Contents:
Summary
The European Union is experiencing a surge in brute-force cyberattacks on corporate and institutional networks, mostly originating from Russia, according to a Heimdal investigation.
These attackers exploit Microsoft infrastructure, particularly in Belgium and the Netherlands, to avoid detection.
Heimdal’s data reveals that the attacks date back to May 2024, but evidence suggests they may have been occurring for an even longer period.
This aligns with European leaders’ belief that Russia is waging a ‘shadow war’ to unsettle Europe.
At the NATO summit in July, leaders claimed Russia was behind cyberattacks, disinformation, sabotage, and other disruptive actions.
Danish Prime Minister Mette Frederiksen stated, “Russia is trying to destabilize all of us, using various measures.”
She urged that countries “take it more seriously.”
The investigation into the Russian brute-force campaign has revealed several critical insights:
- Attackers are aiming for High-Value Targets (HVTs)
- Key infrastructure cities like Edinburgh and Dublin have been frequently targeted
- Over half of the attack IP addresses are linked to Moscow, targeting major cities in the UK, Denmark, Hungary, and Lithuania
- The rest of the investigated attack IPs can be traced back to Amsterdam and Brussels
- Major ISPs like Telefonica LLC and IPX-FZCO were significantly abused
The EU has published a report that supports our findings about telecommunications and electricity sector being in danger and identifies supply chain vulnerabilities, particularly in 5G networks and renewable energy infrastructure. The report goes into great detail about the risks and offers advice on how to stay safe.
Russian Brute-Force Attacks – Singularly or prelude?
EU’s recent risk evaluation on highlights significant vulnerabilities and stresses the urgent need for enhanced security measures.
Given the surge in Russian brute-force attacks uncovered by Heimdal, this report underscores the necessity for robust defenses.
It calls for coordinated efforts among EU member states to protect critical infrastructure, implement advanced cybersecurity protocols, and foster international cooperation to counteract state-sponsored cyber threat.
Furthermore, in a broader context, these brute-force attacks may be seen as preliminary moves in a larger, more significant operation, on the Russian side.
The map below illustrates the primary origin of the attack.
Heimdal’s data shows these attacks date back to May 2024 but may have been happening even longer.
Prevalent Infiltration and Attack Techniques.
The attackers primarily target administrative accounts using various case combinations and language variants.
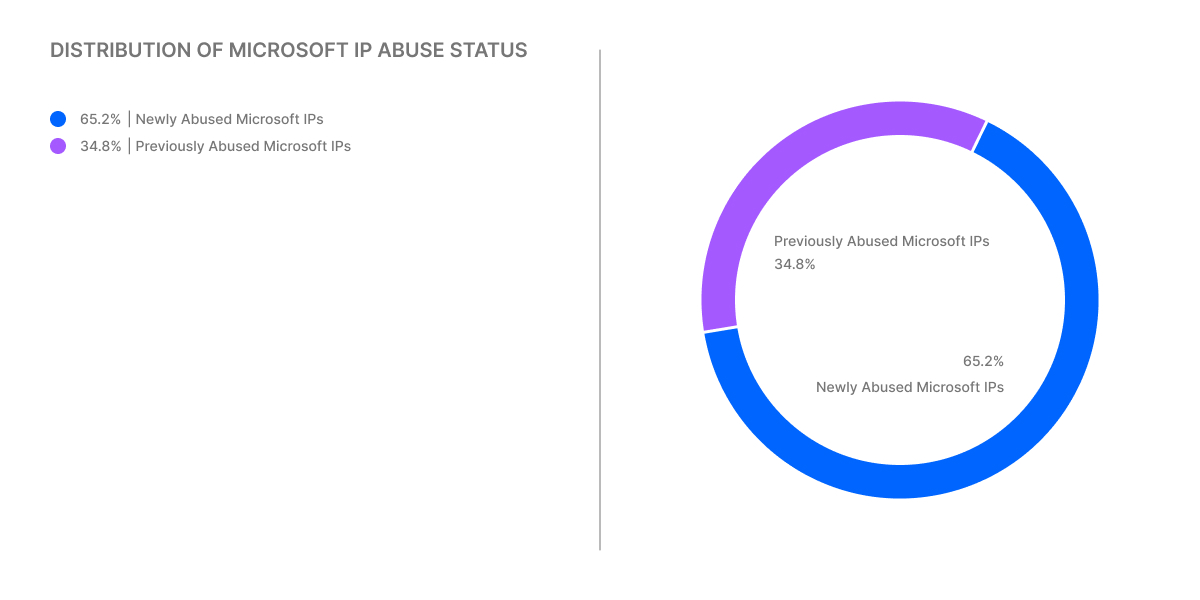
Over 60% of attack IPs are new, with approximately 65% recently compromised and the rest previously abused, revealing a constantly evolving threat.
The threat actors employ known attack principles such as SMBv1 crawlers, RDP crawlers, and RDP alternative port crawlers, exploiting weak or default credentials through password guessing, spraying, and stuffing.
Additionally, their use of legitimate Microsoft infrastructure broadens the attack surface and complicates detection and response.
Data shows that attackers have actively exploited Microsoft infrastructure from the Netherlands and Belgium to increase their attack range and success odds.
Russia Leveraging State-Owned Networks to Propagate Attack
Major ISPs like Telefonica LLC and IPX-FZCO are significantly abused, with the former accounting for 27.7% of attacks from Russia.
The attackers also leveraged resources from Russian allies, including Indian telecom companies Bharat Sanchar Nigam Limited and Bharti Airtel Limited, both of which have faced recent data breaches.
Scope of Brute-Force Campaign
Russia’s motivation behind these cyberattacks is multifaceted.
The reasons for these actions likely include aims to destabilize and disrupt critical infrastructure in Europe, extract sensitive data, gain financial advantage to fuel ongoing cyber-war efforts, or deploy malware.
The threat actors’ mandates can span multiple types of subversive cyber-warfare ops, including seek-and-destroy, disruption of critical assets, and sabotage.
