Contents:
Threat actors are targeting exposed Remote Desktop services to encrypt windows devices using the new Venus Ransomware. Venus Ransomware began operating in the middle of August 2022 and has been used to encrypt victims’ machines since then.
The threat actors gained access to a victim’s corporate network through the Windows Remote Desktop protocol.
How Venus Ransomware Works?
The ransomware attempts to terminate thirty-nine processes linked with database servers and Microsoft Office applications when executed. After that, it will also delete event logs Shadow Copy Volumes, and disable Data Execution Prevention.
The ransomware will add the.venus extension to encrypted files, as demonstrated below. For instance, test.jpg would be renamed test.jpg after being encrypted. Venus.
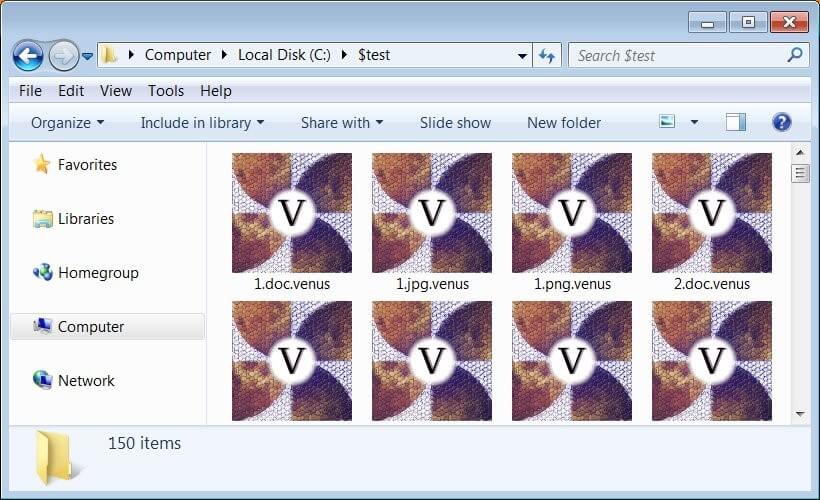
Files encrypted by the Venus Ransomware (Source)
The ransomware will append a “goodgamer” filemarker and other data to the end of each encrypted file. At this point, it is unknown what this further data entails.
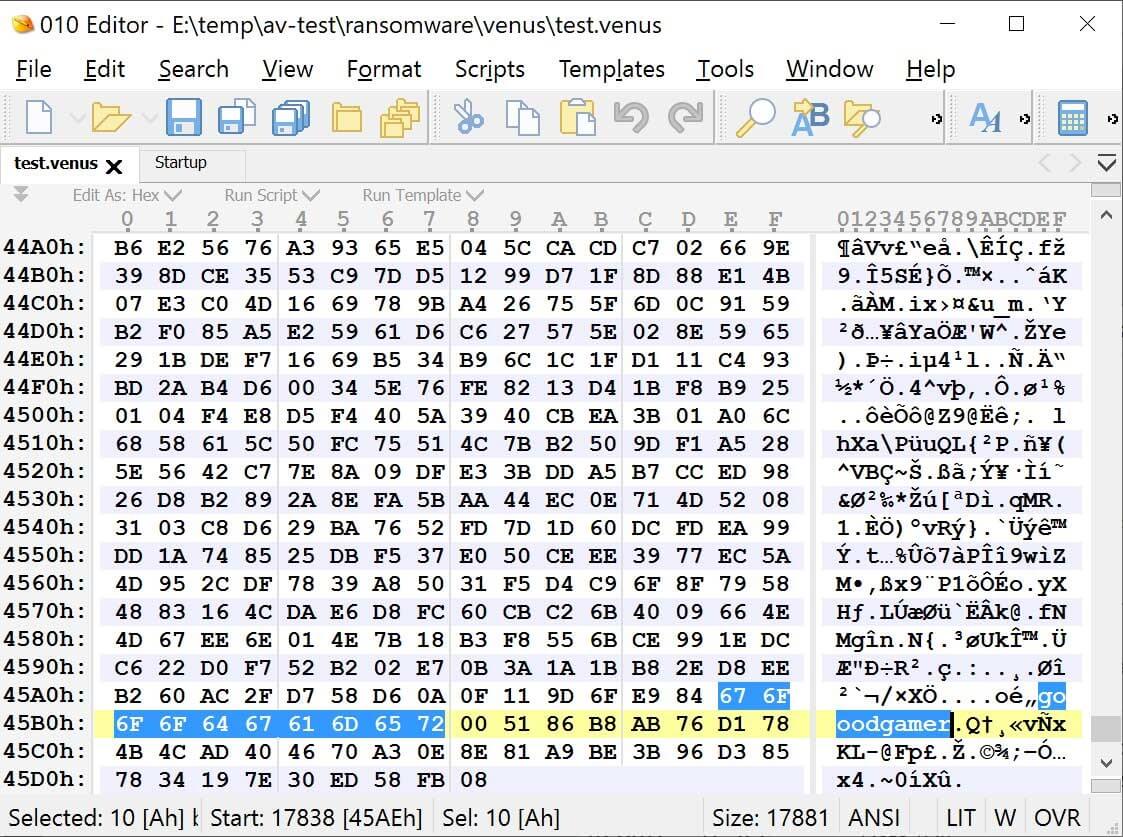
