Contents:
Summary: we discovered a Digi phishing campaign targeted at Romanian internet users. However, the campaign is displaying tailored content for each country, so its actual target pool is much larger. The malicious domains could be accessed from organic Google search results and led the user to a page with Digi branding elements. Once there, the users were invited to go through some steps, ‘win’ a prize consisting of a new smartphone and then claim the ‘prize’ by submitting their personal details, including credit card information.
How Does the Digi Phishing Campaign Work?
Incidentally, we found these malicious websites while looking for Antivirus-related search words on Google. It’s pretty ironic if I think about it since people who are looking for cybersecurity software could be well enough prepared to recognize a phishing campaign. Of course, I suspect that this is not the only search that could lead to these malicious but organic results to be displayed. 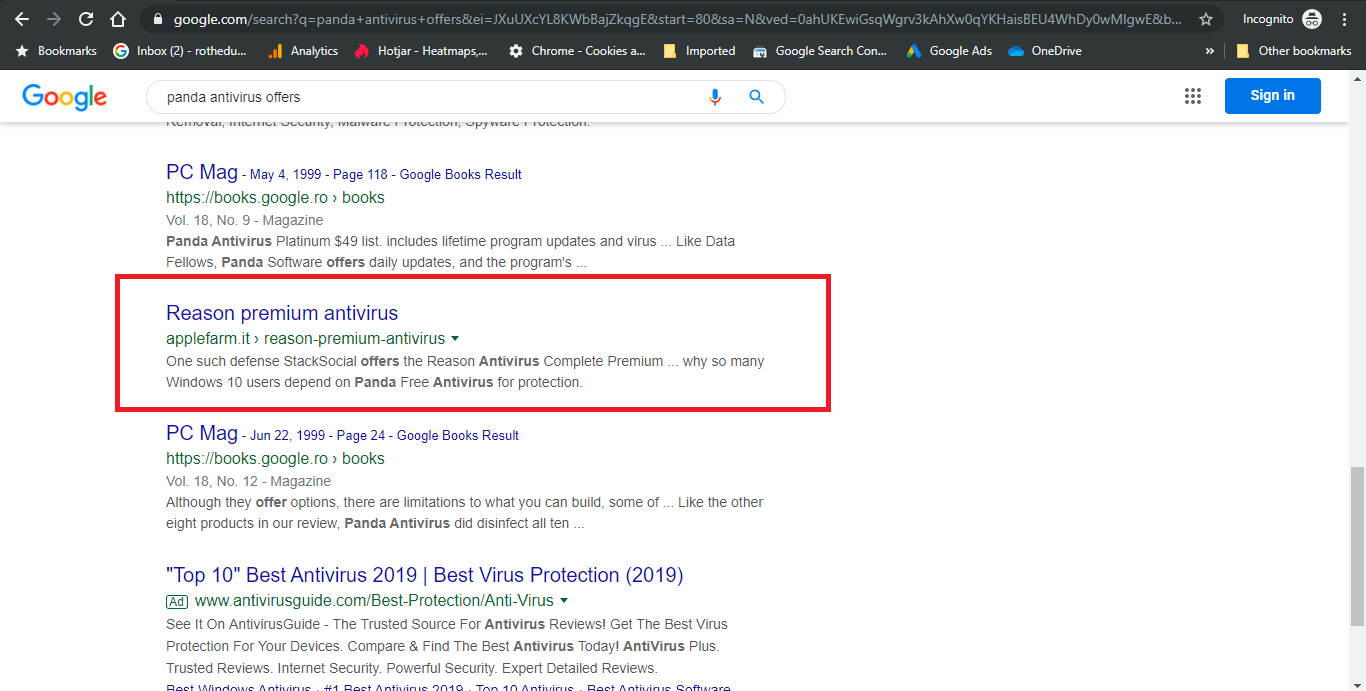 The malicious link for the Digi phishing campaign only worked if accessed from Google. If we attempted to access them directly, the browser just entered a redirect loop and nothing was loaded. Once we accessed the website, the page first asked for verification of humanity (the standard ‘Confirm you are not a robot’ checkbox). Oddly, this first screen was displayed in Spanish, although the next ones are in Romanian, based on the correct identification of our location.