A Wake Up Call for the European Union
This persistent threat underscores the need for cybersecurity measures within EU countries, including strengthening cloud security, enforcing multi-factor authentication, conducting regular security audits, and educating employees.
Morten Kjaersgaard, founder of Heimdal, said:
This data shows that an entity in Russia is waging a hybrid war on Europe, and may have even infiltrated it.
The threat actors are aiming to extract as much data or financial means as possible, leveraging Microsoft infrastructure to do so.
Whoever is responsible, whether it’s the state or another nefarious group, they have no shame in using Russia’s allies to commit these crimes.
The exploitation of Indian infrastructure is a strong example. The data also proves these attackers have strong ties with China.
Paul Vixie, co-founder of SIE Europe, added:
The data that Heimdal has uncovered is explosively evil, and SIE Europe data clearly shows how well built these Russian Wasp nests are and they show no signs of stopping.
SIE Europe does not ever traffic in Personally Identifiable Information, and this case shows the investigative power of public information once cooperatively assembled.
Full Report
The European Union is currently grappling with a substantial increase in cyberattacks primarily originating from Russia.
These brute-force attacks, targeting corporate and institutional networks, are exploiting Microsoft’s infrastructure in Belgium and the Netherlands to remain undetected.
Data from Heimdal indicates that over half of the attack IP addresses are linked to Moscow, while others trace back to Amsterdam and Brussels.
Since May 2024, these attacks have targeted non-administrative accounts to facilitate lateral movement within networks.
The attackers, using compromised IPs, employ methods such as password guessing and exploiting weak credentials.
The involvement of major ISPs and the use of resources, predominantly from Indian telecom companies further complicate the cybersecurity landscape, underscoring the need for robust defenses and international cooperation.
Methodology
Heimdal collected data for the Russian brute-force attack campaign using its advanced Threat-Hunting & Action Center, which offers comprehensive monitoring and analysis capabilities.
The platform leverages the Extended Threat Protection (XTP) engine integrated with Heimdal’s Next-Generation Antivirus, Firewall, and Mobile Device Management (MDM) products for real-time threat detection and deeper insights into attack patterns.
Heimdal’s data is strengthened and made trustworthy by incorporating reputable external sources such as SHODAN, Cloudflare, Censys, and SIE Europe probing.
This multi-source approach ensures a robust, multi-faceted view of threat activity, enhancing the accuracy and reliability of the findings.
The use of advanced threat-hunting techniques and continuous monitoring allows Heimdal to identify both known and emerging threats effectively.
Russia’s Cyber-Warfare Tactics Against the EU
Russia has launched a sophisticated cyber-warfare campaign against the European Union, employing brute-force attacks on corporate and institutional networks.
These attacks exploit Microsoft infrastructure in Belgium and the Netherlands to avoid detection and target non-administrative accounts for lateral movement within networks.
Circa 65% of the attack IPs linked to Microsoft were recently compromised, while the rest have been abused in the past for similar activities.
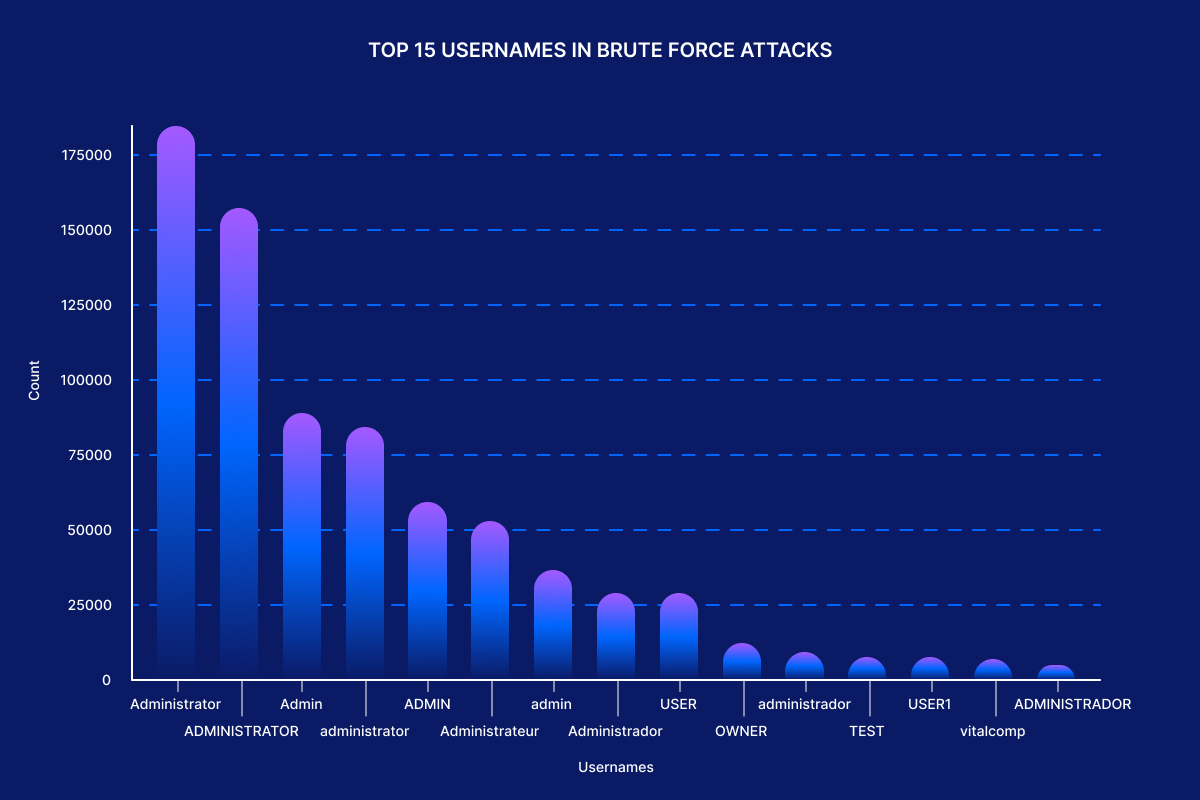
The brute-force attacks predominantly target variations of administrative usernames like “Administrator” and “ADMINISTRATOR,” with counts exceeding 175,000, alongside common non-admin names such as “USER” and “TEST.”
