Contents:
Flaws found in the Galaxy App Store gave attackers the ability to install apps without the user’s knowledge and send them to malicious sites.
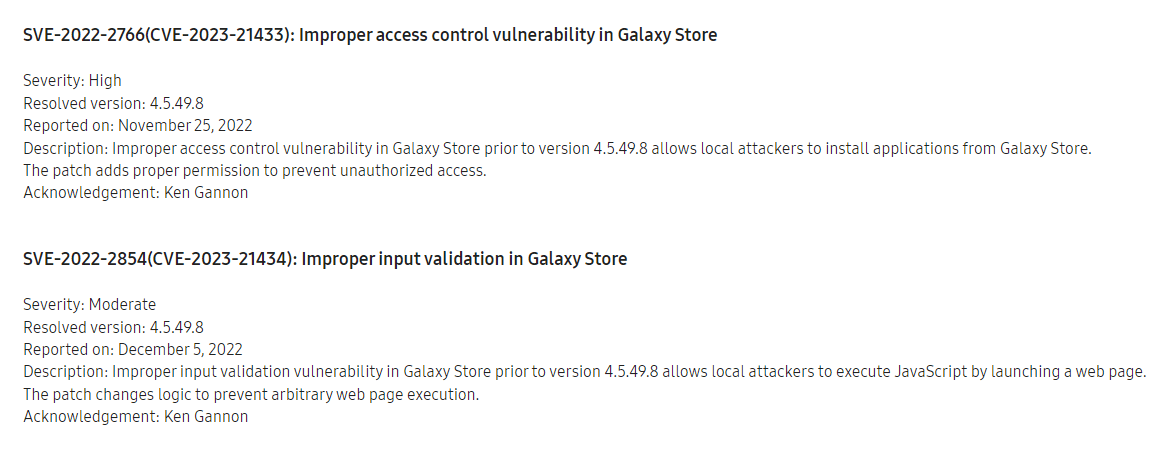
Samsung was notified regarding flaws CVE-2023-21433 and CVE-2023-21434, in November and December 2022. After flagging the first bug as high and the second one as moderate risk, the company announced fixing both, on January 1st, this year. A new version of the Galaxy App Store (4.5.49.8) was also released and users of Android 12 and before are urged to update to it, in order to protect themselves from the two CVEs.
Technical Details on Samsung’s Galaxy Store App Vulnerabilities
- CVE-2023-21433
The security issue made it possible for rogue Android software that is already present on the Samsung device to install any app from the Galaxy Store. It was defined as an improper access control problem that only had an impact on devices that used Android 12 and before. The vulnerability did not affect devices using Android 13.
If threat actors succeed in uploading malicious apps on Galaxy Store, the user could easily fall victim to data breach and privacy loss.
- CVE-2023-21434
By exploiting this vulnerability, an improper input validation, threat actors can run JavaScript on the target device by accessing a web page.
In this instance, researchers discovered that a webview in the Galaxy App Store included a filter that restricted the URLs it could explore. Because that filter was misconfigured, it allowed the webview to navigate to sites controlled by threat actors.
Cyber researchers stated that:
Either tapping a malicious hyperlink in Google Chrome or a pre-installed rogue application on a Samsung device can bypass Samsung’s URL filter and launch a webview to an attacker-controlled domain,
This kind of attack can offer access to private data, crash apps, and facilitate app UI interaction.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







