Contents:
Since at least 2019, a massive cyber-espionage operation targeting mainly renewable energy and industrial technology entities has been operational, impacting more than fifteen organizations all over the world.
According to BleepingComputer, security researcher William Thomas was the one to find the cyber spying campaign using OSINT (open-source intelligence) methods such as DNS scans and public sandbox submissions.
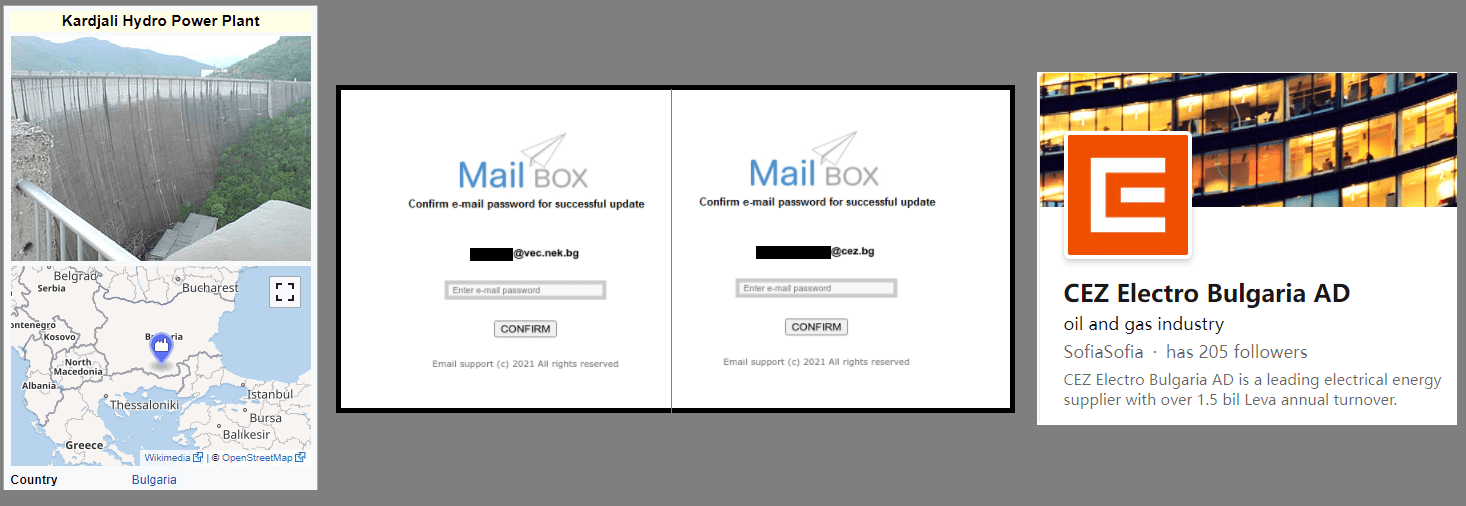
According to his findings, the threat actor employs a custom ‘Mail Box’ toolkit, a basic phishing package installed on the hackers’ infrastructure, and genuine websites that have been hacked to host phishing pages.
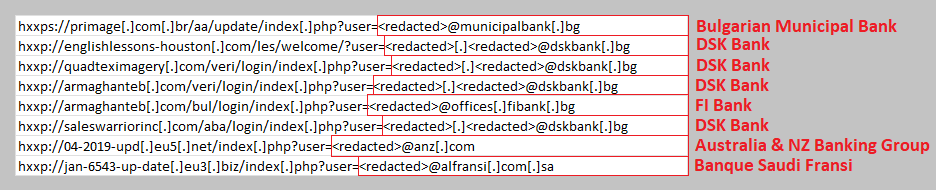
The majority of the phishing pages were hosted on the domains “*.eu3[.]biz,” “*.eu3[.]org,” and “*.eu5[.]net,” while most of the affected websites were situated in Brazil (“*.com[.]br”).
Hackers Focus on Renewable Energy Orgs
The objective of the phishing campaign is to collect login credentials belonging to employees working for renewable energy companies, environmental organizations, and industrial technology in general.
Some of the targeted companies in this campaign include Schneider Electric and Honeywell, Chinese telecommunications giant Huawei, semiconductor manufacturer HiSilicon, Telekom Romania, and US universities such as the University of Wisconsin, California State University, and Utah State University.
The Operation
The security expert was unable to obtain samples of the phishing emails used in the attack, but based on the landing pages, he thinks the emails used a “Your Mail Box storage is full” enticement.
Who Was Behind the Attack?
The researcher couldn’t link this operation to any particular cybercrime organizations, but evidence suggests that there were two clusters of activity, one from APT28 (aka FancyBear) and the other from Konni (hackers from North Korea).
Cybersecurity researchers at Google Threat Analysis Group discovered that:
Since mid-Dec, @Google TAG has detected ongoing APT28 cred phishing campaigns targeting Ukraine. Some IOCs:
consumerpanel.eu3[.]biz
consumerpanel.eu3[.]org
consumerspanelsrv.eu3[.]org
protectpanel.eu3[.]biz
updateservicecenter.blogspot[.]com— billy leonard (@billyleonard) January 14, 2022
As explained by BleepingComputer, one similarity for both hacking groups is that the hostnames used for phishing login information are owned by Zetta Hosting Solutions, a name that has recently appeared in many analyst reports.
According to Thomas, numerous Advanced Persistent Threat (APT) hacking groups employ Zetta in cyberattacks. Nevertheless, he highlighted that nothing indicates the hosting company is deliberately helping these malicious operations.
Zetta is used a lot by APTs and malware, and I’d be very surprised if they didn’t know. They’re not a huge company. Threat actors also like these types of free hostname services where they can setup infrastructure quickly, freely, and anonymously.
Bulgaria, Another Target
The analyst has also discovered a small cluster of activity from 2019 that was connected to the same infrastructure focusing on numerous financial institutions located in Bulgaria.
Thomas thinks that the threat actor is backed financially by companies that have an interest in fossil fuels, especially someone selling energy to Bulgaria, and considers renewable energy a threat.
This is another reason why cybersecurity solutions for Energy and Utility providers are becoming more important in todays security landscape.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