Please refer to the graph below for additional information on targeted account names.
By leveraging these combinations, the threat actors aim to increase the likelihood of finding accounts with weak or unchanged passwords.
This strategy maximizes their chances of gaining unauthorized access to systems quickly and efficiently.
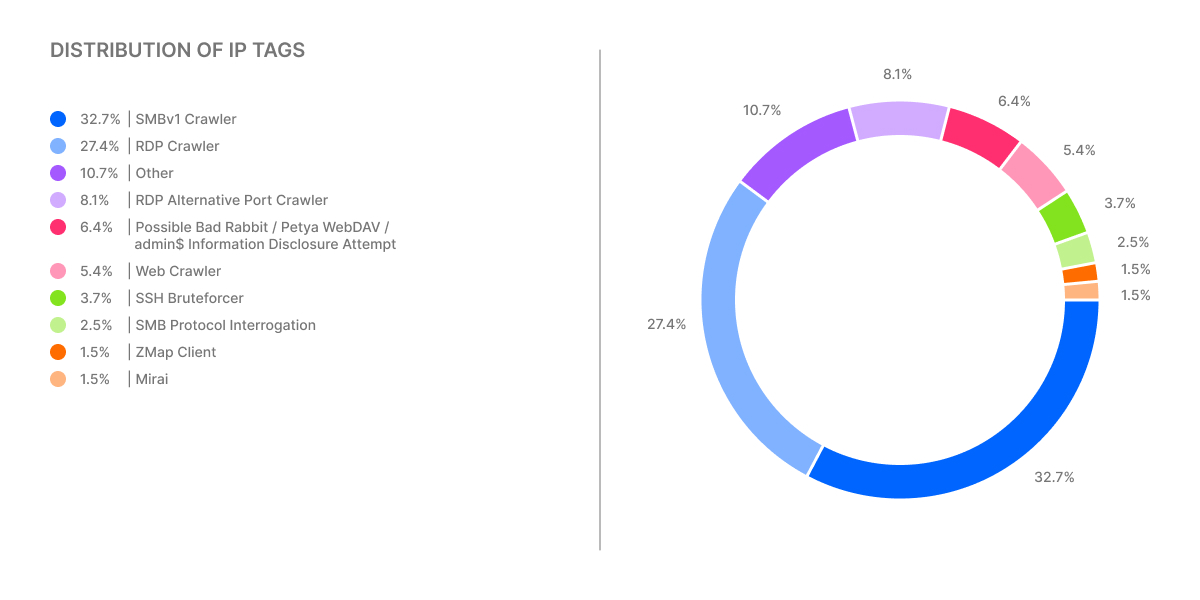
Heimdal intelligence shows that the top three brute-force attack techniques used by Russian threat actors are SMBv1 Crawler, RDP Crawler, and RDP Alt Port Crawler.
The SMBv1 Crawler is responsible for 32.4% of attacks, utilizing methods such as password guessing, password spraying, credential stuffing, and exploiting default or weak credentials.
The RDP Crawler, accounting for 27.4% of attacks, also uses password guessing, password spraying, credential stuffing, and exploiting default or weak credentials.
The RDP Alt Port Crawler, used in 8.1% of attacks, involves port scanning and guessing, port scanning and spraying, port scanning and stuffing, and exploiting default or weak credentials on non-standard ports.
The analysis indicates that 55% of the most used attack IPs originate from Moscow, with significant portions traced back to Amsterdam and Brussels.
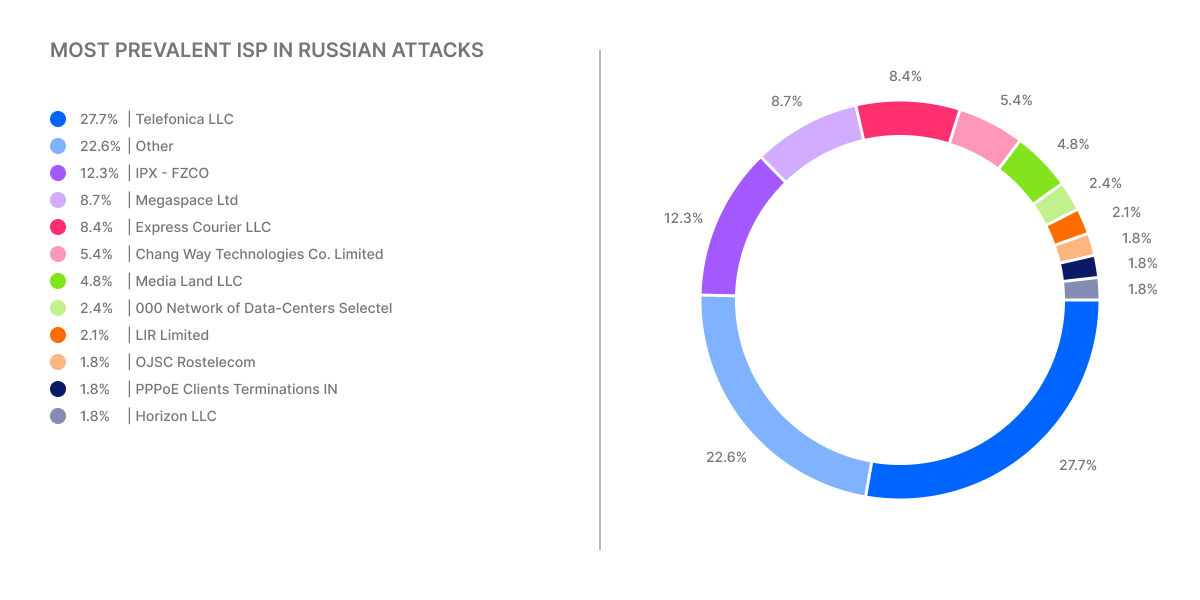
For brute-brute force dissemination thereat actors prevalently used ISPs such as Telefonica LLC (27.7%) and IPX – FZCO (12.3%). Other notable instances are Megaspace Ltd (8.7%) and Express Courier LLC (8.4%).