The malicious link for the Digi phishing campaign only worked if accessed from Google. If we attempted to access them directly, the browser just entered a redirect loop and nothing was loaded. Once we accessed the website, the page first asked for verification of humanity (the standard ‘Confirm you are not a robot’ checkbox). Oddly, this first screen was displayed in Spanish, although the next ones are in Romanian, based on the correct identification of our location. 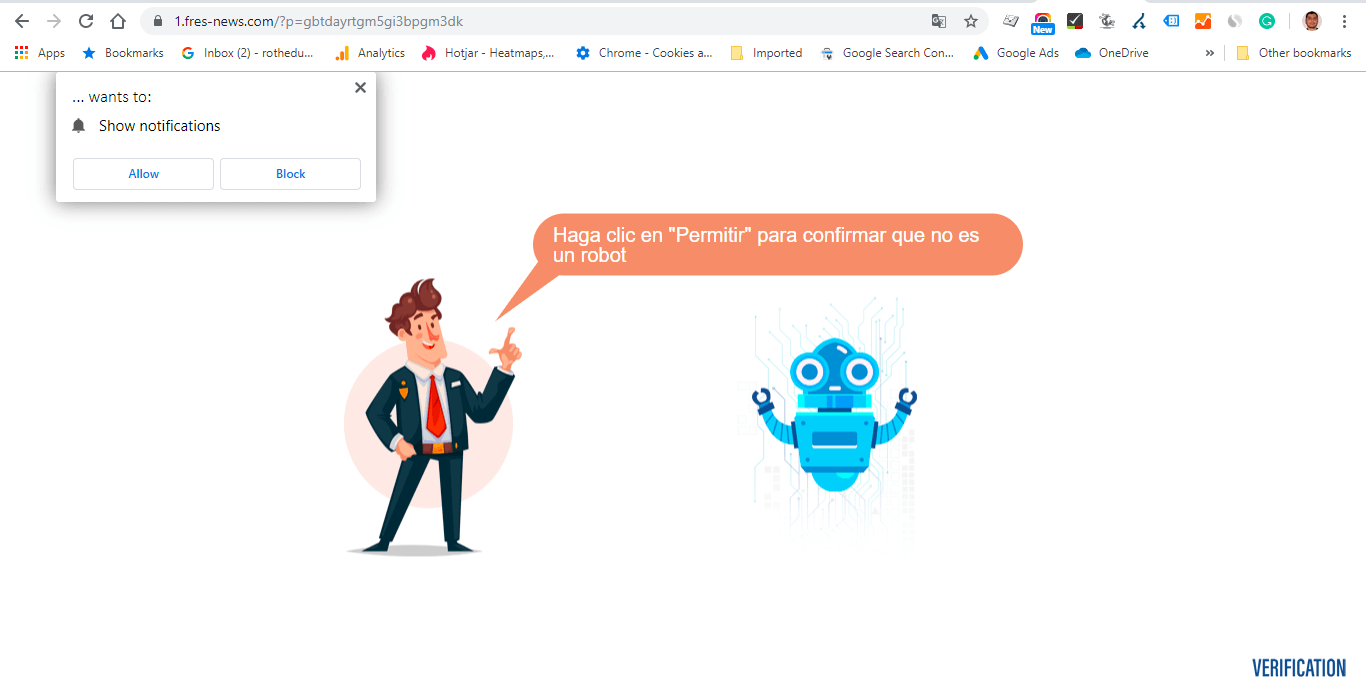 After moving past the human confirmation screen, a page imitating the Digi brand is displayed. The page offers congratulations for being ‘one of the selected 100 users’ eligible to receive a smartphone gift. But before you can receive your gift, you need to answer 9 questions.
