Contents:
After a nearly two-month hiatus, the REvil ransomware actor’s dark web servers have mysteriously come back online. At the moment, it is unclear whether the REvil gang started operations again or if law enforcement turned on the servers.
Massive Ransomware Attack Conducted by the REvil Group
In July, we announced that a supply chain vulnerability was successfully exploited by cybercriminals to target thousands of businesses through the initial infected host. The entry point was the Managed Service Provider (MSP) Kaseya VSA, a cloud-based platform that allows its customers to perform patch management and client monitoring.
This led to the most significant ransomware attack in history. The data of 60 customers, plus around 1,500 downstream businesses have been impacted by the attack.
REvil gang initially decided that the price for decrypting all systems would be $70 million in Bitcoin in exchange for the tool that allows all affected businesses to recover their files, but later dropped the price to $50 million.
The REvil Ransomware Group Mysteriously Disappears
The interesting part is that a few days after the attack, the REvil ransomware gang mysteriously disappeared. According to ransomware experts, the attackers’ payment site, the public site, the ‘helpdesk’ chat, and their negotiation portal went offline July 13th at approximately 01:00 AM EST, which is 08:00 AM Moscow time.
Some security experts believe the gang may have shut down their own websites due to internal disagreements or fear related to increased law enforcement attention.
Following the Kaseya attacks, the White House warned that the USA would take action themselves if Russia did not act upon threat actors in their borders.
We still don’t know what really happened with the gang but their decision to disappear certainly impacted the victims who wanted to negotiate in order to receive a decryption key for their encrypted files.
Kaseya Managed to Get a Decryption Key
After the gang’s disappearance, Kaseya declared that it obtained a universal decryptor for the ransomware attack from a “trusted third party” and now is distributing it to the impacted customers.
Security experts believe Russian intelligence obtained the decryption key from the threat actors and sent it to the FBI to show their good intentions.
REvil Ransomware Gang’s Servers Online Again
Both REvil’s Tor ‘Happy Blog’ data leak site and the Tor payment/negotiation site came back online yesterday. According to BleepingComputer, REvil’s latest victim was added to their data leak site on July 8th, 2021, just five days before the gang’s mysterious disappearance.
Unlike the data leak site, which is up and running, the Tor negotiation site does not appear to be fully functional yet, as victims are unable to log in.
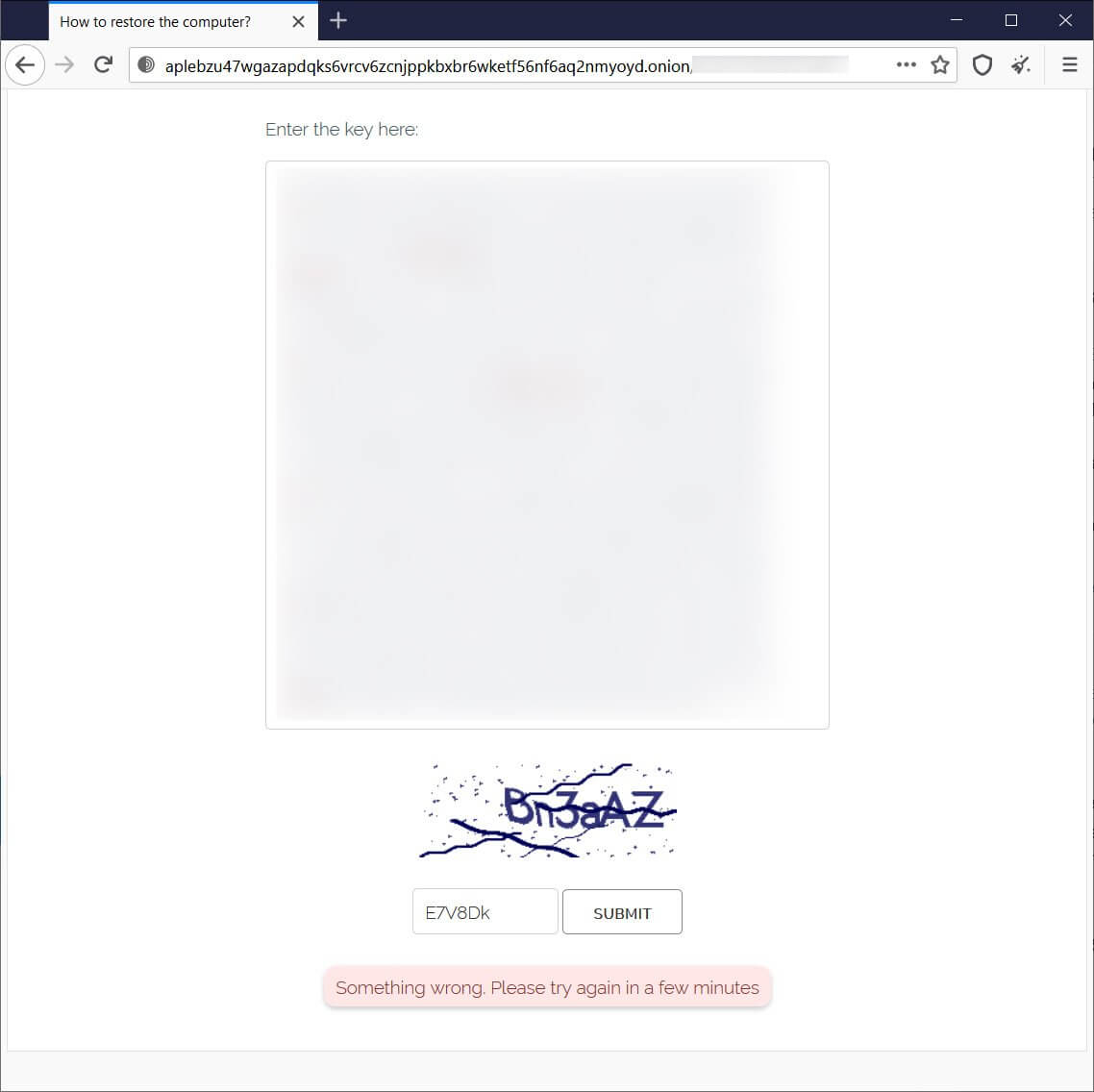
At the time of writing, the REvil’s site decoder[.]re is still offline.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