The full list of ISPs involved in the Russian brute-force campaign has been captured in the graph below.
Key cities targeted include Edinburgh and Dublin, which are home to critical infrastructure and tech hubs, and Budapest and Törökbálint. Major cities in the UK, Denmark, Hungary, and Lithuania are also frequently targeted.
The reasons for these actions likely include aims to destabilize and disrupt critical infrastructure in Europe, extract sensitive data, gain financial advantage, or malware deployment.
The threat actors’ mandates can span multiple types of subversive cyber-warfare ops, including seek-and-destroy, disruption of critical assets, and sabotage.
Recent examples of similar tactics include the 2023 SolarWinds attack, where allegedly Russia-backed hackers infiltrated multiple U.S. government agencies, and the 2024 cyberattacks on Ukrainian critical infrastructure, which caused extensive disruption.
On Russia’s involvement in the recently detected brute-force campaign, Morten Kjaersgaard, chairman and founder of Heimdal commented
This data shows that an entity in Russia is waging a hybrid war on Europe, and may have even infiltrated it.
The threat actors are aiming to extract as much data or financial means as possible, leveraging Microsoft infrastructure to do so.
Whoever is responsible, whether it’s the state or another nefarious group, they have no shame in using Russia’s allies to commit these crimes.
The exploitation of Indian infrastructure is a strong example. The data also proves these attackers have strong ties with China.
Leveraging Indian and Chinese Resources to Fuel On-going European Cyber-Assault
Despite maintaining diplomatic relations with Russia, both China and India are acutely aware of ongoing cyberattacks from Russian threat actors.
This section explores the methods and implications of these attacks, highlighting the involvement of Indian and Chinese resources in facilitating Russia’s cyber-warfare against the European Union.
India has experienced a staggering number of cyberattacks, with 39 malicious campaigns reported in Q2 2023 alone.
These attacks include brute-force attempts conducted from Russia.
Throughout the recent brute-force campaign, Russian cyber actors have notably leveraged resources from Indian telecom companies Bharat Sanchar Nigam Limited (BSNL) and Bharti Airtel Limited, using them against EU HVTs (i.e., High Value Targets).
Both companies have faced significant data breaches, compromising their infrastructure and data.
Bharat Sanchar Nigam Limited (BSNL) has suffered two major data breaches, the latest in late May, where 278 GB of sensitive data was leaked, including IMSI numbers, SIM card information, DP card data, and server snapshots.
Bharti Airtel Limited, despite the company’s denial, has had reports suggesting that personal identifiable information (PII) of 375 million Airtel customers was found on a dark web auction website.
China was similarly targeted by brute-force attacks from Russia.
Heimdal data shows that many of the IPs used in the attack against EU targets can be traced to Hong Kong or in proximity to the city.
China’s unwillingly involvement in the Russian underground cyber-warfare effort is intimately tied to also Fancy Bear (APT28).
This group has been conducting large-scale brute-force attacks targeting various VPN services, SSH services, and web application authentication interfaces globally.
Despite close ties, both China and India have become involuntary resources for Russian cyber-warfare efforts targeting the European Union.
Russian threat actors have abused the compromised infrastructure of Indian telecom companies and Chinese infrastructure to set the stage for the brute-force campaign on the EU.
This highlights the complex and far-reaching nature of Russia’s cyber campaigns and underscores the necessity for enhanced cybersecurity measures.
TTPs Used by Russian Threat Actors in EU Attacks
According to Heimdal’s intel, these are the attack techniques used throughout the EU.
SMBv1 Crawler
Usage: Employed in 32.4% of attacks
Sub-techniques:
- T1110.001: Password Guessing – Attackers attempt common passwords.
- T1110.003: Password Spraying – Attackers try one password against many usernames.
- T1110.004: Credential Stuffing – Using previously breached credentials.
- T1078: Valid Accounts – Exploiting default or weak credentials.
RDP Crawler
Usage: Employed in 27.4% of attacks.
Sub-techniques:
- T1110.001: Password Guessing – Attackers attempt common passwords.
- T1110.003: Password Spraying – Attackers try one password against many usernames.
- T1110.004: Credential Stuffing – Using previously breached credentials.
- T1078: Valid Accounts – Exploiting default or weak credentials.
RDP Alt Port Crawler
Usage: Employed in 8.1% of attacks
Sub-techniques:
- T1046: Network Service Scanning – Port scanning to find open ports.
- T1110.001: Password Guessing – Attempting common passwords on discovered ports.
- T1110.003: Password Spraying – Trying one password against many usernames on discovered ports.
- T1110.004: Credential Stuffing – Using breached credentials on discovered ports.
- T1078: Valid Accounts – Exploiting default or weak credentials on non-standard ports.
Web Crawler
Usage: employed in 6.4% of attacks
Sub-Techniques:
- T1595: Active Scanning – Automated scanning of web pages to discover and index content.
- T1596: Search Open Websites/Domains – Gathering information from public-facing websites to find security weaknesses.
Possible Bad Rabbit/Petya
Usage: employed in 3.7% of attacks.
Sub-techniques:
- T1486: Data Encrypted for Impact – Encrypting data to make it unavailable to the target.
- T1059.003: Command and Scripting Interpreter: Windows Command Shell – Executing malicious scripts and commands to spread ransomware.
WebDAV/admin$ Information Disclosure Attempts
Usage: employed in 2.5% of attacks.
Sub-Techniques:
- T1003.002: OS Credential Dumping: Security Account Manager – Extracting credentials from the system to access sensitive information.
