Contents:
Heimdal® has recently launched an ample investigation into the Russia-linked cybercrime wave. Based on the data gathered from internal and external sources, Heimdal® has discovered that the phenomenon is expanding, both in magnitude and frequency. This article will showcase our SOC team’s discoveries, delineate methodology, and propose actionable strategies that will aid organizations to counter this rising trend.
Background and investigative methodology
To further substantiate the claims set forth by this article, we have deemed it necessary to provide some background. Below you will find a list of publications that have covered the topic.
- A 2021 article by The Guardian labeled this trend as a “rising global threat”, calling out all Russian-speaking black-hat groups that have attacked numerous targets from USA, UK, and Australia. The same article cites GCHQ stating that the number of ransomware attacks would double by the end of 2021.
- A 2022 Barron’s article mentions a link between cyber criminals and Russian intelligence, while also claiming that, given the political climate, Russia may be more inclined to turn a blind eye to their activities, oftentimes leveraging these ill-gotten resources for various cyberespionage-related purposes.
- In February 2022, BBC News posted an article about the paper trail left behind by ransomware attacks. The research reveals that a staggering 74% of all ransomware profits go to Russian-speaking hackers. Furthermore, the same publication hints at the same link between black-hat hackers and the Russian government.
- CISA’s AA22-110A alert mentions an increase in Russian-speaking (and allegedly funded) threat groups, conducting various types of operations against Ukrainian targets. Among the most prolific is BERSERK BEAR, a threat group that earned its notoriety after attacking HVTs from Northern America and Eastern Europe.
- A DW article voices concern that the Ukrainian – Russian conflict may become the hotbed of cybercrime, with many threat groups siding with either Ukraine or Russia. Furthermore, according to BKA (German Federal Police Office), earlier this year, an unknown group of Russian hackers attempted to disable multiple servers belonging to German authorities and ministries.
The Outcome of the Investigation
The methodology used to make our assessment is as follows. Prompted by the gathered intel, we have amassed a list of malicious domain detections going back to early 2021. Event log triage allowed us to conclude that between March 2021 and October 2022, over 600,000 Russian TLDs were created. There’s no evidence to suggest that all detected TLDs were or are used for malicious purposes. Given the high volume, we hypothesize that the non-malicious domains may simply be used as a backup in case of detection. Another working theory is that these ‘inactive’ TLDs could become the foundation of a botnet.
For the purpose of this article, we have eliminated all inactive domains from statistical churning, and, going forward, we will focus solely on the domains with positive hits (i.e., overt intention). Further data investigation revealed that only 1283 of the detected Russian TLDs were associated with malicious activity (i.e., 0.18% prevalence rate when sequencing active vs. inactive domains). Between January 2021 and late October 2022, over 8,000 cyberattacks have been carried out from the domains, at an average of circa 6.35 attacks per day. IP-based domain tracking returned no results as the threat actor has gone to great lengths to minimize the online footprint.
