Contents:
Update 23rd April 2019: Further research revealed that the ShadowHammer malware has targeted and successfully attacked multiple companies, not just ASUS. In these other attacks, similar algorithms were used and just like in the ASUS case, legitimately signed certificates were used. Among the other targets were Electronics Extreme (authors of the ‘Infestation: Survivor Stories’ zombie survival game), Innovative Extremist, another IT and game development company, and Zepetto (the South Korean authors of the ‘Point Blank’ video game). There were also several retailers and pharmaceutical companies located in Asia targeted by the ShadowHammer attack. Latest security updates unveiled an advanced persistent threat (APT) attack that affected over a million ASUS users worldwide. This type of attack is unprecedented in its seriousness because it managed to perfectly imitate the signature of the original ASUS auto-update software, passing by undetected by conventional anti-virus solutions. This huge supply chain attack fooled computers into thinking they were receiving updates from ASUS, all the while installing a backdoor into those computers. This unusually dangerous attack has been dubbed Operation #ShadowHammer and ran from June 2018 to November 2018 undetected until now. We want to make you aware of this vulnerability, and urge you to take a few basic steps to secure your system, in case you own any ASUS computers.
How the Advanced Persistent Threat (APT) infection worked
The ASUS Live Update is a software patching utility which comes preinstalled on most ASUS computers. It’s used to perform automatic updated on important computer software components, such as BIOS, UEFI, software drivers, and some other major applications. The hackers managed to replace the authentic ASUS Live Update software with several corrupted versions of their own, which imitated the digital signature of ASUS and fooled computers into downloading and installing them. The researchers who raised the alarm estimate that over a million computers were affected. Each of these corrupted auto-update software versions was targeting a specific and unknown pool of users, which were identified by their network adapters’ MAC addresses. Cybersecurity experts say that this type of MO points to a surgical espionage malware, which means it was specifically designed to spy on specific users.
Asus Live Updater was used in a big supply chain attack we dubbed Operation #ShadowHammer. We estimate this may have affected over 1 million computer users between June and Nov 2018. https://t.co/jTij3NwpSs
— Costin Raiu (@craiu) March 25, 2019
After a corrupted version of the ASUS auto-update software was installed, the hackers used the hardcoded list of MAC addresses in order to identify those computers where their backdoor had been installed. Once those computers were detected, the hackers then deployed stage 2 of their supply chain attack. The second part of malicious code was downloaded from the command-and-control server located at asushotfix[.]com. This server was taken down some time in November 2018, way before the cybersecurity researchers first detected this vulnerability in the ASUS auto-update software.
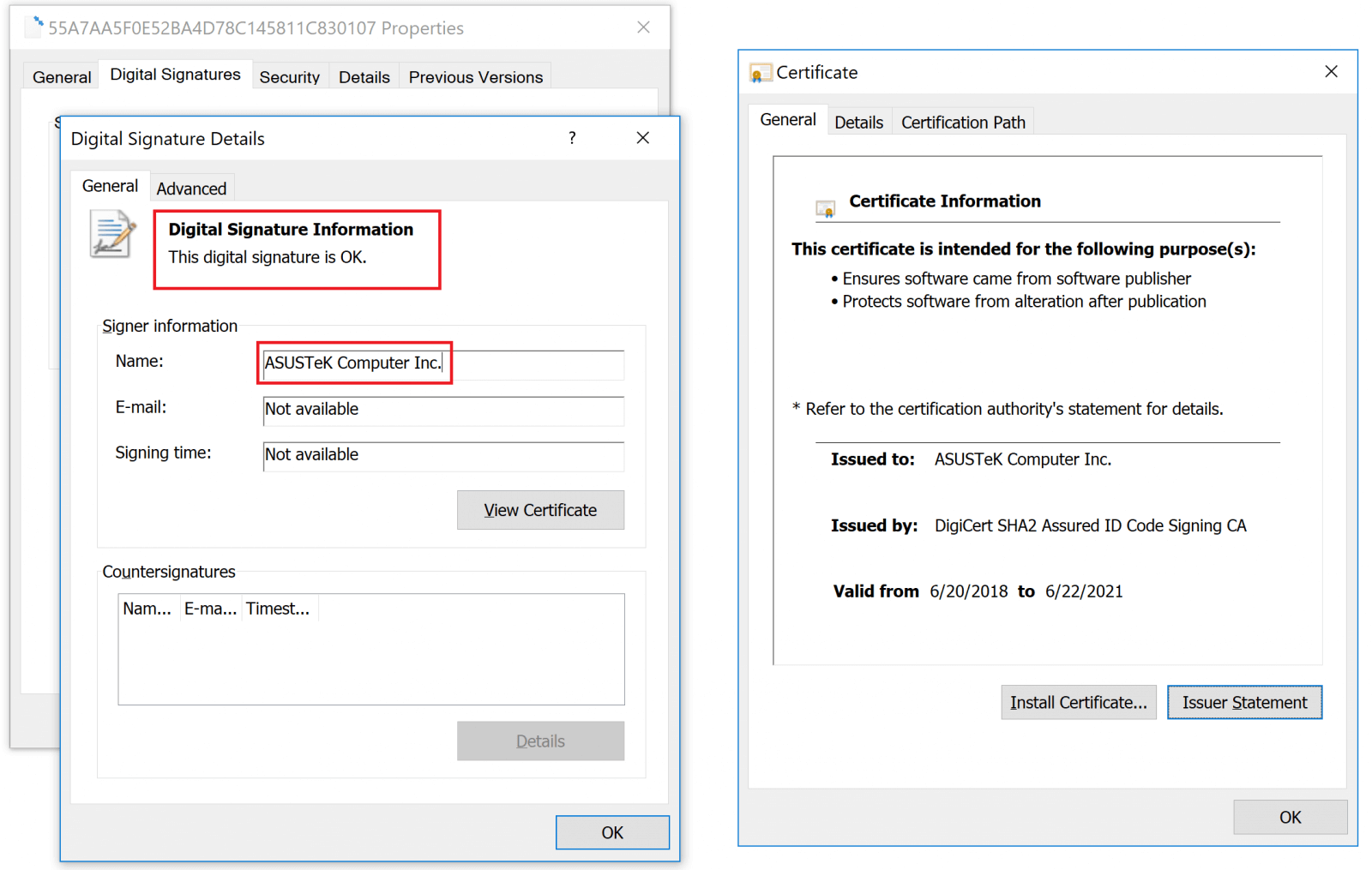
Signed ASUS Live Updater Installer Certificates.