- T1071.001: Application Layer Protocol: Web Protocols – Using web protocols to communicate with compromised systems.
SSH Bruteforcer
Usage: employed in 1.5% of attacks.
Sub-Techniques:
- T1110.001: Brute Force: Password Guessing – Attempting common passwords for SSH access.
- T1110.003: Brute Force: Password Spraying – Trying one password across multiple accounts.
SMB Protocol Interrogation
Usage: employed in 1.5% of attacks.
Sub-Techniques:
- T1046: Network Service Scanning – Scanning and interrogating SMB services to find vulnerabilities.
- T1592.002: Gather Victim Host Information: Hardware – Collecting information about the hardware configuration of a victim’s system.
ZMap Client
Usage: employed in 1.5% of attacks. High-speed internet-wide network scanning to identify open ports and vulnerable services.
Sub-Techniques:
- T1595.002: Active Scanning: Scanning IP Blocks – Performing rapid scanning of internet IP addresses to identify open ports.
- T1046: Network Service Scanning – Identifying services running on open ports.
Mirai
Usage: Botnet primarily targeting IoT devices to create networks of compromised devices for large-scale attacks.
Sub- Techniques:
- T1090.002: Proxy: External Proxy – Using compromised devices to proxy traffic for hiding malicious activity.
- T1566.002: Phishing: Spearphishing Link – Using phishing emails to compromise devices.
Other(s)
Usage: employed in 10.7% of attacks.
Usage: A collective category for various scanning activities not specifically categorized.
Sub-techniques: a variety of techniques used by the other attack groups.
Insights
- High Usage of Common Techniques.
Russian cyber actors heavily rely on common password-related techniques, such as those used by SMBv1 and RDP Crawlers.
This emphasizes the urgent need for robust password management and heightened security awareness among EU organizations.
Implementing strong, unique passwords and frequent updates is crucial in mitigating these attacks.
- Credential Reuse.
The prevalent use of credential stuffing across various crawler types highlights the significant risk posed by data breaches.
This underscores the importance of unique passwords for different accounts to prevent attackers from leveraging previously compromised credentials to gain unauthorized access.
- Weak Initial Security.
The frequent exploitation of default or weak credentials points to widespread issues with initial security configurations.
This underlines the necessity for stringent security policies from the outset, including ensuring that all default passwords are changed and implementing comprehensive security protocols.
- Port Scanning and Exploitation.
The focus of the RDP Alt Port Crawler on scanning and exploiting non-standard ports suggests that Russian attackers are thorough in their infiltration efforts.
This indicates that EU organizations need to monitor and secure all network ports, not just the commonly used ones, to protect against these sophisticated scanning techniques.
Regular network audits and advanced intrusion detection systems are essential to mitigate these threats.
Distribution of Brute-Force Attacks
Subsequent queries provided by SHODAN pinpoint these attacks to Moscow and its outskirts.
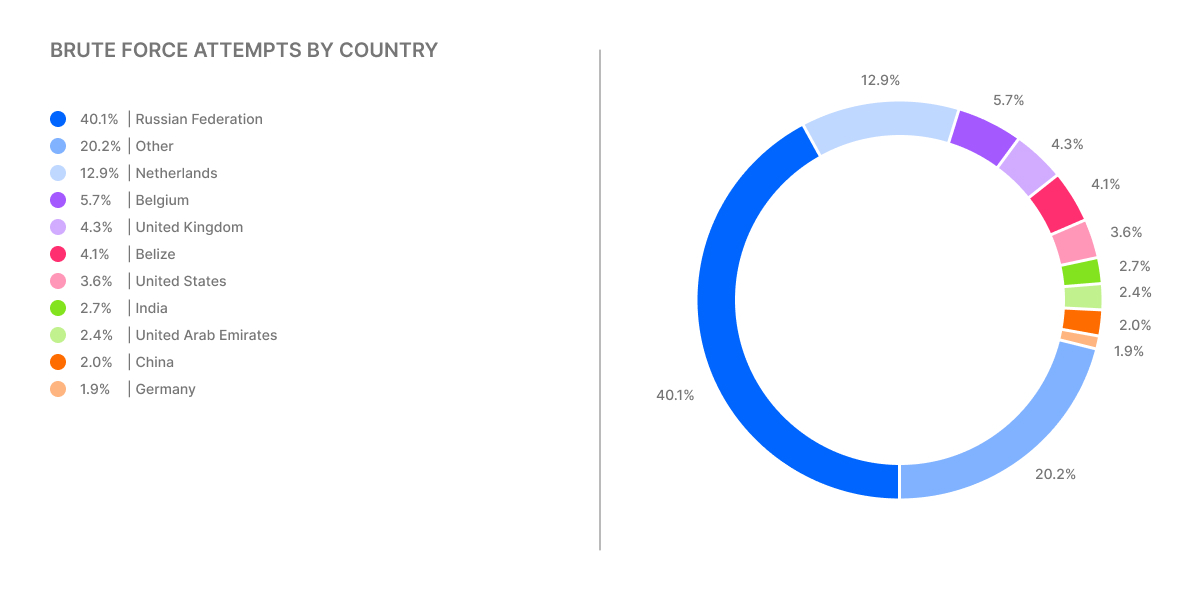
The data indicates that 40.1% of brute-force attacks originate from the Russian Federation, with significant contributions from the Netherlands (12.9%) and Belgium (5.7%).
Other notable sources include the United Kingdom (4.3%), Belize (4.1%), and several countries collectively accounting for the remaining 20.2%.
The complete information on brute-force attack distribution has been captured in the graph below.
