Contents:
A fully undetectable PowerShell backdoor disguising itself as part of a Windows update process is being actively used by a threat actor who has targeted at least 69 entities.
Researchers that have uncovered this threat have yet to attribute the chain attacks to a specific threat actor. In a report, Tomer Bar, director of security research at SafeBreach, states that metadata associated with the lure document, specifically a weaponized Microsoft Word document that was uploaded on August 25, 2022, indicates that the initial intrusion vector is a LinkedIn-based spear-phishing attack, which ultimately leads to the execution of a PowerShell script via a piece of embedded macro code.
The Threat in Depth
Initially, the PowerShell backdoor was not seen as malicious until operational mistakes made by the hackers allowed SafeBreach analysts to access and decrypt commands sent to execute on infected devices.
The document contains malicious macros that drop and execute an ‘updater.vbs’ script that creates a scheduled task to impersonate a routine Windows update. The script then executes two PowerShell scripts: Script1.ps1, which is designed to connect to a remote command-and-control (C2) server and retrieve a command to be launched on the compromised machine by means of a second PowerShell script, temp.ps1, which in turn decodes the command, executes it, and then encrypts and uploads the result via a POST request to the C2.
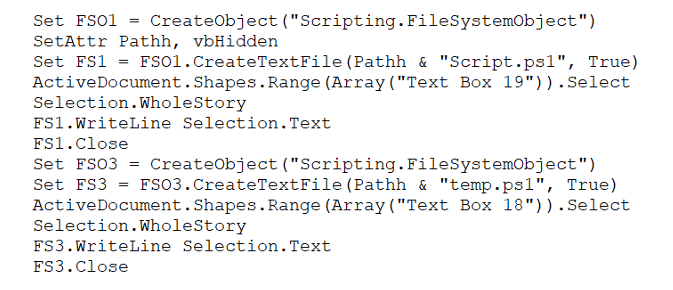
Creation of two PowerShell scripts
According to The Hacker News, some of the notable commands issued consist of exfiltrating the list of running processes, enumerating files in specific folders, launching whoami, and deleting files under the public user folders.
The Dangers of Stealth
Government, corporate, and private user systems are the most common targets when it comes to threat actors engaging in cyberespionage and, as BleepingComputer also points out, this PowerShell backdoor is a very good example of unknown stealthy threats used in such attacks.
The findings coincide with Microsoft taking steps to block Excel 4.0 and Visual Basic for Applications (VBA) macros by default across Office apps, which resulted in threat actors adapting their malware delivery methods.
There are, however, steps that can be followed in order to stay safe from any potential risks. Applying security updates as quickly as possible, limiting remote access to endpoints and following the principle of least privilege, as well as being well informed about any emerging threats are just a few examples that will keep cybercriminals from causing damage.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