After moving past the human confirmation screen, a page imitating the Digi brand is displayed. The page offers congratulations for being ‘one of the selected 100 users’ eligible to receive a smartphone gift. But before you can receive your gift, you need to answer 9 questions. 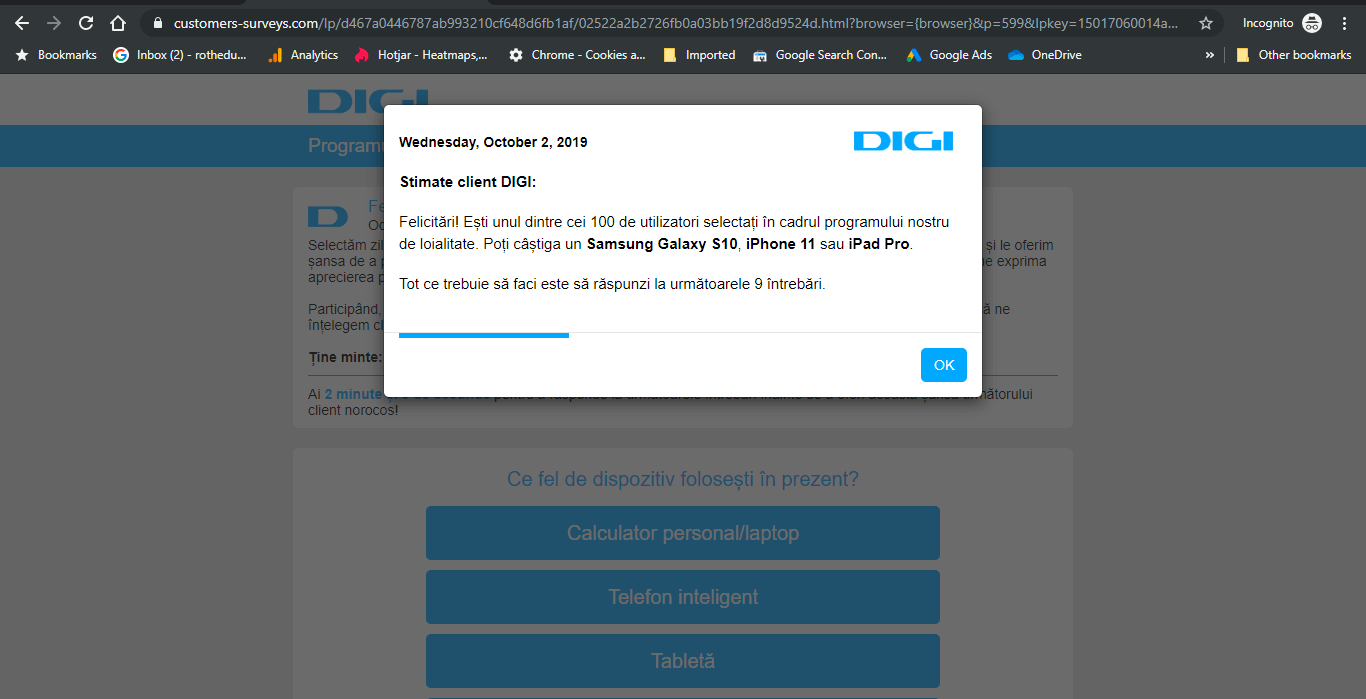 The questions are well crafted as to not arouse suspicion. All of them were about the devices you use, what other internet and cable providers have you had, that kind of stuff – it can seem like legitimate competitor research questions a brand can ask its users. After moving through the questions, you get another confirmation that you answered all of them, that no duplicate IP entries were found and that you are indeed about to get the smartphone reward.
