloaded 5,000 times via Google Play.
FileVoyager shares the same operational pattern as X-File Manager. The software focuses on financial institutions in Italy and the UK to give users a wide-ranging experience.
Bitdefender spotted another app called “LiteCleaner M”, which was downloaded 1,000 times before being removed from the Google Play Store.
Currently, this app is only available through third-party app stores like APKSOS. However, the same store hosts a SharkBot loader named Phone AID, Cleaner, and Booster 2.6.
What Can You Do To Keep Safe?
Threat actors are becoming increasingly common to infiltrate significant app stores, like the Google Play Store, and distribute their malicious software. To avoid these types of threats, it’s always recommended to only download apps from verified publishers and report any shady behavior to the app store.
If you use any Android apps, you should delete these immediately and change the passwords for any online bank accounts you use.
One of the best defenses against these malware-laced apps is to keep the Play Protect service turned on, which scans and removes malicious apps.
In addition, an Android mobile security antivirus option would help to detect malicious traffic and apps before they are reported to Google Play.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