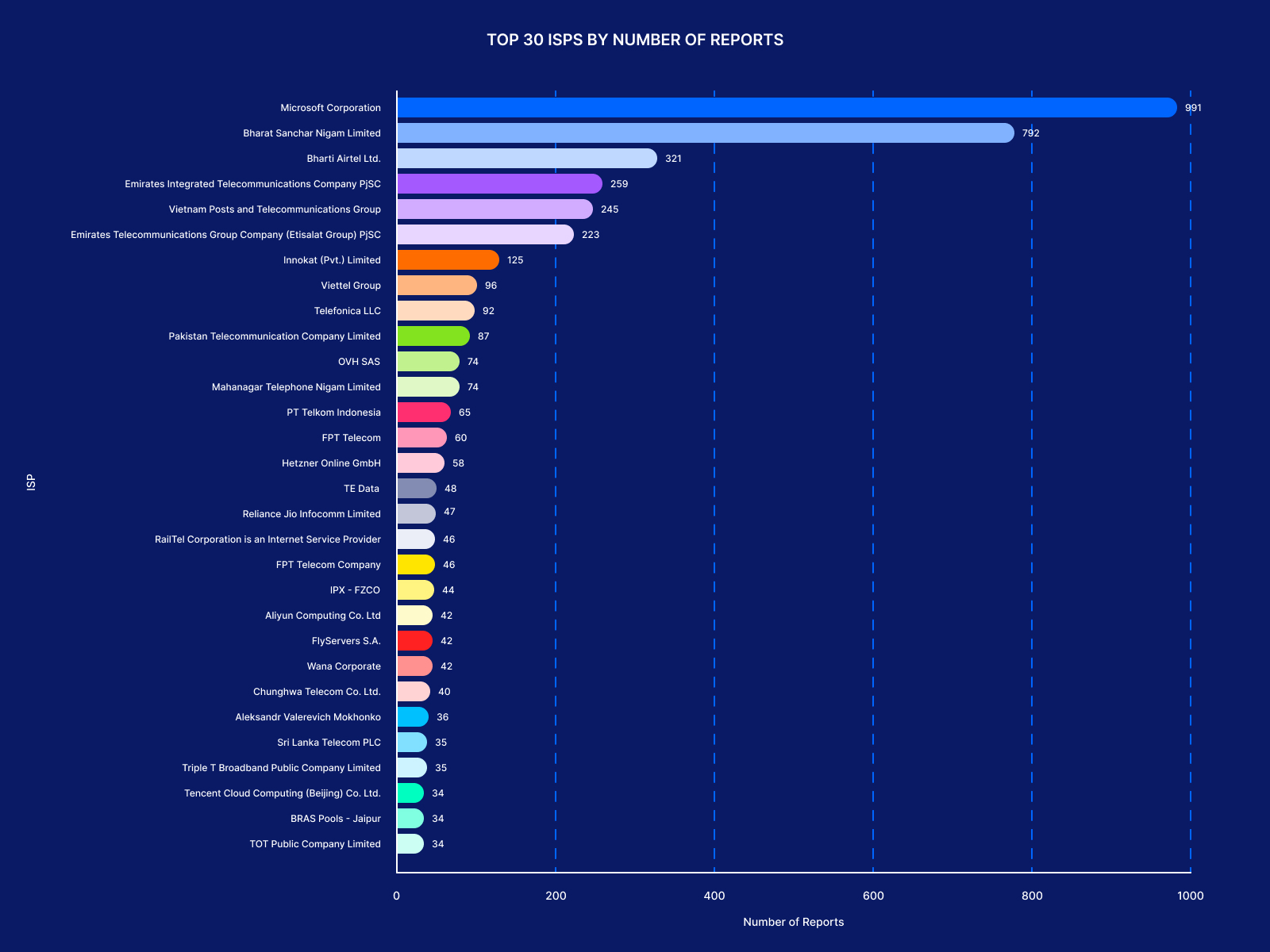
The chart below highlights that brute force attacks involve a wide range of ISPs from around the world.
Microsoft Corporation and Indian ISPs (Bharat Sanchar Nigam Limited and Bharti Airtel Ltd.) are the top most abused ISPs, with significant activity also observed from ISPs in the UAE, Vietnam, Russia, and Pakistan.
Reach out for comments, Paul Vixie of SIE Europe, issued the following statement:
The data that Heimdal has uncovered is explosively evil, and SIE Europe data clearly shows how well built these Russian Wasp nests are and they show no signs of stopping.
SIE Europe does not ever traffic in Personally Identifiable Information, and this case shows the investigative power of public information once cooperatively assembled.
SIE Europe is a non-profit organization that empowers its members to identify, map, and protect against cybercrime by facilitating the contribution and sharing of real-time passive DNS data.
Mapping Brute-Force Attack Aggressors Against Target Cities
A significant portion of brute-force attacks targeting corporate and institutional networks in Western Europe originate from Moscow, with additional activity traced to Amsterdam and Brussels.
These attacks are aimed at EU countries, indicating a coordinated and potentially state-sponsored effort.
Evidence
- Attack Origins. 55% of the most used attack IPs are from Moscow, with the rest from Amsterdam and Brussels.
- Targeted Cities. 44% of the attacks focused on major cities in the United Kingdom, such as Dublin, Edinburgh and London.
- IP Analysis. Specific IP addresses linked to these attacks include:
- 91.240.118.73 targeting Haslev, Denmark.
- 194.26.135.68 targeting Edinburgh, UK.
- 185.234.216.136 targeting Dublin, UK.
- 176.111.174.60 targeting Törökbálint, Hungary.
- 176.111.174.34 targeting Budapest, Hungary.
- ISP Information. The IPs are often associated with Chang Way Technologies Co. Limited, a known entity for hosting data centers and web services and have been blacklisted for malicious activities.
Impact
- Compromised Assets. Targeted assets include key infrastructure in the cities, such as traffic management systems, SCADA systems, and major tech company headquarters.
- Strategic Importance. The attacks focus on locations with significant military, economic, and cyber-defense importance, such as the EU Cyber Security Centre in Edinburgh and tech hubs in Dublin.
- Persistent Threats. The repeated use of certain IPs and the targeting of high-value assets suggest a persistent and evolving threat aimed at disrupting and compromising critical systems and infrastructure in EU countries.