Goodgamer file marker in an encrypted file (Source)
After these operations are completed, the ransomware will create an HTA ransom note in the %Temp% folder, which will be displayed automatically when the ransomware finishes the encryption process of the data on the device. The ransomware calls itself “Venus” in the ransomware letter and shares a TOX and email address, which can be used to contact the attacker and negotiate a ransom payment. A base64 encoded blob, which is probably the encrypted decryption key, can be found at the end of the ransom note.
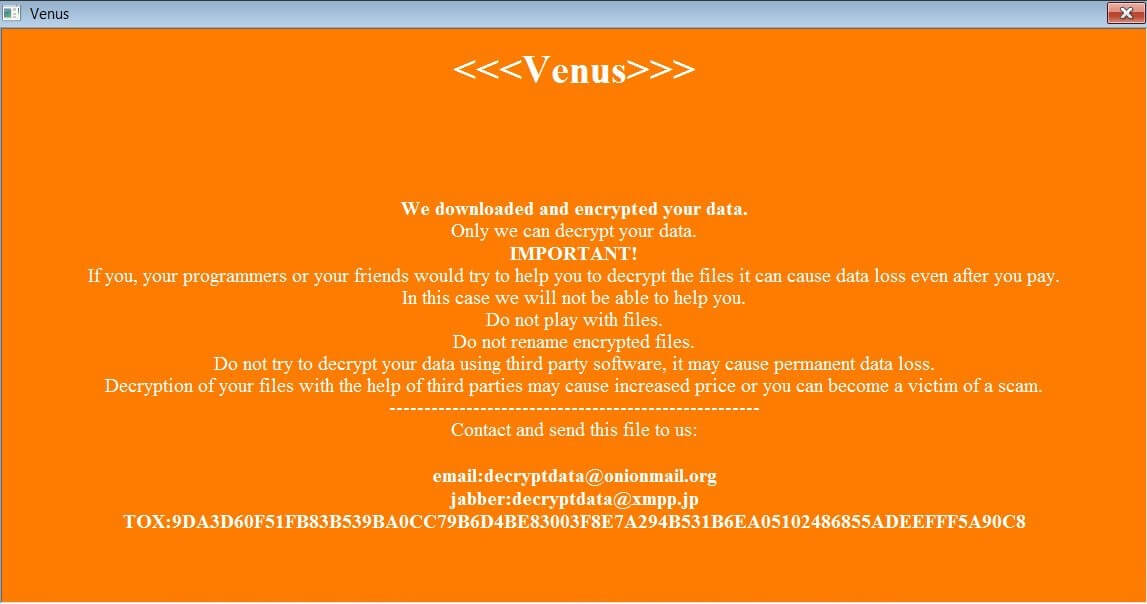
Venus Ransomware note (Source)
According to BleepingComputer, the Venus ransomware is fairly active, with new submissions uploaded to ID Ransomware daily. It is essential to hide these services behind a firewall because the ransomware appears to be targeting publicly exposed Remote Desktop services, even those using irregular TCP ports. No Remote Desktop Services should ideally be openly accessible on the Internet and only available over a VPN.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