The questions are well crafted as to not arouse suspicion. All of them were about the devices you use, what other internet and cable providers have you had, that kind of stuff – it can seem like legitimate competitor research questions a brand can ask its users. After moving through the questions, you get another confirmation that you answered all of them, that no duplicate IP entries were found and that you are indeed about to get the smartphone reward. 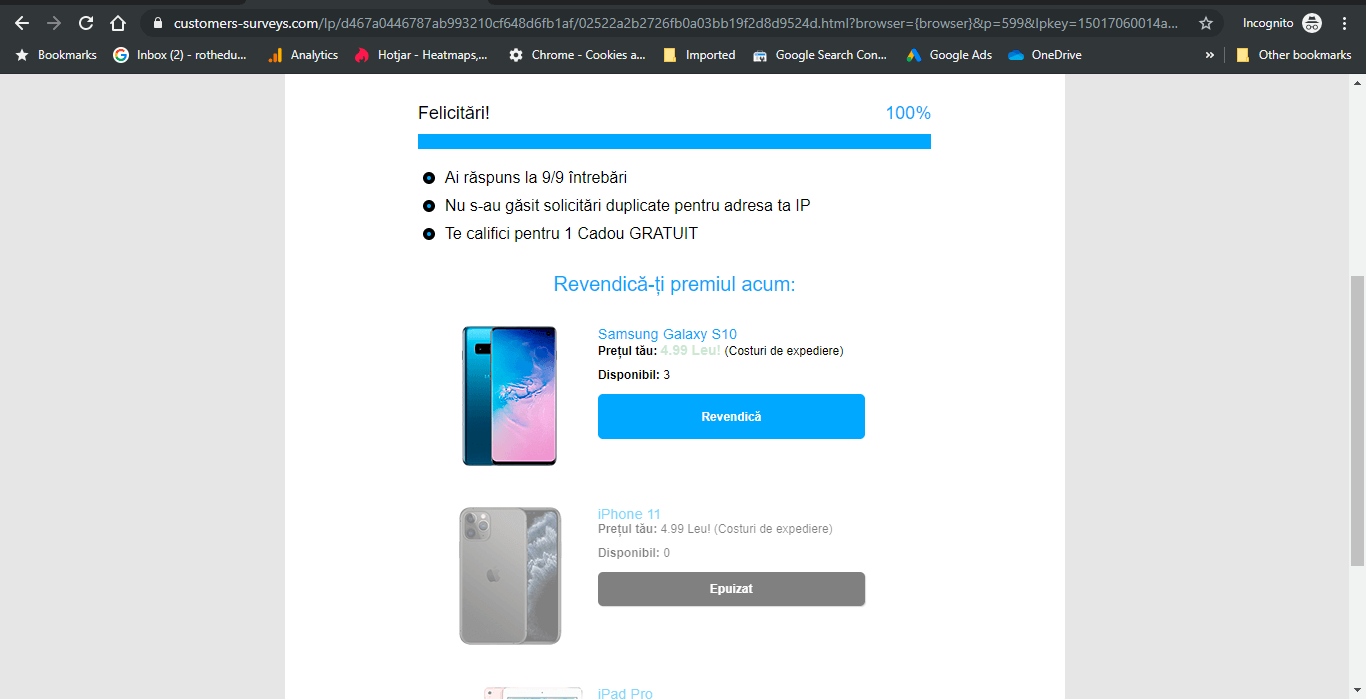 Clicking ‘Next’ will take you to a page displaying the smartphone prize and asking for your email, as well as a confirmation you are over 18.
Clicking ‘Next’ will take you to a page displaying the smartphone prize and asking for your email, as well as a confirmation you are over 18.  After entering your email, you are asked for your credit card details, allowing you to ‘buy’ the smartphone for 4.99 RON, the approximate equivalent of 1 EURO. There’s also a countdown timer on the offer to make you feel the FOMO. Judging by the bad grammar and spelling on this page, I have a strong hunch that this Digi phishing campaign displays in other languages as well, probably across Europe.
