Contents:
Researchers have unveiled a sophisticated and fast ransomware strain called Rorschach, previously undocumented. Malware experts discovered the new ransomware strain after a cyberattack on a U.S.-based company and described it as having “technically unique features”.
Among the capabilities observed was the encryption speed, which would make Rorschach the fastest ransomware threat on the market.
What makes Rorschach stand out from other ransomware strains is its high level of customization and its technically unique features that have not been seen before in ransomware. In fact, Rorschach is one of the fastest ransomware strains ever observed, in terms of the speed of its encryption.
Analyzing Rorschach
Upon a closer look, Rorschach’s source code shows similarities to Babuk ransomware, which was leaked in September 2021, and LockBit 2.0. Furthermore, the ransom notes sent to victims appear to be inspirations from Yanluowang and DarkSide.
The most significant aspect of the intrusion is the use of a technique called DLL side-loading to load the ransomware payload, which has not been seen before. By sidestepping detection, financially motivated groups are becoming more sophisticated in their approach.
The use of direct syscalls to manipulate files and bypass defense mechanisms is another unique characteristic.
Rorschach appears to have taken some of the ‘best’ features from some of the leading ransomwares leaked online and integrated them all together. In addition to Rorschach’s self-propagating capabilities, this raises the bar for ransom attacks.
Rorschach’s Process
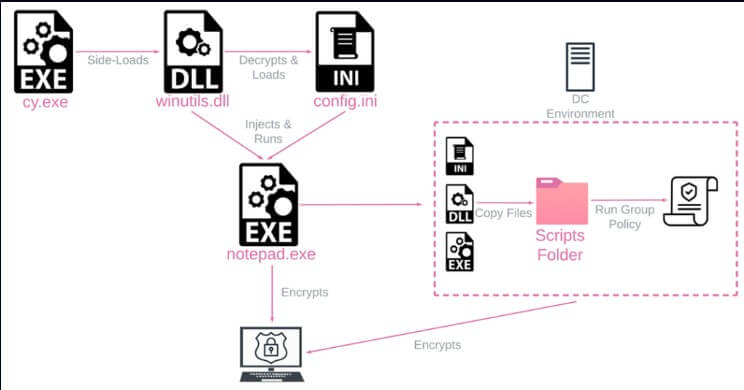
In their report, the analysts describe how they found out that the hackers deployed the malware on the victim network after leveraging a weakness in a threat detection and incident response tool.
Using the Cortex XDR Dump Service Tool (cy.exe) version 7.3.0.16740, the attacker sideloaded the Rorschach loader and injector (winutils.dll), launching the ransomware payload, “config.ini,” into Notepad. A UPX-style anti-analysis protection is provided by the loader file, while the main payload is protected from reverse engineering and detection by virtualizing parts of the code with VMProtect.
Upon execution on a Windows Domain Controller, Rorschach creates a Group Policy that propagates to other hosts. Then, to wipe its traces, the malware erases four event logs (Application, Security, System, and Windows Powershell).
If the victim machine is configured with a language other than the Commonwealth of Independent States (CIS), Rorschach starts encrypting data.
As BleepingComputer points out, combining curve25519 and eSTREAM cipher hc-128, this encryption scheme encrypts files intermittently, allows for higher processing speeds.
According to THN, this process is designed to only encrypt a specific portion of the original file content instead of the entire file and employs additional compiler optimization methods that make it a “speed demon.”
To prove how fast Rorschach’s encryption is, Check Point researchers set up a test with 220,000 files on a 6-core CPU machine. It took Rorschach 4.5 minutes to encrypt the data, whereas LockBit v3.0, considered the fastest ransomware strain, finished in 7 minutes.
Currently, the operators of the Rorschach ransomware are unknown and there is no branding, which is rare among ransomware.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