Russia Actively Exploiting Microsoft IPs for EU Brute-Force Attacks
The analysis indicates that Russia-based threat actors are leveraging compromised and newly abused IPs, particularly those associated with Microsoft infrastructure, to conduct widespread brute-force attacks on strategically important targets in the EU region.
This coordinated effort underscores the need for enhanced cybersecurity measures, robust monitoring, and international cooperation to mitigate the risks posed by such sophisticated cyber threats.
For additional information, please refer to Appendix 1.
Protective Measures
-
Strengthen Cloud Security
- Implement advanced security features in cloud services.
- Regularly update and patch cloud infrastructure.
-
Enforce Multi-Factor Authentication (MFA)
-
Conduct Regular Security Audits
-
Cybersecurity training.
-
Implement Network Segmentation.
- Isolate critical systems from the rest of the network.
- Use firewalls and access control lists to restrict unauthorized access.
-
Enhance Detection and Response Capabilities.
- Deploy intrusion detection and prevention systems (IDPS).
- Utilize Security Information and Event Management (SIEM) solutions for real-time monitoring.
-
Strengthen Password Policies
- Enforce strong, unique passwords and regular password changes.
- Implement account lockout mechanisms after multiple failed login attempts.
-
Limit Access to Critical Systems.
- Restrict access to critical infrastructure to authorized personnel only.
- Regularly review and update access permissions.
-
Monitor External Traffic.
- Use geolocation-based filtering to block traffic from high-risk regions.
- Analyze and log incoming IP addresses to detect patterns indicative of brute-force attacks.
-
Use Threat Intelligence.
- Subscribe to threat intelligence feeds to stay informed about emerging threats.
- Share and receive information with other organizations to enhance collective defense.
-
Regularly Backup Critical Data.
- Ensure regular backups of critical systems and data.
- Store backups in secure, isolated environments to prevent tampering.
Conclusion
The recent spike in brute-force attacks across Western Europe, primarily originating from Moscow, highlights a major cybersecurity threat from Russia-based actors.
These attackers exploit Microsoft and EU infrastructure in Belgium and the Netherlands to evade detection and target non-admin accounts for lateral movement within networks.
To counter this, EU countries need to enhance cloud security, enforce multi-factor authentication, conduct regular security audits, and educate employees.
A proactive approach and international cooperation are essential to mitigate these sophisticated cyber threats.
Appendix 1
Heimdal’s telemetry yielded that 55% of the top 9 most used attack IPs originate from Moscow, the others being tracked to Amsterdam or Brussels. Our statistical sample reveals that the aggressors have specifically targeted destinations that are part of the European Union.
Furthermore, 44% of the attacks targeted major cities in the United Kingdom such as Dublin, Edinburgh and London.
The complete information can be found in the table below.
| No. | Aggressor’s IP | Aggressor City | Target City | Target Country | Attack count |
|---|---|---|---|---|---|
| 1 | 91.240.118.73 | Moscow | Haslev | Denmark | 120 |
| 2 | 194.26.135.68 | Moscow | Edinburgh | United Kingdom | 200 |
| 3 | 185.234.216.136 | Moscow | Dublin | United Kingdom | 180 |
| 4 | 176.111.174.60 | Moscow | Törökbálint | Hungary | 80 |
| 5 | 176.111.174.34 | Moscow | Budapest | Hungary | 75 |
| 6 | 31.43.185.3 | Amsterdam | Sindal | Denmark | |
| 7 | 80.66.76.121 | Amsterdam | London | United Kingdom | 150 |
| 8 | 80.66.76.121 | Amsterdam | Vilnius | Lithuania | 65 |
| 9 | 194.165.16.72 | Brussels | Brighouse | United Kingdom | 140 |
Breakdown of attack IPs by City of Origin
In this section, we are going to focus on the first attack IPs on the list as they synthesize all of the information necessary to debunk the brute-force campaign.
The last four are variations on the first five entries included in this table.
91.240.118.73
According to SHODAN’s analysis, the first IP on the list (91.240.118.73) can be tracked down to Moscow.
IPSHU pinpoints it to the city’s Central Federal District.
This type of IP is generally used for data centers, web hosting, or transit purposes.
However, its Company/T1 flag suggests that this type of IP could also be employed by companies that rely on high-speed internet connections.
Additional information
- ISP: Chang Way Technologies Co. Limited (ASN: AS57523).
- Preferred OS: Windows (build 10.0.14393).
- Preferred communication ports: 135, 445, 3389, and 5985.
- Domain name: changway.hk.
Analysis
Further investigation into the aggressor’s IP has revealed that the Chang Way Technologies Co. Limited IP may be a redirect.
According to SpeedGuide.com, the IP originates in Hong Kong, more specifically in the Aberdeen Upper Reservoir area.
What’s even more intriguing is the fact that the same IP has two separate entries on Spamhaus’ international IP and domain blacklist:
- 91.240.118.73 is blacklisted! –> [sbl-xbl.spamhaus.org].
- 91.240.118.73 is blocked –> [pbl.spamhaus.org].
Additional intel provided by AbuseIPD suggests that the same IP has been used to carry out illicit port scanning, brute-force, hacking, and similar activities since 2022.
The latest verified reports from users laietania.net and Kimax show that the IP in question has been used to stage out highly aggressive RDP brute-force attacks.
The first attack IP has been reported over 5,000 times, with a confidence of abuse score of 32%.
Targeted Assets
The first IP on the list targeted the Danish city of Haslev. The city itself does not host key military infrastructure or vital economic assets.
194.26.135.68
The second attacking IP (194.26.135.68) can be tracked to Moscow.
SHODAN and SpeedGuide.com assessments point to the fact that this IP is not a bounce like in the first case.
According to the latter source, the location appears to be the Muscovite district of Yakimanka.
Similarly to the first case, this IP appears to be used by data centers, web hosting, or for transit purposes.
The Company/T1 flag also harbors a distinct possibility that the IP might be used by a company.
