Contents:
Heimdal™ Security’s SOC department together with other cybersecurity institutions have released an all-out advisory to its customer base, clients, users, and partners in regards to the activity of an emergent botnet that has infected thousands of websites. The botnet StealthWorker (GoBrut) has achieved an impressive number of hits in a brief span of time, by brute-forcing the victim’s Internet-facing NAS devices and web servers. As for the ‘zombified’ devices, Heimdal™ believes that they will be used in future botnet campaigns for the purpose of compromising even more hosts.
Botnet StealthWorker – M.O, Infectious Mechanism(s), and Distribution
GoBrut aka StealthWorker is not exactly a botnet novelty. In fact, the same botnet has been involved in the August 2021 attack against Synology’s NAS devices but, interestingly enough, it goes all the way back to February 2019 when the same malware was found to be behind several brute-force attacks launched against improperly secured CMSs, Magento being among them. It appears that its MO’s been consistent over time – using distributed brute-force attacks in order to infiltrate, infect, corrupt, and ‘zombify’ the target device.
Design-wise, Gobrut has been written in Golang, a programming language very popular among hackers and pen-testers for its flexibility, reasonable learning curve, and coding efficiency, and employs two IP addresses – one for payload delivery and one to perform various C2 functions. As in the case of Synology, the payload’s delivered via JS injection or similar. Once the delivery was marked as successful, the malware will begin to enumerate resources, identifying those that are vulnerable to brute force.
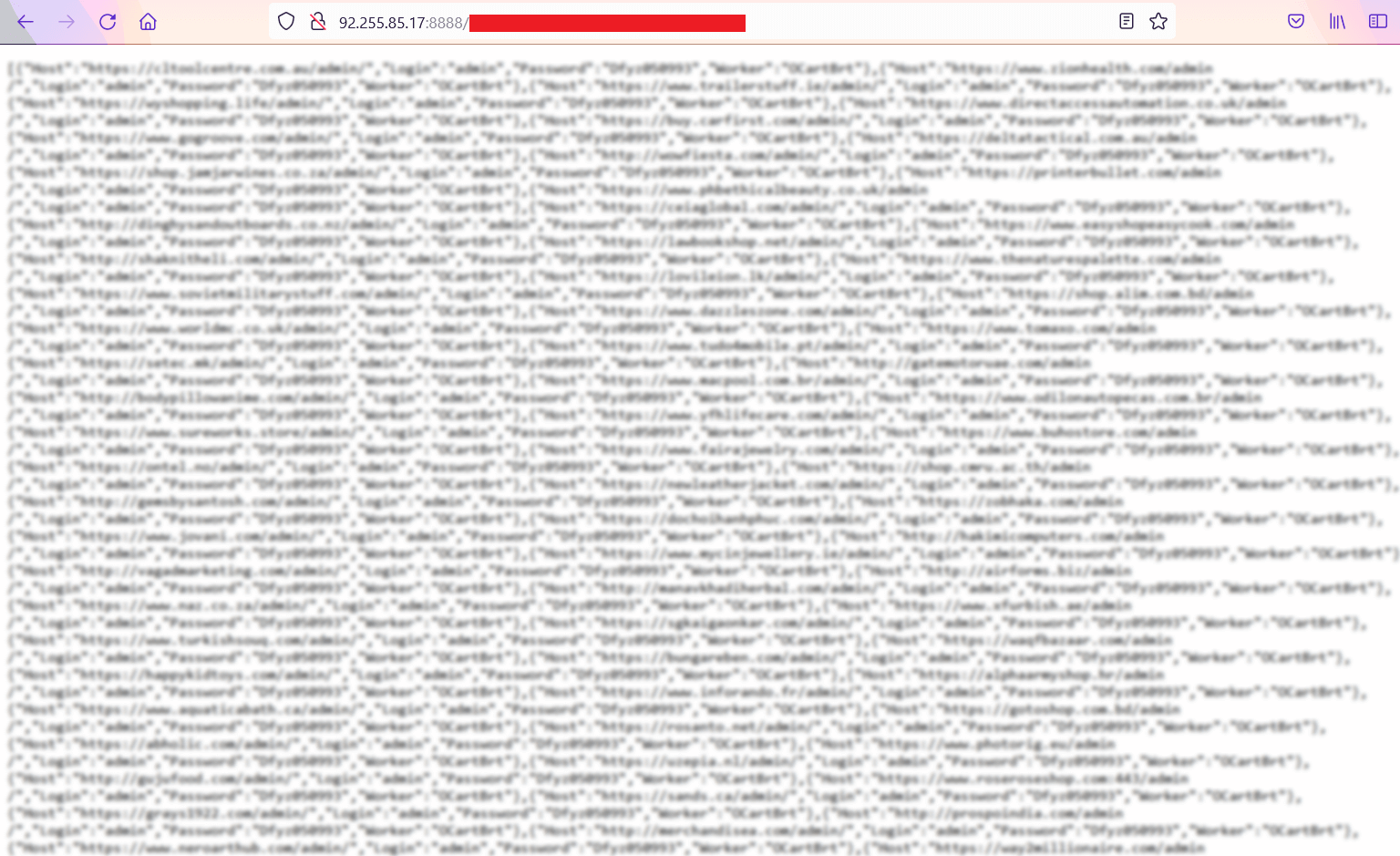
One of the reasons why botnet StealthWorker has had a stellar success resides in how certain CMSs handle password hygiene. In several cases, the credentials that got leaked were default user-password pairs, meaning that no steps have been taken to strengthen those credentials (e.g., password evaluators, salting, etc.). Concerning infiltration, the credentials obtained via distributed dictionary-based brute-forcing were fed to a c2 panel hosted on the second ‘attack’ address (i.e., the one used to perform C2 functions). What’s even more daunting is the fact that Gobrut also has the capability of backtracking user admin login paths and scouring backup file locations.
Photo courtesy of SecurityPix
Crude as far malware goes, although botnet StealthWorker relies heavily on distributed brute-forcing, it has managed to expose thousands of web servers running various types of CMSs (e.g., OpenCart, MySQL, SSH, FPT, Drupal, Joomla, and WordPress).
Additional Cybersecurity Advice
Since the botnet SteathWorker is currently active, Heimdal™ Security recommends the following:
- Evaluating and changing your password-related policies. Focus on NAT devices and your CMSs. Change your default passwords immediately and, if applicable, enforce Multi-Factor Authentication (MFA).
- Blacklisting the attack and C2 IPs. If your company employs a WAF, please blacklist the following addresses: http://82.165.106.79/ (payload IP) and http://92.255.85.17:8888/ (C2 IP).
- Deploy security updates (if available). Please check with your CMS vendor for the latest security updates. If there are unapplied updates and/or patches, deploy them as soon as possible.
- Brute-force protection. Two-progged attacks can only be stopped by using brute-force protection (detect brute-force attempts and blacklist IPs). Heimdal™ Security’s Next-Gen Antivirus & MDM is a product designed to prevent, address, and mitigate the after-effects of a botnet-spun brute-force attempt.
Conclusion
The botnet StealthWorker is the very embodiment of the saying: “simpler is better”. Although heavily reliant on volumetric attacks, this malware has managed to rake up numerous hits by leveraging sub-par authentication mechanisms.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security