After entering your email, you are asked for your credit card details, allowing you to ‘buy’ the smartphone for 4.99 RON, the approximate equivalent of 1 EURO. There’s also a countdown timer on the offer to make you feel the FOMO. Judging by the bad grammar and spelling on this page, I have a strong hunch that this Digi phishing campaign displays in other languages as well, probably across Europe. 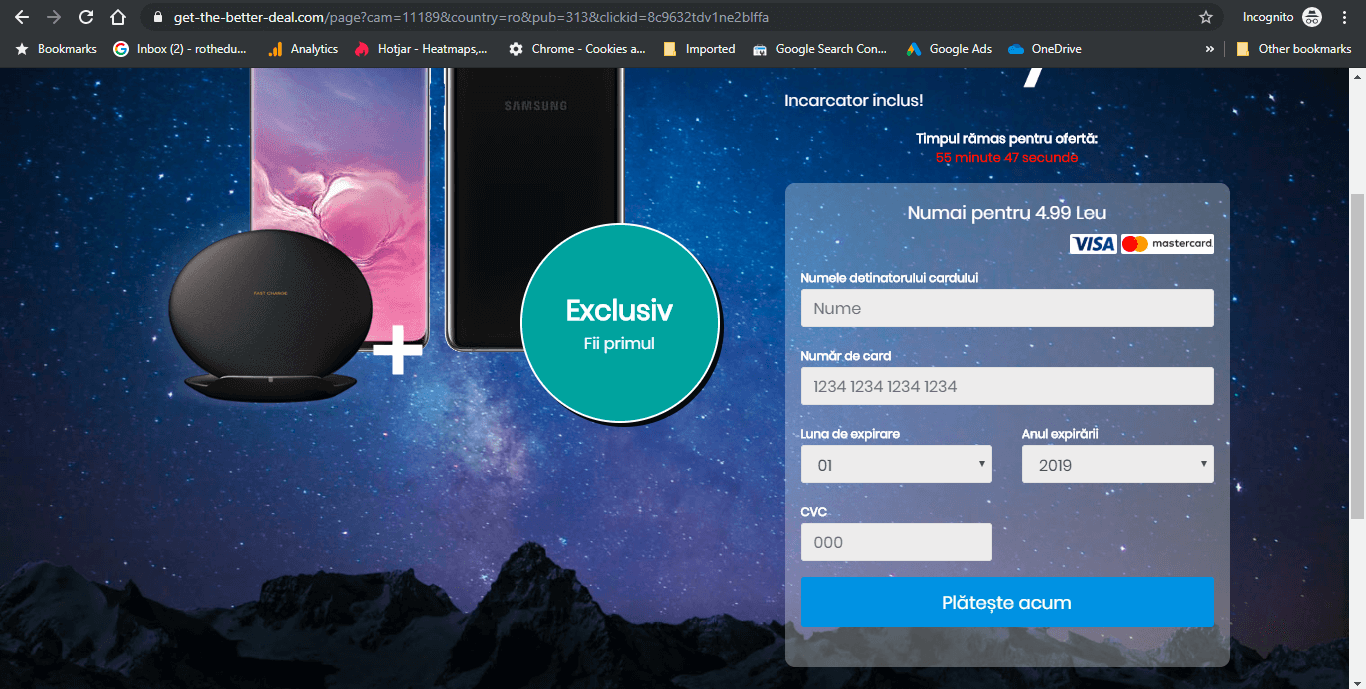 These are the malicious URLs we identified as part of this Digi phishing campaign (but they do not work if accessed directly, only if accessed through search results): http://applefarm.it/wx0/reason-premium-antivirus.html https://fres-news.com/?p=gbtdayrtgm5gi3bpgm3dk https://1.fres-news.com/?p=gbtdayrtgm5gi3bpgm3dk https://2.fres-news.com/?p=gbtdayrtgm5gi3bpgm3dk https://customers-surveys.com/lp/d467a0446787ab993210cf648d6fb1af/02522a2b2726fb0a03bb19f2d8d9524d.html?browser={browser}&p=599&lpkey=15017060014a220f78&source=AdCash&campaign=173949420&zone=2048991-600419873-0&subzone=Adsterra&uclick=2tdv1ne2bl# https://supertrackingz.com/click.php?lp=1 https://get-the-better-deal.com/page?cam=11189&country=ro&pub=313&clickid=8c9632tdv1ne2blffa Meanwhile, our own cybersecurity software (the DNS traffic filtering engine in Heimdal™ Threat Prevention) blocks all of the above.