Additional information
- ISP: Chang Way Technologies Co. Limited (ASN: AS57523).
- Preferred OS: Windows (build 10.0.14393).
- Preferred communication ports: 135, 445, 3389, and 5985.
- Domain name: megaspacenet.com.
Analysis
The IP in question has two entries on Spamhaus’ international IP and domain blacklist:
- 194.26.135.68 is blacklisted! –> [sbl-xbl.spamhaus.org].
- 194.26.135.68 is blocked –> [pbl.spamhaus.org].
AbuseIPD reveals that this IP has been used to conduct various malicious actions such as IDS admin, brute-force storm over port 3389, RDP local account slowly brute-force attempts, and highly aggressive brute-force attempts.
The log goes back to November 2023.
The latest verified reports from the users laietania.net and Kimax show that this IP has been used to stage out highly aggressive and slow-paced RDP brute-force attacks.
The second IP has been reported over 100 times, with a confidence of abuse score of 24%.
Targeted Assets
The second IP targeted Edinburgh. Threat actors might seek to compromise the following vital assets.
EU Cyber Security Centre
The UK hosts several EU cyber defense initiatives, including contributions to the EU Cyber Security Centre, which provides 24/7 defense. This center is involved in real-time information sharing, training, and expertise for Allies and partner nations.
185.234.216.136
The third attacking IP (185.234.216.136) can be tracked to Moscow. SHODAN and SpeedGuide.com assessments converge to the same conclusion. There’s no information available about the attacker’s precise location. This IP is used by data centers, web hosting, or for transit purposes.
Additional information
- ISP: Chang Way Technologies Co. Limited (ASN: AS57523).
- Preferred OS: N/A.
- Preferred communication ports: 135, 445, 3389.
- Domain name: expcourier.ru.
Analysis
This IP has two Spamhaus blacklist entries :
- 185.234.216.136 is blacklisted! –> [sbl-xbl.spamhaus.org].
- 185.234.216.136 is blocked –> [pbl.spamhaus.org].
AbuseIPD shows that this IP has been used for malicious actions such as RDP local account slow, brute-force attempts over port 3389, and highly aggressive brute-force attempts. The log goes back to April 2023.
The latest reports from the users abusiveIntelligence and Kimax show that this IP has been used to stage out RDP brute-force attacks over RDP. This IP has been reported over 100 times, with a confidence of abuse score of 19%.
Targeted Assets
Dublin, the UK city targeted by the third attack IP is home to a host of vital military, economic, and technical assets.
Tech Hub
Home to major tech companies’ European HQs (Google, Facebook, Microsoft), making it vital for cybersecurity.
EU Cyber-Intelligence
Shares threat intelligence and best practices throughout the European Union.
176.111.174.60
The fourth attacking IP (176.111.174.60) can be tracked to Moscow according to SHODAN. SpeedGuide.com’s assessment places the IP in the Yakimanka district similar to the second attack IP. This IP is also used by data centers, web hosting, or for transit purposes.
Additional information
- ISP: Chang Way Technologies Co. Limited (ASN: AS57523).
- Preferred OS: Windows Server 2016 Standard 14393.
- Preferred communication ports: 135, 445, 3389, and 5985.
- Domain name: expcourier.ru.
Analysis
This IP has two Spamhaus blacklist entries:
- 176.111.174.60 is blacklisted! –> [sbl-xbl.spamhaus.org]
- 176.111.174.60 is blocked –> [pbl.spamhaus.org]
AbuseIPD shows that this IP has been used for malicious actions such as RDP local account slow, brute-force attempts over port 3389, and highly aggressive brute-force attempts.
The log goes back to October 2023.
The latest reports from the users laietania.net and remote24.se show that this IP has been used to stage out RDP brute-force attacks.
This IP has been reported over 80 times, with a confidence of abuse score of 28%.
Targeted Assets
Törökbálint, the Hungary-based city targeted by the fourth attack IP also has a strong strategic importance. This includes:
EU Cyber-defense
Hungary supports EU’s cyber defense through training and collaborative initiatives.
Proximity to Budapest
Close to the capital, it provides logistical support and benefits from strategic positioning.
176.111.174.34
SHODAN tracks the fifth attacking IP (176.111.174.34) to Moscow according.
SpeedGuide.com’s assessment places the IP in the Yakimanka district.
This IP is also used by data centers, web hosting, or for transit purposes.
There’s a slight discordance between SHODAN and AbuseIPdb evaluation .
While SHODAN attributes 176.111.174.34 to Chang Way Technologies Co. Limited, SpeedGuide states this IP is actually attributed to Express Courier LLC.
This might be a false attribution or a clever obfuscation technique since Express Courier LLC offers services like domestic and international logistics.
Additional information
- ISP: Chang Way Technologies Co. Limited (ASN: AS57523).
- Preferred OS: Windows Server 2016 Standard 14393.
- Preferred communication ports: 22, 135, 137, 139, 445, 3389 and 5985.
- Domain name: expcourier.ru.
Analysis
This IP has two Spamhaus blacklist entries:
- 176.111.174.34 is blacklisted! –> [sbl-xbl.spamhaus.org].
- 176.111.174.34is blocked –> [pbl.spamhaus.org].
AbuseIPD shows that this IP has been used for malicious actions such as RDP local account slow, brute-force attempts over port 3389, and highly aggressive brute-force attempts.
The log goes back to September 2023.
The latest reports from the users laietania.net and abusiveIntelligence show that this IP has been used to stage out brute-force attacks.
This IP has been reported 80 times, with a confidence of abuse score of 18%.
Targeted Assets
Budapest plays a key role in the EU due to its involvement in cyber defense initiatives, its key military logistical hub, and its status as Hungary’s economic center.
EU Cyber Defense
Budapest is involved in EU’s cyber defense efforts through Hungary’s participation in cyber initiatives.
Economic Hub
Budapest is the economic heart of Hungary, with critical financial institutions and commercial enterprises.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security