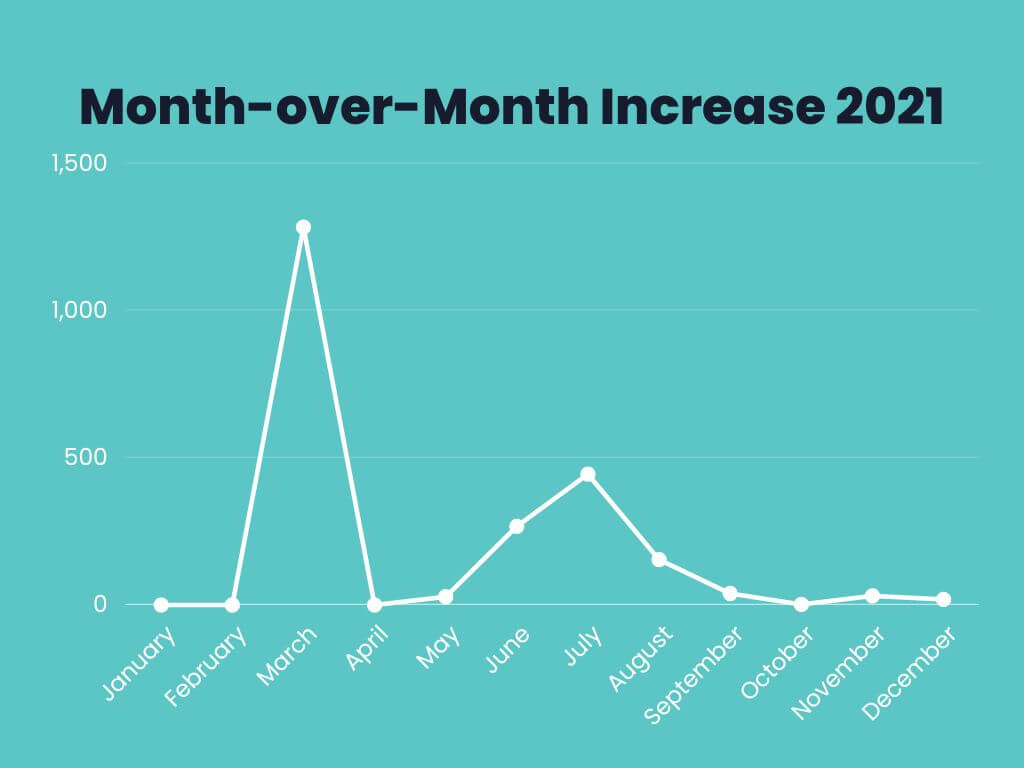
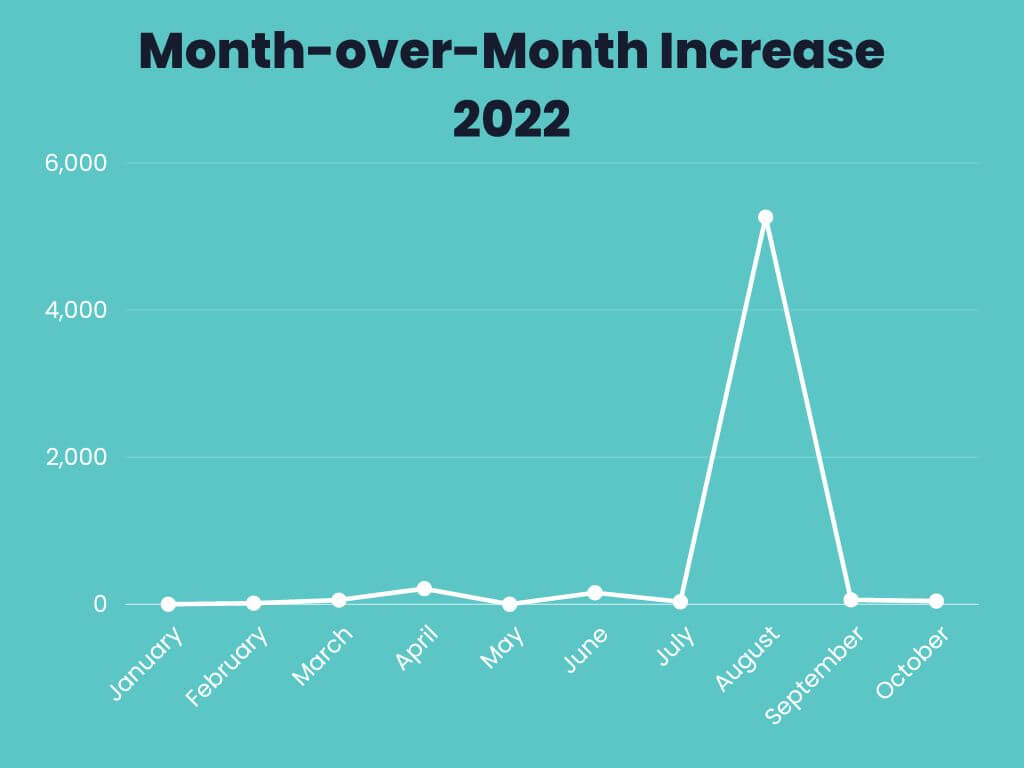
Upon reviewing the final numbers and factoring in variables such as temporal spread, intent, and the number of times a specific domain was used to stage an attack, we can only conclude that Russian-based attack domains are increasing exponentially. Our computations show a 167% year-over-year increase in .ru TLDs, a statement corroborated by the data obtained from clear web sources (i.e. see above section). The investigation is ongoing and we will provide you with updates as soon as they become available. In addition to the data discussed throughout this article, we’ve also annexed the associated graphs (see below).
MoM Increase for 2021
MoM Increase for 2022
Cybersecurity Advice and Conclusions
As the conflict between Russia and Ukraine trudges on, we can expect more threat groups to show up and leave their mark on the cyber world. The numbers provided by Heimdal®’s SOC team prove that the threat is real, with no indications of cessation or slowing down. As mentioned in the section about background and methodology, only a small fraction of the detected domains were used to stage cyberattacks against undisclosed targets. Concerning the bulk, we can assume that they are either backup domains, that can be used in case the primary one is compromised or that the threat actors may be spawning them in order to create a botnet.
To conclude this article, we have enclosed several pieces of cybersecurity advice which you can use in order to increase the efficiency of your defense strategy.
- IP/Domain blacklisting. Creating a custom ruleset for Russian-based IPs and/or domains can significantly reduce the risk of a breach. However, do practice caution on this one because not all Russian TLDs are malicious. Review each instance if necessary to determine the correct course of action.
- Vulnerability management. Bear in mind that no matter the intent, political affiliation, or modus operandi, black-hat hackers will always be gunning for any system, hardware, or software vulnerabilities. To ensure that all the attack gaps are covered, use an automatic patch management solution. Heimdal®’s Patch & Asset Management can aid you in discovering and resolving any type of vulnerability, whether it’s related to OS, third-party or proprietary software.
- Identity management. Ensure that you have up-to-date identity management rules. For sensitive information, enforce the Principle of Least Privilege.
- Endpoint-based defenses. Do not forget about your last line of defense – the antivirus. Please ensure that your antivirus database is up-to-par and, if possible, enhances the functionality of your solution. For instance, Heimdal®’s NGAV & MDM has improved firewall features and a module that protects against brute-force attacks directed towards improperly secure ports (i.e., RDP port).
- Email security. More than 70% of all ransomware is delivered via email. Always double-check the emails that come from outside of your company’s email list. If you encounter an email that raises suspicions, do not click on any links or open attachments.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security