According to them, the setup installers were perfectly imitating digital signatures with legitimate “ASUSTeK Computer Inc.” certificates that were “hosted on the official liveupdate01s.asus[.]com and liveupdate01.asus[.]com ASUS update servers.” It’s not the first time that hackers use a legitimate program in order to install backdoors through it. A similar supply chain attack was carried out through CCleaner in 2017. Still, this is the first attack which manages to imitate digital signatures perfectly and infect computers on such a large scale. Since ASUS is the 5th largest PC vendor in the world (according to a 2017 Gartner count by unit sales), this so-called #ShadowHammer malware is a remarkably dangerous one. As for who could be behind this attack, the researchers who discovered the issue don’t have a definitive answer, but a strong hunch. The breach bore many similarities to previous supply chain attacks targeting CCleaner (the incident linked above) and the ShadowPad attack from 2017 which impacted NetSarang. The threat actor associated with those attacks was BARIUM, an entity which researchers suspect is backed by the Chinese government. Most users affected were located in Russia, Germany, and France. The chart below sheds more light onto the main user pools impacted by this ASUS Live Update backdoor.
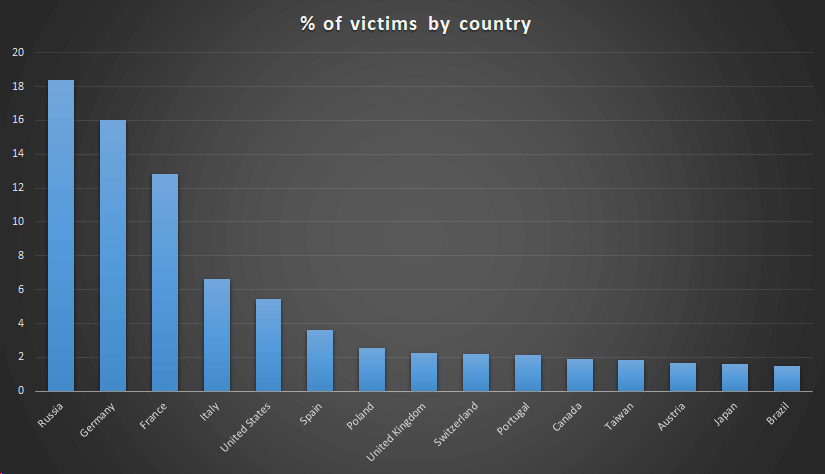
#ShadowHammer Victim Distribution by Country. Image source: BleepingComputer.
Our own numbers show that less than 5% of all Heimdal Security active users own ASUS computers. Still, we urge everyone to be vigilant and make sure they are getting the best protection possible. A concerted attack such as this APT cannot be detected by conventional antivirus solutions since it imitates the digital signatures of the original software. The only chance of preventing this kind of infection is to have the complete protection offered byHeimdal™ Threat Prevention (prevention shield) with Thor Vigilance (the anti-virus itself). We offer this powerful combo in our Heimdal™ Premium Security Home and Endpoint Security Suite use.
Apply these basic security measures to protect yourself:
Here’s what you can do right now to make sure you’re safe if you’re an ASUS computer user.
#1. Check if your computer has the ASUS Live Update facility.
You can find the updater usually in the icon bar, bottom right corner of your screen, like in the screenshot below. ![]()
#2. Uninstall it from the Control Panel
If you have the ASUS Live Update facility installed, go to the Control Panel / Programs / Programs and Features. Find the ASUS Live Update there in the alphabetically ordered list and click uninstall. You can always reinstall this software later if you really want to after the crisis is contained by ASUS and we can be sure the danger has passed.
#3. Run a scan of your entire computer ASAP
Run a complete scan of your computer to see if the ASUS installer created any trouble or deployed other Trojans throughout your system. You can use our EDR Solution free trial; you have 30 days of free use so there’s plenty of time to secure your system before the trial expires.
#4. Use a trusted Software Patching Manager
Instead of the ASUS Live Update facility which you just uninstalled, use a trusted software patching manager to keep everything inside your computer up to date. Lagging behind on updates for your apps and software is a major security liability since that’s the entry ticket for most malicious actors. Our Thor Free product can help you manage your software updates from one single dashboard. It runs silently and automatically in the background, and it’s free forever.



 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