These are the malicious URLs we identified as part of this Digi phishing campaign (but they do not work if accessed directly, only if accessed through search results): http://applefarm.it/wx0/reason-premium-antivirus.html https://fres-news.com/?p=gbtdayrtgm5gi3bpgm3dk https://1.fres-news.com/?p=gbtdayrtgm5gi3bpgm3dk https://2.fres-news.com/?p=gbtdayrtgm5gi3bpgm3dk https://customers-surveys.com/lp/d467a0446787ab993210cf648d6fb1af/02522a2b2726fb0a03bb19f2d8d9524d.html?browser={browser}&p=599&lpkey=15017060014a220f78&source=AdCash&campaign=173949420&zone=2048991-600419873-0&subzone=Adsterra&uclick=2tdv1ne2bl# https://supertrackingz.com/click.php?lp=1 https://get-the-better-deal.com/page?cam=11189&country=ro&pub=313&clickid=8c9632tdv1ne2blffa Meanwhile, our own cybersecurity software (the DNS traffic filtering engine in Heimdal™ Threat Prevention) blocks all of the above.
Context: Another Campaign Which Fakes Digi Branding, but on Social Media
As it happens, another fraudulent campaign using the Digi branding has been identified in the past few days, on social media. There were 5 fake Facebook Digi accounts posing as the official page, even if they were clearly recently created and had very few likes. Link to full story HERE (the text is written in Romanian). Even more weirdly, one of the pages also ran a sponsored campaign on Facebook, attempting to grow its user pool. The incident is unanimously believed to be a part of a potential electoral fraud campaign, preparing to flood people with fake news in order to influence their votes. This Digi fake accounts campaign is not so different from the Cambridge Analytica scandal and also with some Russian involvement. Some of the ‘o’ characters in these fake Digi pages were not quite right, and a closer look revealed that the input method had been a Russian keyboard, using the Cyrillic equivalent of ‘o’.
Potential of Electoral Fraud?
Such campaigns have a huge potential for electoral fraud and other types of social engineering. While the two types of campaigns discovered could be unconnected, I’m not yet sure it’s all a coincidence. It’s clear that the objective of the first campaign was to collect credit card details for some type of actual financial theft. It’s also true that Digi is a very well-known brand, so it makes sense for any hacking group to use its image for a campaign. But at the same time, I am also concerned that the two Digi phishing campaigns are not unrelated and hacking into people’s wallets is just another offshoot of malicious intent. Especially since elections are upcoming and social engineering has already proved its potential for evil, I suspect we will see more in the following months.
How to Stay Safe from Phishing and Social Engineering in General:
We’ve written dedicated guides on how to stay safe from phishing and how to recognize social engineering. Please feel free to browse them and take some precautions from there. In a nutshell, the most important take-away from the Digi phishing campaign is this: never fail to verify whether a domain you are accessing is the real deal. You can do this by checking its name in the address bar, by closing the tab and going to the official website, or even by contacting customer service to be found on the official page. If an offer sounds too good to be true, it probably is. As for social engineering and the potential of election fraud, things can be more complicated. There was a huge backlash in both ways after the Cambridge Analytica scandal came to life. People are not comfortable accepting that they can be manipulated easily and that perhaps their ideas are not exactly their own. The only advice for this, beyond checking whether the pages posting stuff on social media are the official ones, is to strengthen your critical thinking as much as possible. Note: I would like to thank my colleague Eduard Roth who initially drew my attention to this Digi phishing scam.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security